Поиск по тегу «check point infinity» в разделе Видеокаталог
HD 00:34:55
Check Point: Gil Shwed Keynote: Stepping Up to Gen V of Cyber Security
Gil Shwed's keynote from CPX 2018 on the future of Cyber Security. Find out what Gen V Cyber Attacks are and how you can prevent the next Cyber Attack. For more information visit -
Cмотреть видео
Cмотреть видео
HD 00:06:01
Check Point: Advanced Cyber Security for 2018 - Cyber Security Demo
This video is a technical demonstration of what the cyber security architecture of the future is all about. For more information visit: Infinity is the first consolidated cyber security across networks, cloud and mobile. Unlike other so...
Cмотреть видео
Cмотреть видео
HD 00:02:24
Check Point: SandBlast Mobile: How It Works
Accurate threat detection is a critical component of preventing advanced attacks on smartphones and tablets. Traditional mobile anti-virus, signature-based solutions identify known threats, but they can't detect zero-day malware or apps tha...
Cмотреть видео
Cмотреть видео
HD 00:02:22
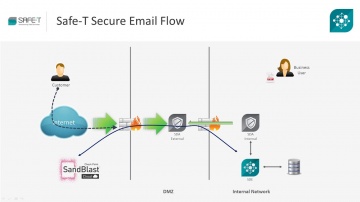
Check Point: Securing Data Exchange with SandBlast and Safe-T HDS
Organizations today face host of challenges in securing high risk data. SandBlast is most advanced protection against zero-day malware threats, while Safe-T HDS secures all data exchange scenarios including human data exchange such as secu...
Cмотреть видео
Cмотреть видео
HD 00:03:33
Check Point: Continuing Policy Work-in-Progress with R80.10 Session Take Over | Tech Bytes
R80.10 enables security administrators to work on the same policy at the same time. But what happens if a project needs to be finished and the security administrator is not available to do so? R80.10 Session Take Over feature allows for oth...
Cмотреть видео
Cмотреть видео
HD 00:03:13
Check Point: Managing Security Policy Changes with R80.10 | Tech Bytes
When new services are introduced and your security policy needs to be adjusted accordingly, what tools will you be using? R80.10 makes it easier to implement changes. The “Where Used” and “Replace” tools will help security administrators ma...
Cмотреть видео
Cмотреть видео
HD 00:04:30
Check Point: Converting Another Vendor's Security Policy to is a SmartMove | Tech Bytes
offers migration tools and assistance to migrate your security policy from another vendor to . This video shows how you can use the SmartMove tool to migrate from Cisco to . To learn more about SmartMove in CheckMate visit:
Cмотреть видео
Cмотреть видео
HD 00:04:03
Check Point: Use R80.10 New Packet Mode Feature to Search Through Policy
Packet Mode, a new feature introduced within R80.10, enables you to search the rule base as if it were a packet going through the security policy. For more information visit: R80.10 features the most advanced threat prevention across netw...
Cмотреть видео
Cмотреть видео
HD 00:24:49
Check Point: Welcome to the Future of Cyber Security | Infinity
The future of cyber security is here. Learn and stay protected against today's cyber threat landscape. For more information: We are all living in a connected world which is affecting every aspect of our lives. In the past couple of ye...
Cмотреть видео
Cмотреть видео
HD 00:26:30
Check Point: Infinity | The Cyber Security Architecture of the Future
Gabi Reish - VP, Product Management and Product Marketing, Software For more information on the Cyber Security Architecture of the Future, please go to:
Cмотреть видео
Cмотреть видео
HD 00:17:56
Check Point: Hacking the Smartphone | Mobile Cyber Hack Demonstration
Live demonstration of a smartphone hack, from Experience 2017. For more information visit: Watch Michael Shaulov, Head of Mobility Products at Software hack a smart phone in real time. Today every business is a mobile business, with req...
Cмотреть видео
Cмотреть видео
HD 00:18:41
Check Point: Cloud Security: Safe Journey to the Cloud
The era of cloud is upon us; firms of all sizes and in all walks of life are looking to leverage the agility and elasticity of cloud. For more information visit: But cloud carries a totally new and unique set of security challenges. In th...
Cмотреть видео
Cмотреть видео
HD 00:04:47
Check Point: R80.10 SmartConsole Security Policies View | Threat Prevention
This video is an overview that describes important features and functionality of the R80.10 SmartConsole and focuses on: Unified Access and Threat Prevention Policies Example of inline layers for zone-based policy Using multiple blades in o...
Cмотреть видео
Cмотреть видео
HD 00:05:27
Check Point: Start Building Your Unified Policy with R80.10 | Security Management | Tech Bytes
R80.10 policy management is unified so you can create and monitor these policies harmoniously. One single policy manages your users, devices, applications, data and networks. With this unified policy, you also get unparalleled granular cont...
Cмотреть видео
Cмотреть видео
HD 00:04:32
Check Point: R80.10 Security Management | Tech Bytes: Gateways, Logs, and Manage & Settings
This video is an overview that describes important features and functionality of the R80.10 SmartConsole. More information: To learn more about R80.10 Security Management: Infinity is the only fully consolidated cyber security architec...
Cмотреть видео
Cмотреть видео
HD 00:01:25
Check Point: Advanced Cyber Security for 2018 | Infinity
Learn more at Introducing Infinity, the world’s most advanced cyber security and management architecture. Infinity consolidates security across network, cloud and mobile, keeping you secured from known and unknown threats, today and in ...
