Check Point: Threat Emulation Explained by | Advanced Threat Prevention, Check Point: Webinars HD
00:03:59
Обнаружено блокирование рекламы на сайте
Для существования нашего сайта необходим показ рекламы. Просим отнестись с пониманием и добавить сайт в список исключений вашей программы для блокировки рекламы (AdBlock и другие).
Check Point Software Technologies, Ltd. 360 роликов
4936 просмотров на сайте 12n.ru
Threat Emulation Explained by | Advanced Threat Prevention.
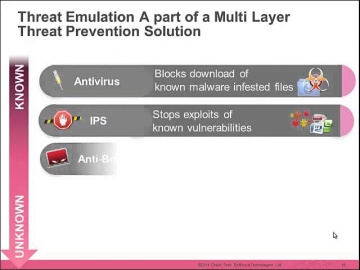
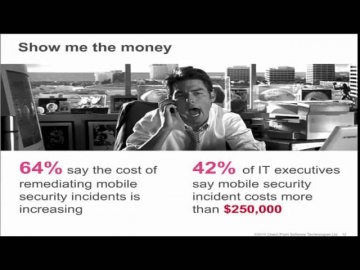
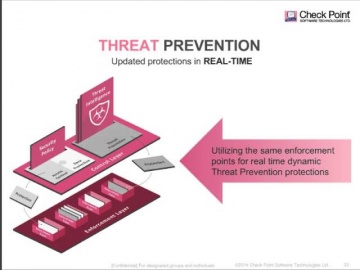
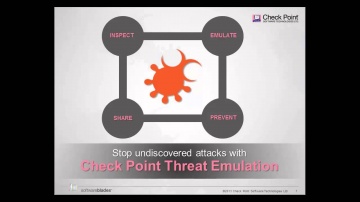
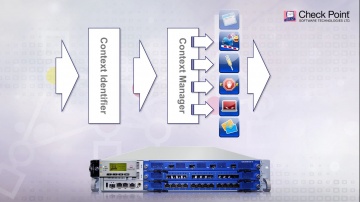
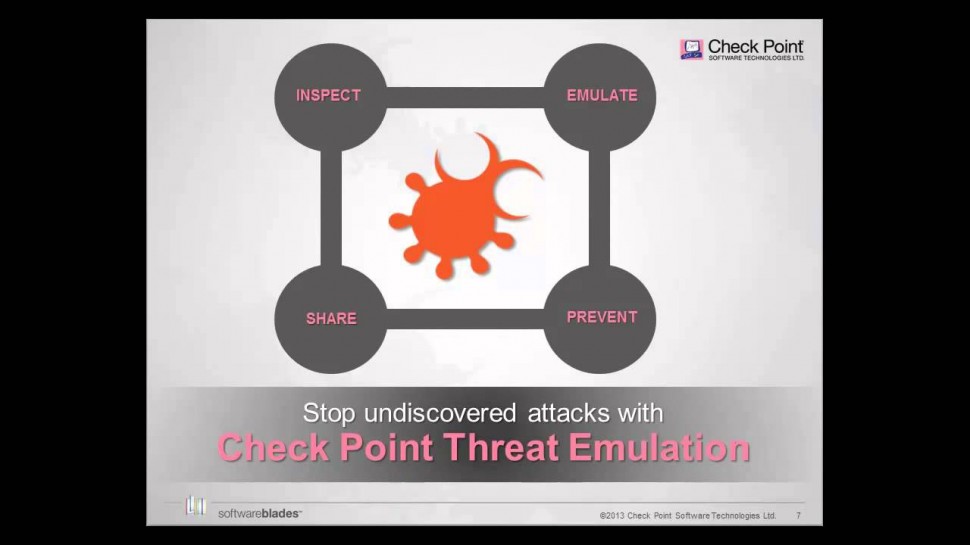
's Threat new Threat Emulation Software Blade prevents infections from undiscovered exploits, zero-day and targeted attacks. For more information: 's Threat new Threat Emulation Software Blade prevents infections from undiscovered exploits, zero-day and targeted attacks. This innovative solution quickly inspects suspicious files, emulates how they run to discover malicious behavior and completely prevents malware from entering the network. Threat Emulation also immediately reports new threats to 's ThreatCloud™ service and automatically shares the newly identified threats with other customers.As part of the SandBlast Zero-Day Protection solution, Threat Emulation prevents infections from new malware and targeted attacks. This innovative zero-day threat sandboxing capability within the SandBlast solution delivers the best possible catch rate for threats, and is virtually immune to attackers’ evasion techniques.
развернуть свернуть