Поиск по тегу «security technology» в разделе Видеокаталог
HD 00:34:55
Check Point: Gil Shwed Keynote: Stepping Up to Gen V of Cyber Security
Gil Shwed's keynote from CPX 2018 on the future of Cyber Security. Find out what Gen V Cyber Attacks are and how you can prevent the next Cyber Attack. For more information visit -
Cмотреть видео
Cмотреть видео
HD 00:19:44
Check Point: Cloud Security - VMware & CloudGuard - CPX 360 2018
Businesses that use the public cloud are vulnerable to cyber threats. Learn how to close the security gaps in the cloud. Public and hybrid cloud adoption is exploding among enterprises, but so are cloud hacks and breaches. Cloud asset...
Cмотреть видео
Cмотреть видео
HD 00:06:37
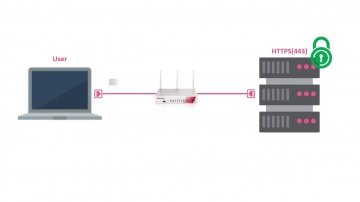
Check Point: HTTPS Inspection on Small Business Appliances
Watch our tutorial on how to enable HTTPS inspection on our 700 Appliance to improve your small business security. More information:
Cмотреть видео
Cмотреть видео
HD 00:09:10
Check Point: Software’s vSEC Cloud Security featured in Globb TV Interview at VMWorld 2017
More information: Itai Greenberg, Head of Cloud Security at Software Technologies, describes how ’s vSEC Cloud Security protects workloads in public clouds like AWS, private clouds like VMware SDDC ( using NSX ) and hybrid clouds built u...
Cмотреть видео
Cмотреть видео
HD 00:01:56
Check Point: Defeats Mobile Cyberattacks
Advanced cybercrimes aren’t science fiction; they’re real – and have real consequences. is at the forefront of mobile security, ensuring that devices and data everywhere remain safe. We don’t just build cutting edge technology: we stand be...
Cмотреть видео
Cмотреть видео
HD 00:02:24
Check Point: SandBlast Mobile: How It Works
Accurate threat detection is a critical component of preventing advanced attacks on smartphones and tablets. Traditional mobile anti-virus, signature-based solutions identify known threats, but they can't detect zero-day malware or apps tha...
Cмотреть видео
Cмотреть видео
HD 00:08:41
Check Point: 's Avi Rembaum: Shedding Light on the Dark Web
Leveraging intelligence culled from the Dark Web will help boost information security for enterprises, says Avi Rembaum of Software Technologies. "What's really becoming far more important is leveraging the intelligence coming from that r...
Cмотреть видео
Cмотреть видео
HD 00:03:33
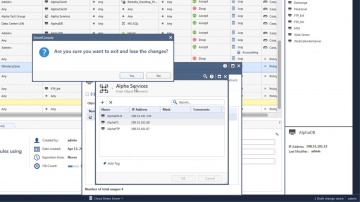
Check Point: Continuing Policy Work-in-Progress with R80.10 Session Take Over | Tech Bytes
R80.10 enables security administrators to work on the same policy at the same time. But what happens if a project needs to be finished and the security administrator is not available to do so? R80.10 Session Take Over feature allows for oth...
Cмотреть видео
Cмотреть видео
HD 00:03:13
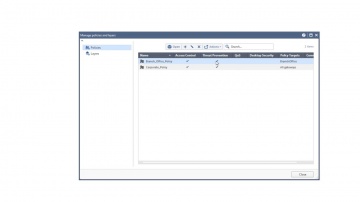
Check Point: Managing Security Policy Changes with R80.10 | Tech Bytes
When new services are introduced and your security policy needs to be adjusted accordingly, what tools will you be using? R80.10 makes it easier to implement changes. The “Where Used” and “Replace” tools will help security administrators ma...
Cмотреть видео
Cмотреть видео
HD 00:04:30
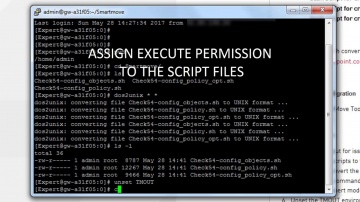
Check Point: Converting Another Vendor's Security Policy to is a SmartMove | Tech Bytes
offers migration tools and assistance to migrate your security policy from another vendor to . This video shows how you can use the SmartMove tool to migrate from Cisco to . To learn more about SmartMove in CheckMate visit:
Cмотреть видео
Cмотреть видео
HD 00:04:12
Check Point: SandBlast Agent Protects From Advanced Zero-day Malware
What happens if employees roam outside enterprise network that protect them from advanced zero-day invasions? For more information: SandBlast Agent protects the enterprise end-points from advanced zero-day malware, by using advanced C-P-U...
Cмотреть видео
Cмотреть видео
HD 00:03:41
Check Point: Overview of SandBlast Agent Forensics Report | Tech Bytes
This video provides an overview of SandBlast Agent’s Forensics Report. SandBlast Agent defends endpoints and web browsers with a complete set of real-time advanced browser and endpoint protection technologies, including Threat Emulation, T...
Cмотреть видео
Cмотреть видео
HD 00:02:35
Check Point: SandBlast Agent Backs Up Anti-Virus by Preventing Recently Discovered Malware | Tech By
What happens if your anti-virus signature database is not updated with a very recently discovered malware? SandBlast Agent defends endpoints with a complete set of real-time advanced endpoint protection technologies, by using the up-to-date...
