Check Point: Tech Bytes плейлист

360 роликов
Нет подписчиков
Компания Check Point Software Technologies Ltd. — мировой поставщик решений в области обеспечения интернет-безопасности, единственный поставщик средств обеспечения полной безопасности Total Security для сетей, данных и конечных узлов, объединенных единой средой управления.
Check Point: Tech Bytes
Software Technologies Ltd. — крупнейший в мире поставщик в области безопасности. Компания предлагает покупателям ведущие в индустрии решения и защищает покупателей от кибератак с непревзойденным уровнем успешного обнаружения вредоносного ПО и отражения других типов атак.
предлагает законченную архитектуру безопасности, которая защищает и сети крупных организаций, и мобильные устройства, а также отличается наиболее полным и интуитивно понятным управлением системой безопасности. стал первопроходцем в индустрии с межсетевым экраном FireWall-1 и запатентованной технологией Stateful Inspection.
Check Point: Petya Malware Blocked by Anti-Ransomware | Ransomware Cyberattack | Tech Bytes
A massive ransomware attack erupted on June 27 worldwide by a variant of Petya, a form of ransomware that encrypts the entire hard-drive rather than each file individually. This attack by Petya crippled many large banks, government offices ...
Cмотреть видео
Cмотреть видео
Check Point: SandBlast Mobile: Quick Start Guide | Tech Bytes
This video is meant to show how easily you can get started protecting your Enterprise's Android and iOS Devices with SandBlast Mobile. More information: Topics covered: Ch1 - Activating Your Admin Account Ch2 - Logging into Your SandBlast...
Cмотреть видео
Cмотреть видео
Check Point: Anti-Ransomware: Solution Brief & Demo | Tech Bytes
Anti-Ransomware protects against sophisticated zero-day ransomware. It is included in SandBlast Agent. More information: Protect endpoints from sophisticated attacks and zero-day threats, enabling a deep understanding of security events f...
Cмотреть видео
Cмотреть видео
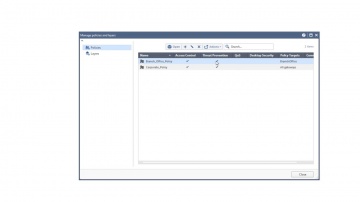
Check Point: R80.10 SmartConsole Security Policies View | Threat Prevention
This video is an overview that describes important features and functionality of the R80.10 SmartConsole and focuses on: Unified Access and Threat Prevention Policies Example of inline layers for zone-based policy Using multiple blades in o...
Cмотреть видео
Cмотреть видео
Check Point: Start Building Your Unified Policy with R80.10 | Security Management | Tech Bytes
R80.10 policy management is unified so you can create and monitor these policies harmoniously. One single policy manages your users, devices, applications, data and networks. With this unified policy, you also get unparalleled granular cont...
Cмотреть видео
Cмотреть видео
Check Point: R80.10 Security Management | Tech Bytes: Gateways, Logs, and Manage & Settings
This video is an overview that describes important features and functionality of the R80.10 SmartConsole. More information: To learn more about R80.10 Security Management: Infinity is the only fully consolidated cyber security architec...
Cмотреть видео
Cмотреть видео
Check Point: Automating vSEC in OpenStack | Tech Bytes
Demo video showcasing automation and orchestration of vSEC Security Gateway in OpenStack (without narration). For more information:
Cмотреть видео
Cмотреть видео
Check Point: Installing SandBlast Agent on the Enterprise Endpoint
This video provides an overview of recommended process for deployment of SandBlast Agent on the Enterprise Endpoints. SandBlast Agent defends endpoints with a complete set of real-time advanced endpoint protection technologies, including T...
Cмотреть видео
Cмотреть видео
Check Point: Overview of SandBlast Agent Forensics Report | Tech Bytes
This video provides an overview of SandBlast Agent’s Forensics Report. SandBlast Agent defends endpoints and web browsers with a complete set of real-time advanced browser and endpoint protection technologies, including Threat Emulation, T...
Cмотреть видео
Cмотреть видео
Check Point: SandBlast Agent Protects From Advanced Zero-day Malware
What happens if employees roam outside enterprise network that protect them from advanced zero-day invasions? For more information: SandBlast Agent protects the enterprise end-points from advanced zero-day malware, by using advanced C-P-U...
