Check Point: Stop Advanced Mobile Threats Before They Start | SandBlast Mobile Security, Check Point: Mobile Security HD

00:02:24
Обнаружено блокирование рекламы на сайте
Для существования нашего сайта необходим показ рекламы. Просим отнестись с пониманием и добавить сайт в список исключений вашей программы для блокировки рекламы (AdBlock и другие).
Check Point Software Technologies, Ltd. 360 роликов
9619 просмотров на сайте 12n.ru
Stop Advanced Mobile Threats Before They Start | SandBlast Mobile Security.
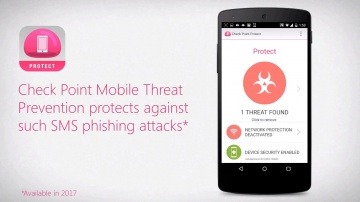
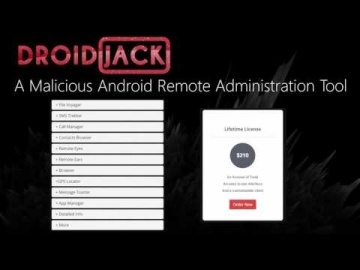
Learn More: Report: IDC Technology Spotlight: Why Comprehensive Security Requires Mobile Threat Prevention: Cyber criminals may be stealing data from your smartphone or tablet without your knowledge. They’re experts at exploiting vulnerabilities in apps, networks, and devices that give them full access to your sensitive data, and can even turn your mobile device into a spying machine. Watch this video to learn more about how Mobile Threat Prevention helps keep mobile devices and data protected.Transcript:We use mobile devices now more than ever to manage our work and personal lives. But how do you protect what you can’t control?Mobile Device Management solutions can manage static device policies and apps; and secure containers help prevent data leakage, but neither detects or stops advanced threats. Cybercriminals are exploiting these gaps in mobile security to steal valuable, sensitive data. And without visibility, even skilled security professionals may not discover an attack until it’s too late. Mobile Threat Prevention manages and mitigates these risks to keep employees and assets protected. With the industry’s highest catch rate, it’s the only solution that stops threats on the device, in applications, and in the network. Users don’t need to learn anything new or change the way they already use their devices. Mobile Threat Prevention runs in the background without impacting performance or battery life. It collects metadata from the device that the cloud-based threat emulation engine uses to identify suspicious behavior. The engine performs static code analysis, evaluates app reputation, and uses advanced machine learning to detect known and unknown threats. It reduces the attack surface with real-time detection and mitigation of malicious apps; discovery of anomalies, vulnerabilities, and configuration changes; and advanced identification of device rooting or jailbreaking. It blocks unsafe Wi-Fi hotspots, thwarts man-in-the-middle attacks, and stops access to corporate networks until threats are eliminated. Integration with existing MDM and EMM solutions makes deploying the solution fast and easy, and enables automatic device policy updates based on identified threats and your unique needs. Mobile Threat Prevention’s cloud-based dashboard provides full visibility in to the threats impacting your environment and integrates all of this intelligence with existing systems like SIEM for added value and peace of mind.To learn more, visit checkpoint.com/mobilesecurity today.
развернуть свернуть