Поиск по тегу «cyber» в разделе Видеокаталог
HD 01:01:07
ДиалогНаука: Современные методы комлексной защиты хранилищ неструктурированных данных - видео
Хранилища неструктурированных данных (файловые сервера, NAS системы, почтовые сервера, контроллеры домена и др.) являются важной составляющий бизнес процессов любой компании. При этом наличие много терабайтных массивов информации влечет за ...
Cмотреть видео
Cмотреть видео
HD 00:12:57
C#: C# + MSSQL | Создаём и подключаем базу данных к Windows Forms | SQL Запросы - видео
Установка Microsoft SQL Server 2019 Express на Windows 10 - SQL Server 2019 - https://www.microsoft.com/en-us/sql-server/sql-server-downloads SQL Server Management Studio (SSMS) - https://docs.microsoft.com/ru-ru/sql/ssms/download... Vis...
Cмотреть видео
Cмотреть видео
HD 00:06:26
BIRCHPUNK - RUSSIA TOMORROW NEWS // РОССИЯ ЗАВТРА: НОВОСТИ
Говорят, отечественная робототехника безнадежно отстала от мировой. Чушь! Мы заглянем на завод Ижевск Дайнемикс, где делают роботов, побываем в Ижевске и Уссурийске, послушаем противника роботизации Виталия Наливкина. ///// They say tha...
Cмотреть видео
Cмотреть видео
HD 00:50:07
ДиалогНаука: ВЕБИНАР: CYMULATE BAS. СИМУЛЯЦИЯ АТАК И ВЗЛОМОВ ПО ВСЕЙ ЦЕПОЧКЕ KILL CHAIN
Вебинар посвящен проблематике оценки защищенности и эффективности СЗИ, симуляции нацеленных атак на основе "конструктора" и платформе Cymulate BAS для симуляции подобных атак и взломов.
Cмотреть видео
Cмотреть видео
HD 00:08:24
Check Point: Lightboard Series: Dynamic Revisions
This video elaborates on the logic behind the R80.10 Security Management architecture focusing on the dynamic revisions feature. This feature automatically stores the full history of database changes, with very little footprint, consuming ...
Cмотреть видео
Cмотреть видео
HD 00:02:38
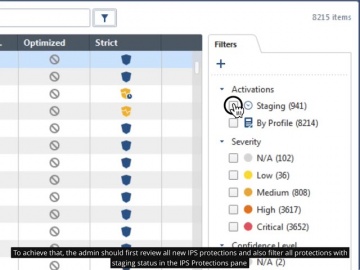
Check Point: R80.10 Policy Management – IPS Protections in Detect (Staging) State
This video elaborates on the logic behind new IPS protections status after IPS update operation and introduces best practice on changing the status of detect-staging on prevent when enough information was gathered regarding the new IPS prot...
Cмотреть видео
Cмотреть видео
HD 00:01:38
Check Point: CloudGuard SaaS Demo Series: Identity Protection for Office 365
Watch this short demonstration video to learn how CloudGuard SaaS, an industry-first software-as-a-service (SaaS) security solution, provides advanced security and identity protection including account takeover protection for SaaS applicat...
Cмотреть видео
Cмотреть видео
00:04:43
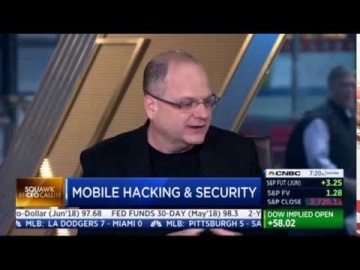
Check Point: Founder & CEO Gil Shwed on CNBC Squawk Box
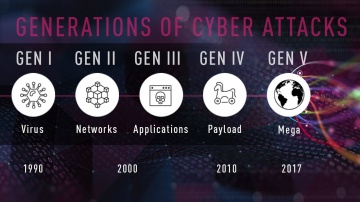
CNBC Squawk Box featured Check Point CEO & Founder Gil Shwed. Gil Shwed discusses 5th generation cyber attacks. For more https://www.checkpoint.com/gen-v-cybe...Talking about level three attacks, level four attacks; what are fifth and s...