Cмотреть видео
Cмотреть видео
Check Point: SandBlast Agent Backs Up Anti-Virus by Preventing Recently Discovered Malware | Tech By
What happens if your anti-virus signature database is not updated with a very recently discovered malware? SandBlast Agent defends endpoints with a complete set of real-time advanced endpoint protection technologies, by using the up-to-date...
Cмотреть видео
Cмотреть видео
Check Point: SandBlast Agent Anti-Bot Protects the Endpoint from Bot Invasions | Tech Bytes
What happens if employees roam outside enterprise network that protect them from Bot invasions? SandBlast Agent protects the enterprise endpoints from Bot threats, by detecting the communication with command-and-control server. Its Anti-Bot...
Cмотреть видео
Cмотреть видео
Check Point: Use R80.10 New Packet Mode Feature to Search Through Policy
Packet Mode, a new feature introduced within R80.10, enables you to search the rule base as if it were a packet going through the security policy. For more information visit: R80.10 features the most advanced threat prevention across netw...
Cмотреть видео
Cмотреть видео
Check Point: Converting Another Vendor's Security Policy to is a SmartMove | Tech Bytes
offers migration tools and assistance to migrate your security policy from another vendor to . This video shows how you can use the SmartMove tool to migrate from Cisco to . To learn more about SmartMove in CheckMate visit:
Cмотреть видео
Cмотреть видео
Check Point: Managing Security Policy Changes with R80.10 | Tech Bytes
When new services are introduced and your security policy needs to be adjusted accordingly, what tools will you be using? R80.10 makes it easier to implement changes. The “Where Used” and “Replace” tools will help security administrators ma...
Cмотреть видео
Cмотреть видео
Check Point: Continuing Policy Work-in-Progress with R80.10 Session Take Over | Tech Bytes
R80.10 enables security administrators to work on the same policy at the same time. But what happens if a project needs to be finished and the security administrator is not available to do so? R80.10 Session Take Over feature allows for oth...
Cмотреть видео
Cмотреть видео
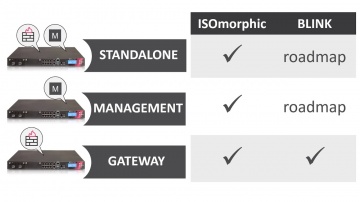
Check Point: Deployment Tools - ISOmorphic & Blink
Deploying Next Generation Firewalls just got easier with the introduction of the Blink utility. For more information: Blink creates a working snapshot of a cleanly installed security gateway with a completed First-Time Configuration Wizard...
Cмотреть видео
Cмотреть видео
Check Point: Deployment Tools; DIY security appliance images using ISOmorphic
Deployment Tools; DIY security appliance images using ISOmorphic. For more information: In our second video on deployment tools we show you how to image Security Appliances and Open Servers. With the ISOmorphic utility you can inst...
Cмотреть видео
Cмотреть видео
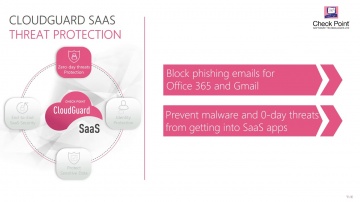
Check Point: Zero-day Threat Protection for SaaS Email | CloudGuard SaaS Demo
Demo showing how CloudGuard Saas provides advanced security and threat prevention for SaaS applications. For more information: Watch this short demonstration video to learn how CloudGuard SaaS, an industry-first software-as-a-service (Saa...
Cмотреть видео
Cмотреть видео
Check Point: CloudGuard SaaS Demo Series: Protecting Sensitive Data
For more information: Watch this short demonstration video to learn how CloudGuard SaaS, an industry-first software-as-a-service (SaaS) security solution, provides advanced security and sensitive data protection for SaaS applications such ...
Cмотреть видео
Cмотреть видео
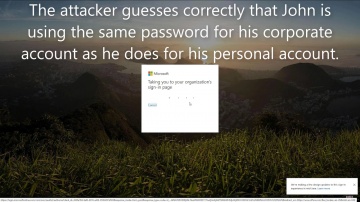
Check Point: CloudGuard SaaS Demo Series: Identity Protection for Office 365
Watch this short demonstration video to learn how CloudGuard SaaS, an industry-first software-as-a-service (SaaS) security solution, provides advanced security and identity protection including account takeover protection for SaaS applicat...
Cмотреть видео
Cмотреть видео
Check Point: Automating vSEC in OpenStack | Tech Bytes
Demo video showcasing automation and orchestration of vSEC Security Gateway in OpenStack (without narration). For more information:
Cмотреть видео
Cмотреть видео
Показать больше