Cмотреть видео
Cмотреть видео
HD 01:03:18
Check Point: and Tufin: Security Management for the Future | Enterprise Network Security
and Tufin provide complete, simplified and automated security management for the enterprise network of the future. For more information: Together, the Tufin Orchestration Suite with Firewalls and Security Management products provide ad...
Cмотреть видео
Cмотреть видео
HD 00:43:39
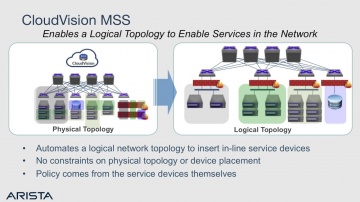
Check Point: & Arista: The Journey to Secure Cloud Networking
Learn from our experts about how and Arista’s Macro-Segmentation Service (MSS) protects the modern data center. For more information: With and Arista CloudVision MSS, ’s data center firewalls can be attached anywhere in the network on ...
Cмотреть видео
Cмотреть видео
HD 00:02:24
Check Point: Technical Assistance Center | Network Security Support
's team of vigilant security experts are here to help our customers. Well trained engineers are available to assist you 24/7 via web service request, live chat, or by phone. For more information:
Cмотреть видео
Cмотреть видео
HD 00:03:20
Check Point: 2017 Mobile Security Media Tour
Our Michael Shaulov, Head of Product, Mobile Security discusses the importance of mobile security and common vulnerabilities and threats mobile data of individuals and the enterprise. For more information:
Cмотреть видео
Cмотреть видео
HD 00:02:14
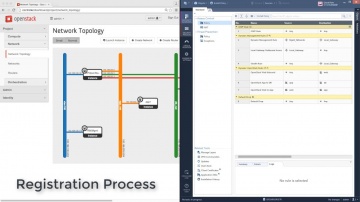
Check Point: Automating vSEC in OpenStack | Tech Bytes
Demo video showcasing automation and orchestration of vSEC Security Gateway in OpenStack (without narration). For more information:
Cмотреть видео
Cмотреть видео
HD 00:02:14
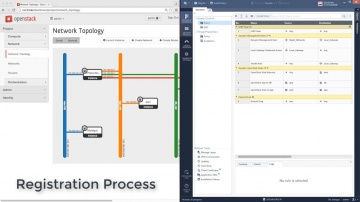
Check Point: Automating vSEC in OpenStack | Tech Bytes
Demo video showcasing automation and orchestration of vSEC Security Gateway in OpenStack (without narration). For more information:
Cмотреть видео
Cмотреть видео
HD 00:07:15
Check Point: vSEC, The Future of Cloud Security
In this video, you’ll hear from Donald Meyer, Head of Marketing, Data Center and Cloud, where he discusses issues surrounding Cloud security and how organizations can better protect themselves from vulnerabilities in the Cloud. For more in...
Cмотреть видео
Cмотреть видео
HD 00:02:37
Check Point: Protecting Mobile Devices Together - ElevenPaths – Telefonica and | Mobile Security
“Mobile devices are critical to the way we do business today. With cyberattacks growing in sophistication and frequency, exposing both the business and personal data we store on smartphones and tablets, mobile devices are the newest enterpr...
Cмотреть видео
Cмотреть видео
HD 00:01:50
Check Point: Hamas’ Cyber Tactics Exposed - Attacking IDF Soldier’s Mobile Phones
The Israeli Defense Forde uncovered a Hamas network that reached out to IDF soldiers online, sometimes in romantic ways, and ask them to download applications that would infect them with Trojan horse viruses. The applications used by Hamas ...
Cмотреть видео
Cмотреть видео
HD 00:00:38
Check Point: vSEC for your AWS Workloads
Utilizing the same security management tool across your hybrid cloud architecture can help your organization be more secure and agile. Maximize the strength of your security posture and capacity for innovation in cloud environments with vSE...
Cмотреть видео
Cмотреть видео
HD 00:00:32
Check Point: Secure Your AWS Apps and Data | Cloud Security
vSEC delivers comprehensive threat prevention security with consolidated management and enforcement for AWS hybrid clouds. For more information:
Cмотреть видео
Cмотреть видео
HD 00:02:13
Check Point: Daymark Secures Cloud with CloudGuard (formerly vSEC) for Microsoft Azure | Cloud Secur
Daymark solutions, trusted advisor to businesses in the Northeast, implemented CloudGuard (formerly vSEC) for Microsoft Azure and now recommends it to all its customers for ease of use, comprehensive visibility and threat prevention. Hea...
Cмотреть видео
Cмотреть видео
HD 00:02:13
Check Point: Daymark Secures Cloud with CloudGuard (formerly vSEC) for Microsoft Azure | Cloud Secur
Daymark solutions, trusted advisor to businesses in the Northeast, implemented CloudGuard (formerly vSEC) for Microsoft Azure and now recommends it to all its customers for ease of use, comprehensive visibility and threat prevention. Hea...
Cмотреть видео
Cмотреть видео
HD 00:07:14
Check Point: Creating Host Objects with R80 Management API Tutorial | Security Management Tutorial
How to use R80 Management API to run a BASH script that automatically creates host objects in the Security Management server database. For more information: This video tutorial is intended for users that are familiar with automation scri...
Cмотреть видео
Cмотреть видео