Поиск по тегу «advanced threat prevention» в разделе Видеокаталог
HD 01:01:35
Check Point: EU GDPR Webinar Replay
The European Union’s General Data Protection Regulation (‘GDPR’) poses the biggest change to the regulatory landscape of data privacy. To learn more visit: GDPR places significant policy and technical responsibilities on ANY organization ...
Cмотреть видео
Cмотреть видео
HD 00:02:10
Check Point: SandBlast Mobile: Protecting Against Malicious Apps
Our mobile devices are used for both personal and business purposes. Installing new apps may compromise both your private and corporate data. Every year, malicious apps downloaded from official app stores infect millions of mobile devices....
Cмотреть видео
Cмотреть видео
HD 00:02:22
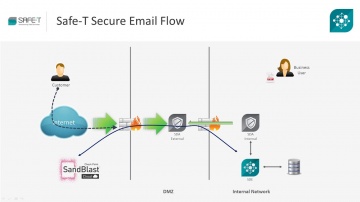
Check Point: Securing Data Exchange with SandBlast and Safe-T HDS
Organizations today face host of challenges in securing high risk data. SandBlast is most advanced protection against zero-day malware threats, while Safe-T HDS secures all data exchange scenarios including human data exchange such as secu...
Cмотреть видео
Cмотреть видео
HD 00:18:47
Check Point: Gil Shwed & Marius Nacht Interview - Milan 2017
Gil Shwed & Marius Nacht discuss product innovation and the Experience over the years. For more information:
Cмотреть видео
Cмотреть видео
HD 00:26:30
Check Point: Infinity | The Cyber Security Architecture of the Future
Gabi Reish - VP, Product Management and Product Marketing, Software For more information on the Cyber Security Architecture of the Future, please go to:
Cмотреть видео
Cмотреть видео
HD 00:17:56
Check Point: Hacking the Smartphone | Mobile Cyber Hack Demonstration
Live demonstration of a smartphone hack, from Experience 2017. For more information visit: Watch Michael Shaulov, Head of Mobility Products at Software hack a smart phone in real time. Today every business is a mobile business, with req...
Cмотреть видео
Cмотреть видео
HD 00:18:41
Check Point: Cloud Security: Safe Journey to the Cloud
The era of cloud is upon us; firms of all sizes and in all walks of life are looking to leverage the agility and elasticity of cloud. For more information visit: But cloud carries a totally new and unique set of security challenges. In th...
Cмотреть видео
Cмотреть видео
HD 00:43:39
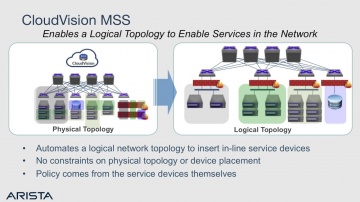
Check Point: & Arista: The Journey to Secure Cloud Networking
Learn from our experts about how and Arista’s Macro-Segmentation Service (MSS) protects the modern data center. For more information: With and Arista CloudVision MSS, ’s data center firewalls can be attached anywhere in the network on ...
Cмотреть видео
Cмотреть видео
HD 00:02:24
Check Point: Technical Assistance Center | Network Security Support
's team of vigilant security experts are here to help our customers. Well trained engineers are available to assist you 24/7 via web service request, live chat, or by phone. For more information:
Cмотреть видео
Cмотреть видео
HD 00:03:20
Check Point: 2017 Mobile Security Media Tour
Our Michael Shaulov, Head of Product, Mobile Security discusses the importance of mobile security and common vulnerabilities and threats mobile data of individuals and the enterprise. For more information:
Cмотреть видео
Cмотреть видео
HD 00:02:14
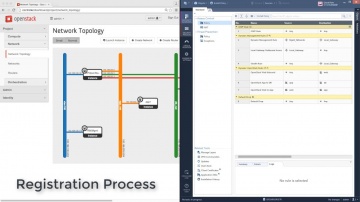
Check Point: Automating vSEC in OpenStack | Tech Bytes
Demo video showcasing automation and orchestration of vSEC Security Gateway in OpenStack (without narration). For more information:
Cмотреть видео
Cмотреть видео
HD 00:02:14
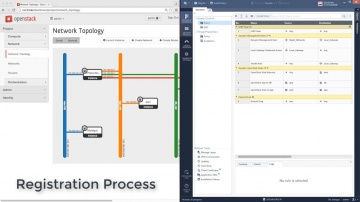
Check Point: Automating vSEC in OpenStack | Tech Bytes
Demo video showcasing automation and orchestration of vSEC Security Gateway in OpenStack (without narration). For more information:
Cмотреть видео
Cмотреть видео
HD 00:07:15
Check Point: vSEC, The Future of Cloud Security
In this video, you’ll hear from Donald Meyer, Head of Marketing, Data Center and Cloud, where he discusses issues surrounding Cloud security and how organizations can better protect themselves from vulnerabilities in the Cloud. For more in...
Cмотреть видео
Cмотреть видео
HD 00:02:37
Check Point: Protecting Mobile Devices Together - ElevenPaths – Telefonica and | Mobile Security
“Mobile devices are critical to the way we do business today. With cyberattacks growing in sophistication and frequency, exposing both the business and personal data we store on smartphones and tablets, mobile devices are the newest enterpr...
Cмотреть видео
Cмотреть видео
HD 00:01:50
Check Point: Hamas’ Cyber Tactics Exposed - Attacking IDF Soldier’s Mobile Phones
The Israeli Defense Forde uncovered a Hamas network that reached out to IDF soldiers online, sometimes in romantic ways, and ask them to download applications that would infect them with Trojan horse viruses. The applications used by Hamas ...
