Check Point: The Security Zone Ep. 5: Impact of Mobile Devices on Information Security, Check Point: Webinars
00:18:31
Обнаружено блокирование рекламы на сайте
Для существования нашего сайта необходим показ рекламы. Просим отнестись с пониманием и добавить сайт в список исключений вашей программы для блокировки рекламы (AdBlock и другие).
Check Point Software Technologies, Ltd. 360 роликов
341 просмотр на сайте 12n.ru
The Security Zone Ep. 5: Impact of Mobile Devices on Information Security.
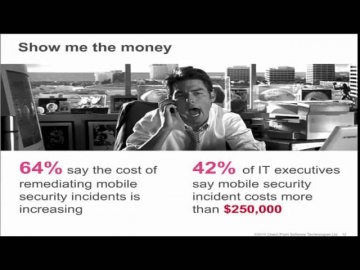
teamed up with Dimensional Analysis to survey over 700 IT and security professionals in 6 countries to learn the current attitudes and trends regarding the impact of mobile devices on information security.
развернуть свернуть