Check Point Software Technologies, Ltd.

360 роликов
Нет подписчиков
Компания Check Point Software Technologies Ltd. — мировой поставщик решений в области обеспечения интернет-безопасности, единственный поставщик средств обеспечения полной безопасности Total Security для сетей, данных и конечных узлов, объединенных единой средой управления.
Сортировка

00:00:31
Обнаружено блокирование рекламы на сайте
Для существования нашего сайта необходим показ рекламы. Просим отнестись с пониманием и добавить сайт в список исключений вашей программы для блокировки рекламы (AdBlock и другие).
HD Check Point: Without the Best Security, Bad Things Happen
Two chatty security guards get distracted by a shiny coin, and their VIP client is swept away by criminals in a white van. For more information visit Takes real life security scenario, and demonstrates how the standard, traditional methods just don’t do the job any more. Gen V from , the only solution for 5th generation cyber security.
Что нового в R81 Management?
Никита Турков рассказывает об изменениях и новом функционале в управлении R81 - единой платформе кибезбезопасности.Вопросы, обсуждаемые в этом вебинаре: - Профили Infinity Treat Prevention - Объекты Data Center Query - Новая NAT полит...
Cмотреть видео
Cмотреть видео
Check Point: обзор и установка CloudGuard IaaS Gateway в Yandex.Cloud
В этом видео рассматриваются различные варианты продуктов Check Point CloudGuard IaaS Firewall & Threat Prevention (PAYG и BYOL) в Яндекс.Облако.Продукты Check Point в Yandex.Cloud: https://cloud.yandex.ru/marketplace?s... CloudGuard Ia...
Cмотреть видео
Cмотреть видео
iot: Безопасная экосистема Интернета вещей (IoT) - видео
Do you trust your IoT devices? Itzik Feiglevitch, Product Manager, Check Point Software TechnologiesРастущие с экспоненциальной скоростью устройства Интернета вещей приносят значительную ценность бизнесу, развивая и расширяя его возможности...
Cмотреть видео
Cмотреть видео
Check Point: CheckMates TechTalk: Analysis of SiliVaccine
SiliVaccine is an Anti-Virus tool used in North Korea. Security Researchers at got a copy of it to see if it had any abnormal behavior or undocumented features. Sure enough, it did!
Cмотреть видео
Cмотреть видео
Check Point: You Asked, CEO Gil Shwed Answers!
Is Gil Shwed a morning person or a night owl? CEO Gil Shwed talks about his favorite apps, drones, future roadmap, and recognizes the winners in our CheckMates Birthday Awards!
Cмотреть видео
Cмотреть видео
Check Point: CheckMates TechTalk: Remote Code Execution Vulnerability on LG Smartphones
Neatsun Ziv and Jonathan Shimonovich discuss our recent publication of vulnerabilities that reside in the default keyboard of all mainstream LG smartphone models. More details:
Cмотреть видео
Cмотреть видео
Check Point: You Asked, VP of Products Dorit Dor Answers!
Is Dr. Dorit Dor a morning person or a night owl? Our VP of Products talks about her favorite apps, drones, future roadmap, and recognizes the winners in our CheckMates Birthday Awards!
Cмотреть видео
Cмотреть видео
Check Point: CheckMates First Birthday Award Winners
CheckMates, the user community for customers and partners, is celebrating it's first birthday by recognizing excellent contributors and content!
Cмотреть видео
Cмотреть видео
Check Point: Lightboard Series: Dynamic Revisions
This video elaborates on the logic behind the R80.10 Security Management architecture focusing on the dynamic revisions feature. This feature automatically stores the full history of database changes, with very little footprint, consuming ...
Cмотреть видео
Cмотреть видео
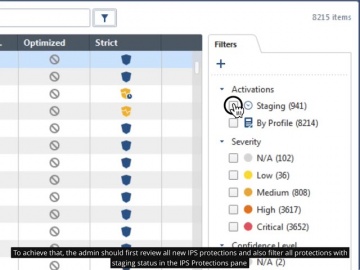
Check Point: R80.10 Policy Management – IPS Protections in Detect (Staging) State
This video elaborates on the logic behind new IPS protections status after IPS update operation and introduces best practice on changing the status of detect-staging on prevent when enough information was gathered regarding the new IPS prot...
Cмотреть видео
Cмотреть видео
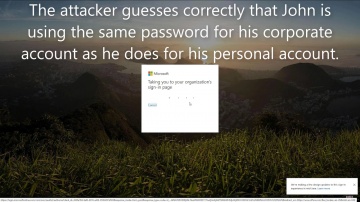
Check Point: CloudGuard SaaS Demo Series: Identity Protection for Office 365
Watch this short demonstration video to learn how CloudGuard SaaS, an industry-first software-as-a-service (SaaS) security solution, provides advanced security and identity protection including account takeover protection for SaaS applicat...
