Check Point: 2018 Cyber Security - 5TH GENERATION CYBER ATTACKS HD
Для существования нашего сайта необходим показ рекламы. Просим отнестись с пониманием и добавить сайт в список исключений вашей программы для блокировки рекламы (AdBlock и другие).
Check Point Software Technologies, Ltd. 360 роликов
2018 Cyber Security - 5TH GENERATION CYBER ATTACKS.
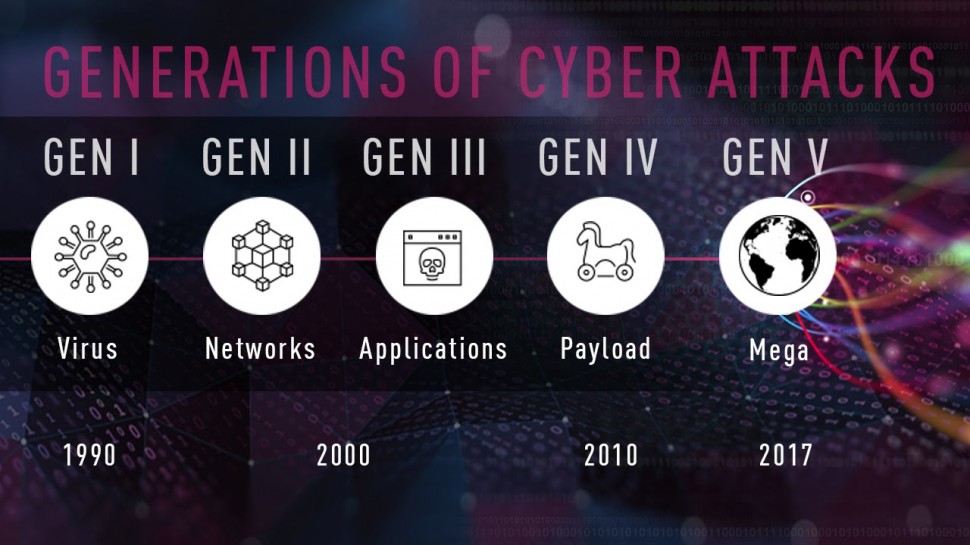
The 5th Generation of Cyber Attacks is here, is your Cyber Security ready in 2018? Darrell Burkey, Director of IPS Products interviews with WADK-AM in Newport/ Providence areas in Rhode Island on Gen V cyber security. Visit — to learn more about Generations of Cyber Attacks.Types of cyber attacks discussed in the video:Generation I: Hackers were typically clever pranksters. Virus attacks on stand-alone PCs began mostly as annoyances or mistakes. To halt disruption, anti-virus products were developed.Generation II: Firewalls, anti-virus, and intrusion detection system (IDS) products were proving to be insufficient in the face of exploits. This sparked the era of best-of-breed patchwork security models, as businesses scrambled to protect themselves.Generation III: Attackers began to analyze networks and software to find and exploit vulnerabilities throughout the IT infrastructure. Firewalls, anti-virus, and intrusion detection system (IDS) products were proving to be insufficient in the face of exploits. This sparked the era of best-of-breed patchwork security models as businesses scrambled to protect themselves. began focusing on prevention and launched intrusion prevention systems (IPS) products.
Generation IV: Cyberattacks reached a new level of sophistication, ranging from international espionage to massive breaches of personal information to large-scale internet disruption. Attacks were hidden in everything from resumes to picture files—evasive and polymorphic. While internet security of the 2nd and 3rd generations provided access control and inspected all traffic, it was incapable of validating actual end-user content received in email, through file downloads and more. In response, introduced anti-bot and sandboxing products to address previously unknown and zero-day attacks.Generation V: Advanced ‘weapons-grade’ hacking tools are leaked, allowing attackers to move fast and infect large numbers of businesses and entities across huge swaths of geographic regions. Large-scale, multi-vector mega attacks spark a need for integrated and unified security structures. Prior generations of patchwork, best-of-breed, detect-first technologies are no match for the rapid and stealthy attacks of the fifth generation. develops a unified architecture with advanced threat prevention solutions that shares threat intelligence in real time, preventing attacks on virtual instances, cloud deployments, endpoints, remote offices, and mobile devices.Please subscribe to our YouTube channel today to learn more about Cyber Attacks, and Threat Prevention.