Cмотреть видео
Cмотреть видео
HD 00:30:26
Check Point: Who's Responsible for your Cloud Security?
A full breakdown of what is shared responsibility and the layers of security needed to protect you from security breaches in the cloud. For more information:
Cмотреть видео
Cмотреть видео
HD 00:29:43
Check Point: The Mobile Threat Landscape
From Judy to Blueborne, the proliferation of mobile threats has grown rapidly in the past year. In this session, we review the various types of mobile threats, how they spread and the damage they cause. We will also be providing practical ...
Cмотреть видео
Cмотреть видео
HD 00:28:57
Check Point: Best of CheckMates: My Top CLI Commands
This presentation will highlight the most useful CLI commands submitted via CheckMates by real users just like you!+ For more information: Use cases, examples and case studies will be presented for the top CLI commands from the CheckMate...
Cмотреть видео
Cмотреть видео
HD 00:22:22
Check Point: Building a Secure Platform as CIO - CPX 360 Keynote
In his keynote, Sharon Schusheim will discuss what it takes to build and operate a secure platform as a CIO. For more information: CPX 360 promises to be the premier cyber security summit. For the first time, we will bring our customers...
Cмотреть видео
Cмотреть видео
HD 00:22:53
Check Point: Gen V Cyber Security with Moti Sagey - CPX 360
In his keynote, Moti Sagey will discuss in a pragmatic fact based way what it takes to build a Gen V security solution and how the cyber landscape matches the must have for effective security.
Cмотреть видео
Cмотреть видео
HD 00:06:53
Check Point: Top Cloud Cyber Security Challenges in 2018
Head of Product Marketing, Data Center and Cloud, Don Mayer, discusses some of the top cyber security challenges organizations face with the cloud in 2018. He dives into the amount of cyber attacks or cyber threats targeting the cloud and e...
Cмотреть видео
Cмотреть видео
HD 00:08:37
Check Point: 2018 Cyber Security - 5TH GENERATION CYBER ATTACKS
The 5th Generation of Cyber Attacks is here, is your Cyber Security ready in 2018? Darrell Burkey, Director of IPS Products interviews with WADK-AM in Newport/ Providence areas in Rhode Island on Gen V cyber security. Visit - to learn more ...
Cмотреть видео
Cмотреть видео
HD 00:05:12
Check Point: Deployment Tools; DIY security appliance images using ISOmorphic
Deployment Tools; DIY security appliance images using ISOmorphic. For more information: In our second video on deployment tools we show you how to image Security Appliances and Open Servers. With the ISOmorphic utility you can inst...
Cмотреть видео
Cмотреть видео
HD 00:27:48
Check Point: New Cyber Security Technologies and Cyber Threat Solutions
is your partner against cyber-crime. This is realized on a daily basis by thousands of customers worldwide using the most advanced cyber security technologies. More information: These technologies are part of Infinity’s cyber security a...
Cмотреть видео
Cмотреть видео
HD 00:20:42
Check Point: Microsoft Azure and CloudGuard - Intelligent Cloud Security - CPX 360 2018
In his keynote, Avi Ben Menahem, Director of Azure Security Microsoft will discuss what it takes to build and operate a secure cloud platform, the approach the team at Microsoft takes to secure Azure, and the importance of a strong develope...
Cмотреть видео
Cмотреть видео
HD 00:22:56
Check Point: Internet of Things: The Dangers of IoT - CPX 360 2018
The concept of Internet of Things (IoT) truly represents a radical shift in how companies will operate, governments will govern and individuals will live their lives. Micro compute technologies and autonomous systems will permeate our day-t...
Cмотреть видео
Cмотреть видео
HD 00:18:01
Check Point: How to Hack a Smartphone - Demo with Pablo Perez CPX 360
Ever wanted to know how to hack a smartphone? Join this exciting live demo to see first-hand how easy it is. For more information visit In this session, Michael Shaulov will demonstrate a live hacking of a smartphone. After the demonstrat...
