Check Point: Converting Another Vendor's Security Policy to is a SmartMove | Tech Bytes, Check Point: Tech Bytes HD
00:04:30
Обнаружено блокирование рекламы на сайте
Для существования нашего сайта необходим показ рекламы. Просим отнестись с пониманием и добавить сайт в список исключений вашей программы для блокировки рекламы (AdBlock и другие).
Check Point Software Technologies, Ltd. 360 роликов
2383 просмотра на сайте 12n.ru
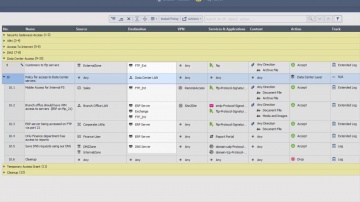
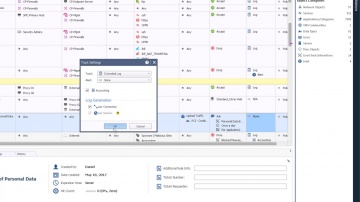
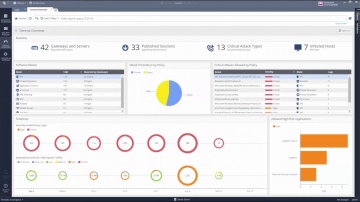
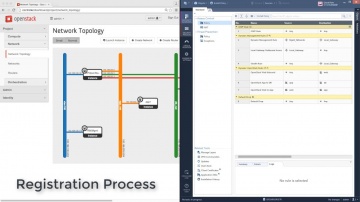
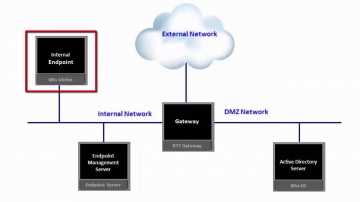
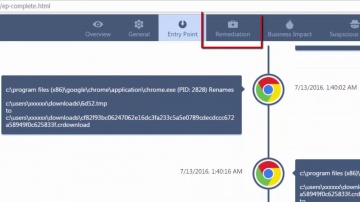
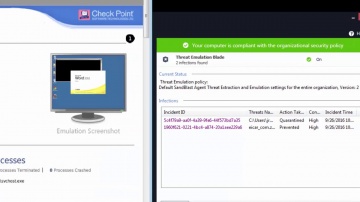
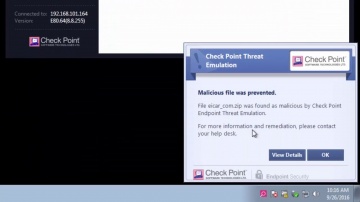
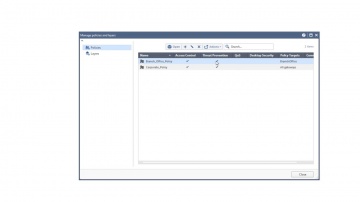
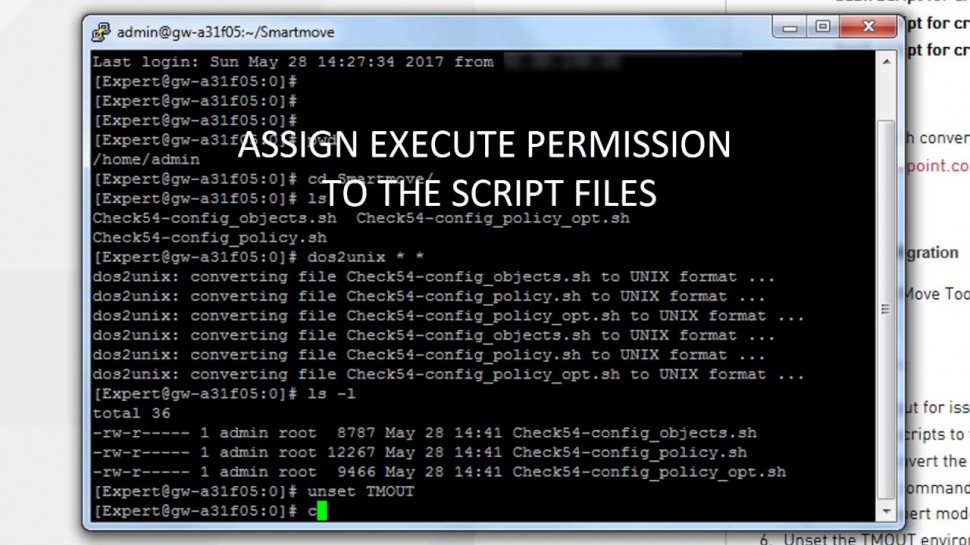
Converting Another Vendor's Security Policy to is a SmartMove | Tech Bytes.
offers migration tools and assistance to migrate your security policy from another vendor to. This video shows how you can use the SmartMove tool to migrate from Cisco to.To learn more about SmartMove in CheckMate visit:
развернуть свернуть