Check Point: The Security Zone Ep. 1: Unknown 300 | Enterprise Cyber Security, Check Point: Webinars

00:27:51
Обнаружено блокирование рекламы на сайте
Для существования нашего сайта необходим показ рекламы. Просим отнестись с пониманием и добавить сайт в список исключений вашей программы для блокировки рекламы (AdBlock и другие).
Check Point Software Technologies, Ltd. 360 роликов
1207 просмотров на сайте 12n.ru
The Security Zone Ep. 1: Unknown 300 | Enterprise Cyber Security.
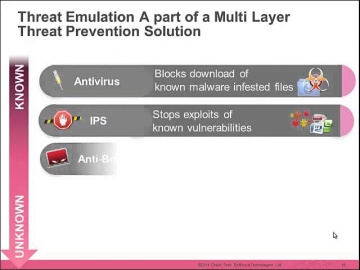
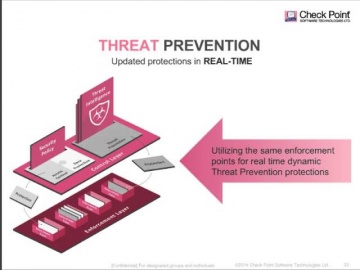
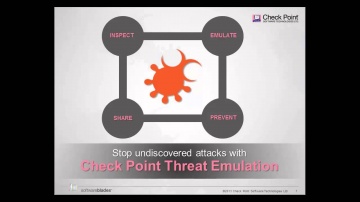
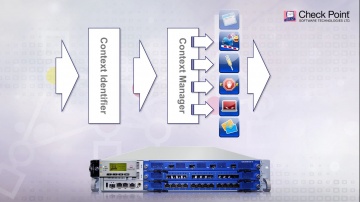
In recent benchmark testing, 300 malicious files were scanned through Threat Emulation and other competitive products. The results found that outperformed all of the others.
развернуть свернуть