Cмотреть видео
Cмотреть видео
Check Point: Founder & CEO Gil Shwed on CNBC Squawk Box
CNBC Squawk Box featured Check Point CEO & Founder Gil Shwed. Gil Shwed discusses 5th generation cyber attacks. For more https://www.checkpoint.com/gen-v-cybe...Talking about level three attacks, level four attacks; what are fifth and s...
Cмотреть видео
Cмотреть видео
Check Point: EU GDPR Webinar Replay
The European Union’s General Data Protection Regulation (‘GDPR’) poses the biggest change to the regulatory landscape of data privacy. To learn more visit: GDPR places significant policy and technical responsibilities on ANY organization ...
Cмотреть видео
Cмотреть видео
Check Point: Who's Responsible for your Cloud Security?
A full breakdown of what is shared responsibility and the layers of security needed to protect you from security breaches in the cloud. For more information:
Cмотреть видео
Cмотреть видео
Check Point: The Mobile Threat Landscape
From Judy to Blueborne, the proliferation of mobile threats has grown rapidly in the past year. In this session, we review the various types of mobile threats, how they spread and the damage they cause. We will also be providing practical ...
Cмотреть видео
Cмотреть видео
Check Point: SMB Security Unique Challenges
The Small and Medium Business market has the same security challenges as larger enterprises. What they don't have a lot of is time or money.
Cмотреть видео
Cмотреть видео
Check Point: Security Blueprint for the Cloud Era
Discover the recommended blueprint for multi-cloud security. Take a deep dive on perimeter security, east-west security, connected clouds, auto-scale, and auto provisioning.
Cмотреть видео
Cмотреть видео
Check Point: GDPR Recommendations for Data Privacy
Coming into effect in May 2018, the European Union’s General Data Protection Regulation (‘GDPR’) poses the biggest change to the regulatory landscape of data protection and privacy.
Cмотреть видео
Cмотреть видео
Check Point: Orchestrating Gateway Operations
In this session, we will take you through some of the operations that are performed on gateways that are not the typical rule base changes.
Cмотреть видео
Cмотреть видео
Check Point: Mobile Security: Configuration and Policy Management Best Practices
What is your mobility policy? Have you ever considered the impact of your mobility policy on your organization? On your employees? Whether it is BYOD, CYOD or corporate owned, traditional mobile management will not cover the security aspe...
Cмотреть видео
Cмотреть видео
Check Point: L’Oréal vSEC Case Study
As one of the world’s leading beauty brands, the L'Oréal group has spent the last century in the pursuit of perfection.
Cмотреть видео
Cмотреть видео
Check Point: Infinity - A Day in the Life of a Security Administrator
Having worked with access control as a basic security level for over 20 years, the speakers reminisce about how much better it was in the past.
Cмотреть видео
Cмотреть видео
Check Point: R80 X Workflow, API, and Automation Use Cases
Software Technologies Ltd. — крупнейший в мире поставщик в области безопасности. Компания предлагает покупателям ведущие в индустрии решения и защищает покупателей от кибератак с непревзойденным уровнем успешного обнаружения вре...
Cмотреть видео
Cмотреть видео
Check Point: Adaptive Security Framework for Internet of Drones
Internet of Drones is an architecture designed for providing coordinated access to controlled airspace for Unmanned aerial vehicles (UAVs).
Cмотреть видео
Cмотреть видео
Check Point: IoT & Industrial Cyber Attacks - Myth or Reality?
There is a lot of hype around how IoT will be able to change our lives, make us smarter, more efficient and more connected than ever. On the other end some site the potential danger this revolution will bring assuming IoT will not be arch...
Cмотреть видео
Cмотреть видео
Check Point: Latest Innovations in Cyber Defense
In this session, we are going to see and use the latest protections from SandBlast Network and SandBlast Agent against the recent strains of malware and security risks from 2017.
Cмотреть видео
Cмотреть видео
Check Point: Learn from the Masters: Maximize the value of your Threat Prevention
Would you like to use SandBlast like a Cyber Jedi? Find out how to achieve the best possible prevention and visibility utilizing the full power of SandBlast’s cutting-edge cyber technologies. Learn from our top experts' cool tricks and be...
Cмотреть видео
Cмотреть видео
Check Point: Artificial Intelligence in Managed Incident Response
The presentation is focused on the Managed Incident Response 5.(MIR) and it will be based on the case studies of our two award-winning** customer projects, ITC and GSTN. We have successfully executed & extended the Sandblast Solution to ...
Cмотреть видео
Cмотреть видео
Check Point: Centralized Security Management Across the Enterprise
Managing security means having to deal with multiple point solutions. This is not only a challenge from an operations/TCO perspective, but also from a security standpoint (point solutions versus a consolidated approach will create security...
Cмотреть видео
Cмотреть видео
Check Point: Best of CheckMates: My Top CLI Commands
This presentation will highlight the most useful CLI commands submitted via CheckMates by real users just like you!+ For more information: Use cases, examples and case studies will be presented for the top CLI commands from the CheckMate...
Cмотреть видео
Cмотреть видео