Поиск по тегу «cyber» в разделе Видеокаталог
HD 00:02:57
Check Point: vSEC for VMware NSXで実現するSoftware-Defined Datacenter (SDDC)による高度なセキュリティ
チェック・ポイントのvSEC for VMware NSX は、VMware NSX と連携し、SDDCにおけるすべてのトラフィックを高度な脅威から防御する動的なオーケストレーションを実現します。 製品情報はこちらhttp://www.checkpoint.co.jp/products/vsec-vmware-nsx/index.html
Cмотреть видео
Cмотреть видео
HD 00:01:41
Check Point: Viking Horde: A New Type of Android Malware on Google Play | Mobile Security
Blog: More information: The research team uncovered a new Android malware campaign on Google Play it calls Viking Horde. Viking Horde conducts ad fraud, but can also be used for other attack purposes such as DDoS attacks, spam messages...
Cмотреть видео
Cмотреть видео
HD 00:02:47
Check Point: ã»âÎÙÄ_Ä_â±Ä â£Ä_â¡ÄÈÄÁÄÄâÈÄ_âü¬»à_¤¼ÄÔ_¨¥ã¬ø
2016_«3¾ÏöÛÄÔÄ_â¢ÄÇÄöÄÄÄÄöÄøÄ_âøâ_øCEOÇâöâÜÄÑÄ_Ä¢Ä_âáĤÄ_Ü¥ÓÈâÕÉÂÐÜÑ_ÑÙÛâÒÁâä¨Ü¥ÓȤøÛÄÔÄ_â¢ÄÇÄö__¨üÈ_µÇø_Ñ_ÇЪ_Ûã_ܨÄâ_Ä_ÄöÇ_ã_...
Cмотреть видео
Cмотреть видео
HD 00:02:22
Check Point: Customer Success: Community Newspaper Group (CNG)
Watch as Infrastructure Manager, Michael Brine discusses his experience with SandBlast Agent in this customer success video. Community Newspaper Group's seventeen newspapers provide readers with the latest in local news, sports, and ente...
Cмотреть видео
Cмотреть видео
HD 00:02:29
Check Point: Customer Success: Community Newspaper Group (CNG)
For More Information: Community Newspaper Groups seventeen newspapers provide readers with the latest in local news, sports, and entertainment in Perth, Australia. As a publishing outlet, its critical for Community Newspaper Group to kee...
Cмотреть видео
Cмотреть видео
HD 00:02:43
Check Point: Introduces Next-Generation Threat Prevention Appliances | Advanced Threat Prevention
Introducing the next-generation of appliances designed to unleash the full power of advanced threat prevention security for businesses of all sizes. For more information visit: Gen V Cyber Security is here: Infinity is the first conso...
Cмотреть видео
Cмотреть видео
HD 00:04:02
Check Point: SideStepper: Anatomy of an iOS Vulnerability | Mobile Threat Prevention
For more information, visit: Report: IDC Technology Spotlight: Why Comprehensive Security Requires Mobile Threat Prevention: disclosed details about SideStepper, a vulnerability that can be used to install malicious enterprise apps o...
Cмотреть видео
Cмотреть видео
HD 00:01:10
Check Point: RSA 2016: Prevent Cyberattacks from Entering the Endpoint with SandBlast Agent
More information:
Cмотреть видео
Cмотреть видео
HD 00:01:18
Check Point: RSA 2016: Mobile Threat Prevention | Mobile Security
For more information visit:
Cмотреть видео
Cмотреть видео
HD 00:01:46
Check Point: RSA 2016: Day 1 - Software
For more information visit: An overview of RSA 2016, Day 1 with Software.
Cмотреть видео
Cмотреть видео
HD 00:00:49
Check Point: RSA 2016: Receives "Recommended" Rating in NSS Next Generation Firewall Test
More Information: NSS Labs, Inc. released their results for the 2016 Generation Firewall Test. In their independent assessment of the security effectiveness and value, NSS once again recognized with the "Recommended" rating. This marks t...
Cмотреть видео
Cмотреть видео
HD 00:05:29
Check Point: Next Generation Firewall, How To Choose The Right One | Network Security
What questions should you ask when choosing the right network security protection in an integrated next generation firewall platform? For more information: provides customers of all sizes with the latest data and network security protect...
Cмотреть видео
Cмотреть видео
HD 00:03:59
Check Point: Threat Emulation Explained by | Advanced Threat Prevention
's Threat new Threat Emulation Software Blade prevents infections from undiscovered exploits, zero-day and targeted attacks. For more information: 's Threat new Threat Emulation Software Blade prevents infections from undiscovered exploit...
Cмотреть видео
Cмотреть видео
HD 00:03:59
Check Point: Threat Emulation Explained by | Advanced Threat Prevention
's Threat new Threat Emulation Software Blade prevents infections from undiscovered exploits, zero-day and targeted attacks. For more information: 's Threat new Threat Emulation Software Blade prevents infections from undiscovered exploit...
Cмотреть видео
Cмотреть видео
HD 00:04:23
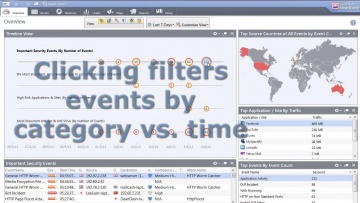
Check Point: SmartEvent | Security Management Walk-Through
Are you tired of managing security by manually searching through millions of logs to find the information you need? There is a better way! Watch this SmartEvent Video to learn how to manage your security more efficiently. For more informa...
Cмотреть видео
Cмотреть видео
00:02:14
КРОК: Москва 24.«Утро»
В столице стартует первый индивидуальный чемпионат среди хакеров. В нем любой желающий сможет совершенно законно взломать информационные системы. Это уникальный для России проект, включающий индивидуальный хакерский тур, аналогов которому в...
Cмотреть видео
Cмотреть видео
HD 00:00:45
КРОК: C^2:Cyber Challenge
C^2: Cyber Challenge — уникальный проект по информационной безопасности Турнир сильнейших хакеров страны и успешные решения для бизнеса на одной площадке. Сразись с сильнейшими white-hat хакерами России в игре Cyber Readiness Challenge (CRC...
Cмотреть видео
Cмотреть видео
00:05:34
Check Point: Software commente les dernières tendances de la sécurité informatique en 2010
I Télé Les Echos de l'Eco David Darmon, Directeur General France de Software Technologies, lun des leaders mondiaux de la sécurité informatique, explique les tendances de la sécurité informatique en 2010 au vu des récents événements Inter...
Cмотреть видео
Cмотреть видео