Check Point: Secure your Mobile Phone Now | Introducing SandBlast Mobile, Check Point: Mobile Security HD

00:02:05
Обнаружено блокирование рекламы на сайте
Для существования нашего сайта необходим показ рекламы. Просим отнестись с пониманием и добавить сайт в список исключений вашей программы для блокировки рекламы (AdBlock и другие).
Check Point Software Technologies, Ltd. 360 роликов
2873 просмотра на сайте 12n.ru
Secure your Mobile Phone Now | Introducing SandBlast Mobile.
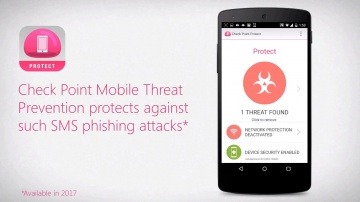
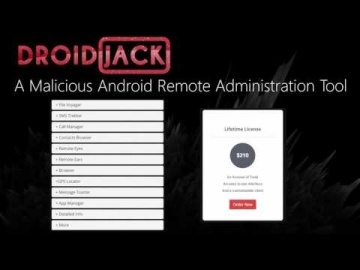
Protecting your enterprise from mobile threats and cyber attacks. More information: Worried about your Mobile Privacy? Secure your mobile phone now against mobile threats. Keeping your business safe from cyberattacks is no easy task, and the increased use of personal smartphones and tablets in the workplace has made it even harder. Cybertheives know your employees are often the weakest link in your organization's security. With a single attack, these cyber criminals can get inside operating systems, networks, and apps to take, monitor, or even change sensitive business data. The best defense against these attacks is a comprehensive mobile security solution that protects you against all three major vectors of attack. Watch this video to learn more about how SandBlast Mobile can keep mobile devices and data protected from cyber crime.
развернуть свернуть