Check Point: R80.10 Security Management | Tech Bytes: Gateways, Logs, and Manage & Settings, Check Point: Tech Bytes HD
00:04:32
Обнаружено блокирование рекламы на сайте
Для существования нашего сайта необходим показ рекламы. Просим отнестись с пониманием и добавить сайт в список исключений вашей программы для блокировки рекламы (AdBlock и другие).
Check Point Software Technologies, Ltd. 360 роликов
9278 просмотров на сайте 12n.ru
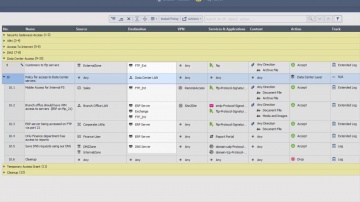
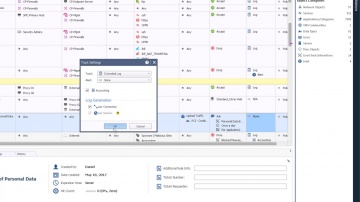
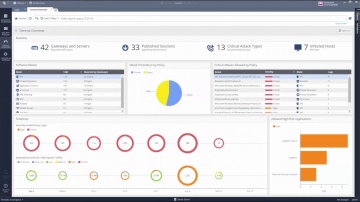
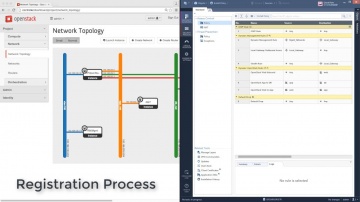
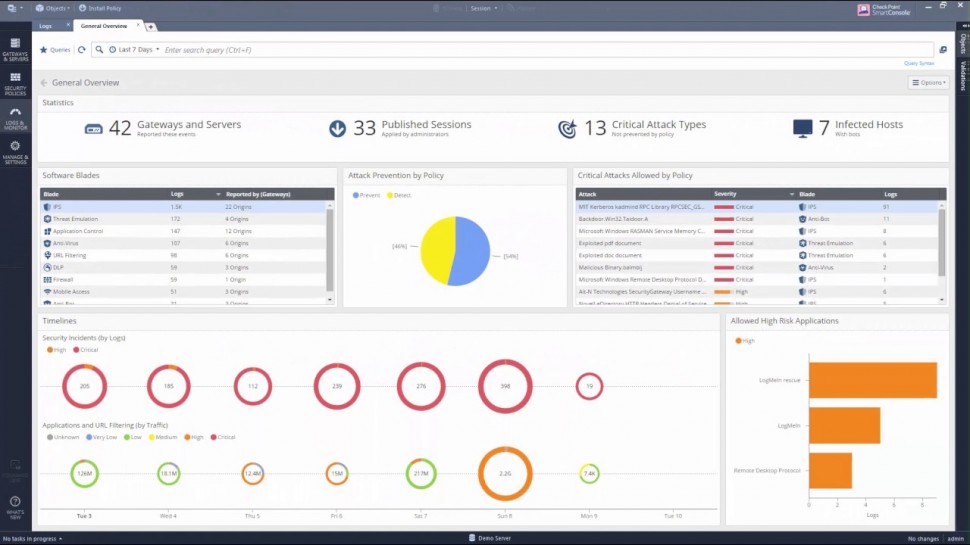
R80.10 Security Management | Tech Bytes: Gateways, Logs, and Manage & Settings.
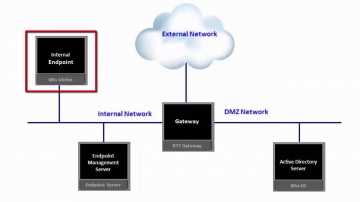
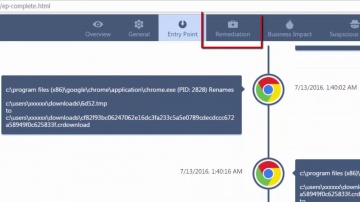
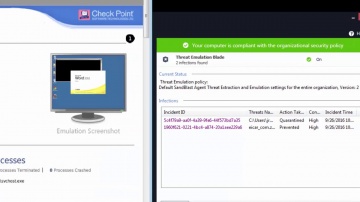
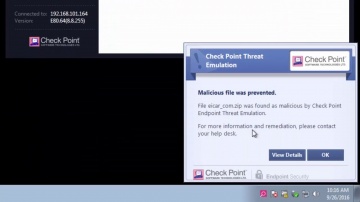
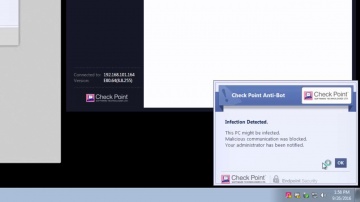
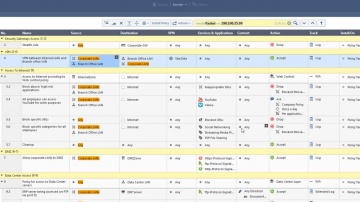
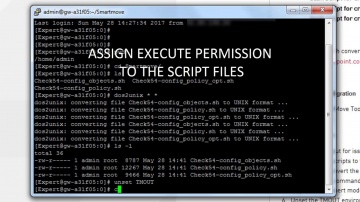
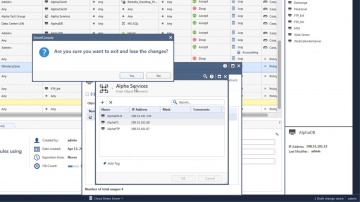
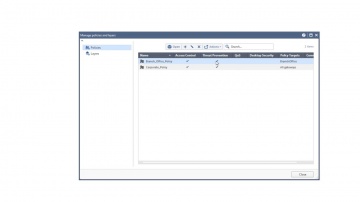
This video is an overview that describes important features and functionality of the R80.10 SmartConsole. More information: To learn more about R80.10 Security Management: Infinity is the only fully consolidated cyber security architecture that provides unprecedented protection against Gen V mega-cyberattacks as well as future cyber threats across all networks, endpoint, cloud and mobile. The architecture is designed to resolve the complexities of growing connectiviity and inefficient security.This video focuses on these views:Gateways & ServersLogs & MonitoringManage & Settings
развернуть свернуть