Check Point: Mobile Security: Configuration and Policy Management Best Practices HD
00:25:14
Обнаружено блокирование рекламы на сайте
Для существования нашего сайта необходим показ рекламы. Просим отнестись с пониманием и добавить сайт в список исключений вашей программы для блокировки рекламы (AdBlock и другие).
Check Point Software Technologies, Ltd. 360 роликов
39 просмотров на сайте 12n.ru
Mobile Security: Configuration and Policy Management Best Practices.
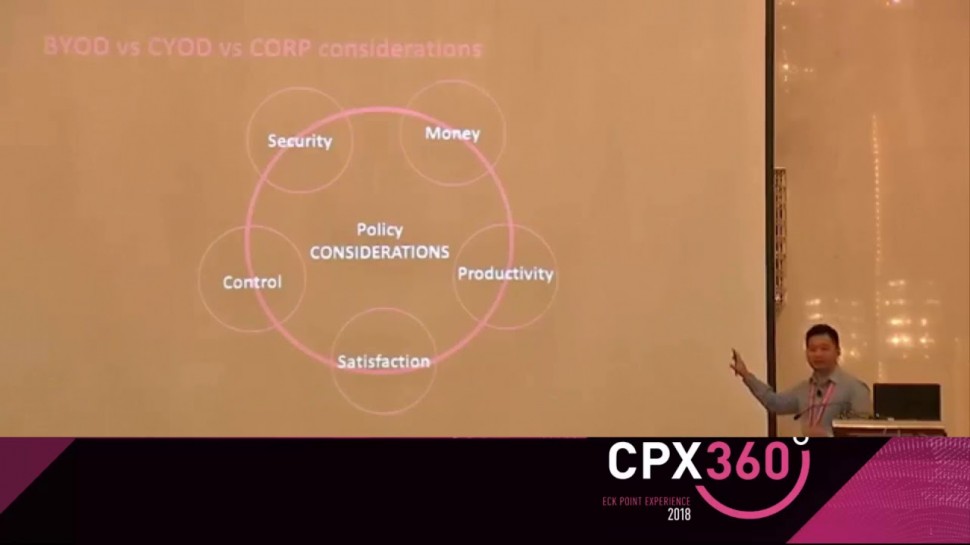
What is your mobility policy? Have you ever considered the impact of your mobility policy on your organization? On your employees? Whether it is BYOD, CYOD or corporate owned, traditional mobile management will not cover the security aspect.Objectives:* Threats on mobile devices* BYOD Vs. CYOD considerations* Recorded and live demo of the SideStepper attack* Live demo of how this attack is mitigated 3 times (SMS, Network, App) if this device was protected with SBM* Discuss and show the security integration with EMM (Tagging)
развернуть свернуть