Cмотреть видео
Cмотреть видео
HD 00:00:38
Check Point: vSEC for your AWS Workloads
Utilizing the same security management tool across your hybrid cloud architecture can help your organization be more secure and agile. Maximize the strength of your security posture and capacity for innovation in cloud environments with vSE...
Cмотреть видео
Cмотреть видео
HD 00:00:32
Check Point: Secure Your AWS Apps and Data | Cloud Security
vSEC delivers comprehensive threat prevention security with consolidated management and enforcement for AWS hybrid clouds. For more information:
Cмотреть видео
Cмотреть видео
HD 00:02:13
Check Point: Daymark Secures Cloud with CloudGuard (formerly vSEC) for Microsoft Azure | Cloud Secur
Daymark solutions, trusted advisor to businesses in the Northeast, implemented CloudGuard (formerly vSEC) for Microsoft Azure and now recommends it to all its customers for ease of use, comprehensive visibility and threat prevention. Hea...
Cмотреть видео
Cмотреть видео
HD 00:02:13
Check Point: Daymark Secures Cloud with CloudGuard (formerly vSEC) for Microsoft Azure | Cloud Secur
Daymark solutions, trusted advisor to businesses in the Northeast, implemented CloudGuard (formerly vSEC) for Microsoft Azure and now recommends it to all its customers for ease of use, comprehensive visibility and threat prevention. Hea...
Cмотреть видео
Cмотреть видео
HD 00:01:41
Check Point: From HummingBad to Worse: Android Malware Campaign | SandBlast Mobile Security
For five months, mobile threat researchers had unprecedented access to the inner-workings of Yingmob, the Chinese cyber criminals behind HummingBad, a malware that establishes a persistent rootkit on Android devices, generates fraudulent a...
Cмотреть видео
Cмотреть видео
HD 00:02:42
Check Point: SandBlast Cloud Advanced Threat Prevention for Microsoft Office 365 | Email Security
Dramatic growth in the use of cloud-based email for the enterprise brings with it an array of security risks, including susceptibility to sophisticated cyber attacks such as ransomware and APTs which use email as a primary entry point. San...
Cмотреть видео
Cмотреть видео
HD 00:01:41
Check Point: Viking Horde: A New Type of Android Malware on Google Play | Mobile Security
Blog: More information: The research team uncovered a new Android malware campaign on Google Play it calls Viking Horde. Viking Horde conducts ad fraud, but can also be used for other attack purposes such as DDoS attacks, spam messages...
Cмотреть видео
Cмотреть видео
HD 00:02:09
Check Point: SmartConsole Integration with Cisco ACI | Private Cloud Networks
vSEC for Cisco ACI securely enables the rapid deployment of applications in private cloud networks. The integration with CiscoÛªs APIC Controller lowers the time it takes to create and update security policies from minutes to seconds, allo...
Cмотреть видео
Cмотреть видео
HD 00:03:59
Check Point: Pokemon GO Repackaged Malware Demonstration | SandBlast Mobile Security Demo
The excitement over the new game Pokemon GO has taken the world by storm. Because it's available only in limited countries right now, some people may be tempted to download the app from sources other than Google Play or the Apple App Store....
Cмотреть видео
Cмотреть видео
HD 00:02:48
Check Point: Samsung Research America Chooses Mobile Threat Prevention
As the research arm of an industry-leading manufacturer of consumer electronics, Samsung Research America is committed to forward-looking innovation and bringing new products to market ahead of competitors. More Info: The last thing it n...
Cмотреть видео
Cмотреть видео
HD 00:02:24
Check Point: Partner Success Story - RoundTower on vSEC Solution | Cloud Security
For More Information: ... Partner Round Tower shares a vSEC success story highlighting the features and benefits of vSEC for VMware NSX advanced security for the Software-Defined Data Center. vSEC integration with VMware NSX delivers dyn...
Cмотреть видео
Cмотреть видео
HD 00:02:44
Check Point: and VMware Partnership delivers advanced security for the SDDC | Cloud Security
More Information: VMware and Partnership delivers advanced security for the Software-Defined Data Center. vSEC integration with VMware NSX delivers dynamic orchestration of advanced threat prevention for all traffic in the Software-Def...
Cмотреть видео
Cмотреть видео
00:02:08
Check Point: Customer Success Video: Helvetia Insurance, vSEC for VMware NSX | Cloud Security
For over 150 years, Helvetia has grown into a successful international insurance group with a wide range of services. Andreas Hagin, Head of Corporate Network & Unified Communication Engineering at Helvetia, discusses the importance of ...
Cмотреть видео
Cмотреть видео
HD 00:04:02
Check Point: SideStepper: Anatomy of an iOS Vulnerability | Mobile Threat Prevention
For more information, visit: Report: IDC Technology Spotlight: Why Comprehensive Security Requires Mobile Threat Prevention: disclosed details about SideStepper, a vulnerability that can be used to install malicious enterprise apps o...
Cмотреть видео
Cмотреть видео
HD 00:01:32
Check Point: SandBlast Mobile Security: Man-in-the-Middle Mobile Attacks
Our mobile devices are more vulnerable then we think. A man-in-the middle attack is a potential threat every time you connect to a Wi-Fi network. For more information: Imagine you are at a coffee shop and you want to connect to Wi-Fi and...
Cмотреть видео
Cмотреть видео