Cмотреть видео
Cмотреть видео
HD 00:03:59
Check Point: SandBlast Agent Anti-Bot Protects the Endpoint from Bot Invasions | Tech Bytes
What happens if employees roam outside enterprise network that protect them from Bot invasions? SandBlast Agent protects the enterprise endpoints from Bot threats, by detecting the communication with command-and-control server. Its Anti-Bot...
Cмотреть видео
Cмотреть видео
HD 00:06:09
Check Point: Introducción a Compliance Blade
Introducción a Compliance Blade a Software
Cмотреть видео
Cмотреть видео
HD 00:38:26
Check Point: Estado de la Ciberseguridad en Operadores de ICS Españolas | CyberDay Spain 2017
Miguel García, VP Centro de Ciberseguridad Industrial Cofundador y Presidente, iTTi, The [Digital] Accountability Think Tank.
Cмотреть видео
Cмотреть видео
HD 00:22:11
Check Point: WannaCry 3.0, próximamente en sus pantallas… del móvil | CyberDay Spain 2017
Ran Schwartz, Product Manager para Mobile Security Products
Cмотреть видео
Cмотреть видео
HD 00:27:06
Check Point: Un Viaje Seguro a la Nube | CyberDay Spain 2017
Javier Hijas, Cloud Security Team Leader Europe
Cмотреть видео
Cмотреть видео
HD 00:28:43
Check Point: Sobrevivir a la plaga de ransomware | CyberDay Spain 2017
Eusebio Nieva, Director Técnico España y Portugal
Cмотреть видео
Cмотреть видео
HD 00:02:06
Check Point: Helvetia Insurance : vSEC for NSXの導入事例
スイスで3番目に大きな保険会社Helvetia InsuranceのvSEC for NSXの導入事例です。保険とは信頼の上に成り立つビジネスなので、お客様の満足度は特に重要であり、セキュリティ対策に求めらるレベルも非常に高いです。ハイレベルなニーズに応えたのがチェック・ポイントのvSEC for NSXでした。
Cмотреть видео
Cмотреть видео
HD 00:03:29
Check Point: Petya Malware Blocked by Anti-Ransomware | Ransomware Cyberattack | Tech Bytes
A massive ransomware attack erupted on June 27 worldwide by a variant of Petya, a form of ransomware that encrypts the entire hard-drive rather than each file individually. This attack by Petya crippled many large banks, government offices ...
Cмотреть видео
Cмотреть видео
HD 00:04:35
Check Point: Anti-Ransomware: Tecnología y Demostración
Anti-Ransomware protege contra el ransomware de día cero. Está incluido en el paquete de SandBlast Agent. Este video presenta la descripción de la solución seguido por una demonstración. Anti-Ransomware usa las habilidades del análisis for...
Cмотреть видео
Cмотреть видео
HD 00:03:02
Check Point: CloudGuard (formerly vSEC) Gateway Introduction
CloudGuard (formerly vSEC) Intro to the Gateway by Greg Pepper, Data Center Security Architect. For more information: Complete Threat Prevention Security for Enterprise Clouds Cloud adoption continues to skyrocket, yet so are attacks targ...
Cмотреть видео
Cмотреть видео
HD 00:23:09
Check Point: R80.10 Best Practices – Migrating from R77.30
Get the insights from Professional Services on how to migrate from R77.30 to R80.10.
Cмотреть видео
Cмотреть видео
HD 00:04:45
Check Point: R80.10 Policy Revision
R80.10 Policy revision explained. Learn how to work with policy revision in R80.10. For more information: R80.10 features the most advanced threat prevention across networks and cloud, managed by a single security management console. Secu...
Cмотреть видео
Cмотреть видео
HD 00:04:30
Check Point: Anti-Ransomware: Solution Brief & Demo | Tech Bytes
Anti-Ransomware protects against sophisticated zero-day ransomware. It is included in SandBlast Agent. More information: Protect endpoints from sophisticated attacks and zero-day threats, enabling a deep understanding of security events f...
Cмотреть видео
Cмотреть видео
HD 00:18:47
Check Point: Gil Shwed & Marius Nacht Interview - Milan 2017
Gil Shwed & Marius Nacht discuss product innovation and the Experience over the years. For more information:
Cмотреть видео
Cмотреть видео
HD 00:24:49
Check Point: Welcome to the Future of Cyber Security | Infinity
The future of cyber security is here. Learn and stay protected against today's cyber threat landscape. For more information: We are all living in a connected world which is affecting every aspect of our lives. In the past couple of ye...
Cмотреть видео
Cмотреть видео
HD 00:26:30
Check Point: Infinity | The Cyber Security Architecture of the Future
Gabi Reish - VP, Product Management and Product Marketing, Software For more information on the Cyber Security Architecture of the Future, please go to:
Cмотреть видео
Cмотреть видео
HD 00:27:09
Check Point: Shedding Light on the Dark Web
Avi Rembaum + Neatsun Ziv The dark web is quickly evolving into a marketplace of information and tools that the hackers and adversaries use to breach company networks. The question we face as an industry is how to leverage an awareness of ...
Cмотреть видео
Cмотреть видео