Cмотреть видео
Cмотреть видео
HD 00:34:55
Check Point: Gil Shwed Keynote: Stepping Up to Gen V of Cyber Security
Gil Shwed's keynote from CPX 2018 on the future of Cyber Security. Find out what Gen V Cyber Attacks are and how you can prevent the next Cyber Attack. For more information visit -
Cмотреть видео
Cмотреть видео
HD 00:19:41
Check Point: Information Security : Gioacchino Buscemi (CPX 360)
In this session, Gioacchino Buscemi, Network Security Officer, European Space Agency. will share his vision on modern IT, among others the importance of compliance and security and how they are very different. Additionally, he will review ...
Cмотреть видео
Cмотреть видео
HD 00:05:18
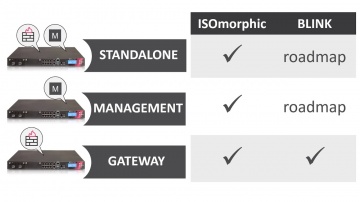
Check Point: Deployment Tools - ISOmorphic & Blink
Deploying Next Generation Firewalls just got easier with the introduction of the Blink utility. For more information: Blink creates a working snapshot of a cleanly installed security gateway with a completed First-Time Configuration Wizard...
Cмотреть видео
Cмотреть видео
HD 00:05:08
Check Point: Advanced Cloud Security - CloudGuard Overview
For more information visit on advanced cloud security solutions visit, Discover CloudGuard, 's advanced cloud security solution. The cloud enables business benefits like agile computing and elastic scalability, but also introduces new clou...
Cмотреть видео
Cмотреть видео
HD 00:50:38
Check Point: Advanced Cyber Security for 2018 | Introducing 3 New products: Step into Gen-V of Cyber
For more information: is happy to welcome the 5th Generation of Cyber Security with 3 exciting new offerings: Infinity Total Protection (ITP), CloudGuard, and Smart-1 Security Management Appliances. • Infinity Total Protection is a gam...
Cмотреть видео
Cмотреть видео
HD 00:02:22
Check Point: Malware Protection 2018 - Public Health Service Prevents, Not Just Detects, Advanced Th
For more information: Malware Protection in 2018 is about prevention not just detection. As a leading West Coast provider of emergency health services, this Public Health Service organization has over two million patients and runs over...
Cмотреть видео
Cмотреть видео
HD 00:02:19
Check Point: The Mississippi Secretary of State & CTO Prevents Ransomware
For more information visit Seeking to modernize its security infrastructure, the Mississippi Secretary of State upgraded to SandBlast and now prevents ransomware attacks and enjoys a peace of mind.
Cмотреть видео
Cмотреть видео
HD 00:06:01
Check Point: Advanced Cyber Security for 2018 - Cyber Security Demo
This video is a technical demonstration of what the cyber security architecture of the future is all about. For more information visit: Infinity is the first consolidated cyber security across networks, cloud and mobile. Unlike other so...
Cмотреть видео
Cмотреть видео
HD 00:01:56
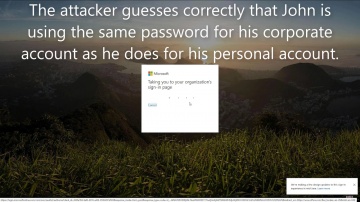
Check Point: Defeats Mobile Cyberattacks
Advanced cybercrimes aren’t science fiction; they’re real – and have real consequences. is at the forefront of mobile security, ensuring that devices and data everywhere remain safe. We don’t just build cutting edge technology: we stand be...
Cмотреть видео
Cмотреть видео
HD 00:02:10
Check Point: SandBlast Mobile: Protecting Against Malicious Apps
Our mobile devices are used for both personal and business purposes. Installing new apps may compromise both your private and corporate data. Every year, malicious apps downloaded from official app stores infect millions of mobile devices....
Cмотреть видео
Cмотреть видео