- Видео
- Технологии
- Безопасность
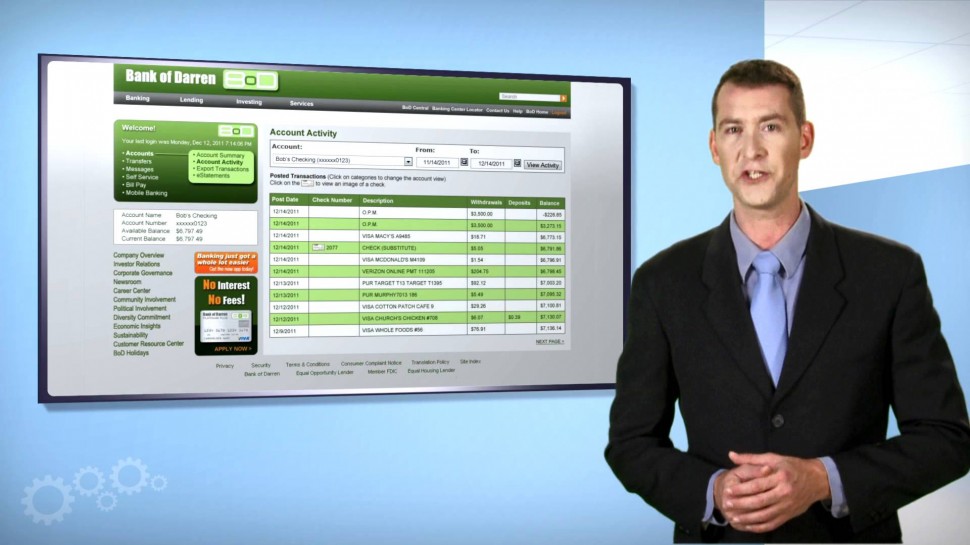
- Check Point: Protecting Against Spy Eye Bot | Network Security
Check Point: Protecting Against Spy Eye Bot | Network Security, Check Point: How-to and Tutorials HD
00:03:31
Обнаружено блокирование рекламы на сайте
Для существования нашего сайта необходим показ рекламы. Просим отнестись с пониманием и добавить сайт в список исключений вашей программы для блокировки рекламы (AdBlock и другие).
-

Check Point: Technical Assistance Center | Network Security Support
Check Point Software Technologies, Ltd. 00:02:24 -

Check Point: R80.10 Best Practices – Migrating from R77.30
Check Point Software Technologies, Ltd. 00:23:09 -

Check Point: SandBlast Mobile: Quick Start Guide | Tech Bytes
Check Point Software Technologies, Ltd. 00:04:00 -

Check Point: Anti-Ransomware: Solution Brief & Demo | Tech Bytes
Check Point Software Technologies, Ltd. 00:04:30 -
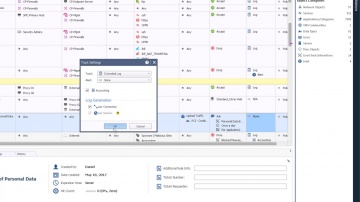
Check Point: Start Building Your Unified Policy with R80.10 | Security Management | Tech Bytes
Check Point Software Technologies, Ltd. 00:05:27 -
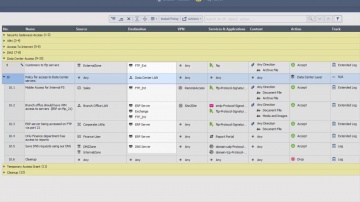
Check Point: R80.10 SmartConsole Security Policies View | Threat Prevention
Check Point Software Technologies, Ltd. 00:04:47 -
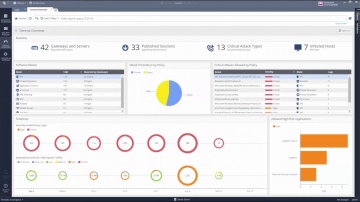
Check Point: R80.10 Security Management | Tech Bytes: Gateways, Logs, and Manage & Settings
Check Point Software Technologies, Ltd. 00:04:32 -
Check Point: Automating vSEC in OpenStack | Tech Bytes
Check Point Software Technologies, Ltd. 00:02:14 -

Check Point: Tutorial: Configuring Application Control
Check Point Software Technologies, Ltd. 00:04:01 -

Check Point: Tutorial: Configuring IPS Settings with R80 Security Management Server | Advanced Threa
Check Point Software Technologies, Ltd. 00:03:30 -
Check Point: Creating Host Objects with R80 Management API Tutorial | Security Management Tutorial
Check Point Software Technologies, Ltd. 00:07:14 -

Check Point: Analyst, Third Party Testing Validations 2014
Check Point Software Technologies, Ltd. 00:04:19 -
Check Point: SMB Cyber Security - 600 Appliance Setup
Check Point Software Technologies, Ltd. 00:04:19 -

Check Point: Software - 20 Years of Innovation
Check Point Software Technologies, Ltd. 00:03:53 -

Check Point: Next Generation Firewall, How To Choose The Right One | Network Security
Check Point Software Technologies, Ltd. 00:05:29 -

Check Point: Compliance Software Blade - Regulatory Compliance
Check Point Software Technologies, Ltd. 00:06:03 -
Check Point: Your Second Pair of Eyes - Compliance Software Blade | Network Security
Check Point Software Technologies, Ltd. 00:02:38 -
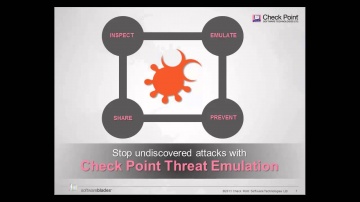
Check Point: Threat Emulation Explained by | Advanced Threat Prevention
Check Point Software Technologies, Ltd. 00:03:59 -

Check Point: Do You Know What's Hiding On Your Network?
Check Point Software Technologies, Ltd. 00:15:01 -
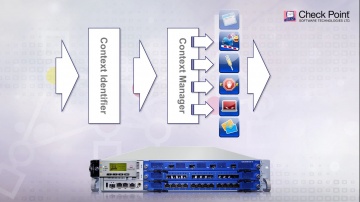
Check Point: Choose the Right Next Generation Firewall - Multi-Layer Security
Check Point Software Technologies, Ltd. 00:03:11 -

Check Point: ThreatCloud | Complete Cyber Security Intelligence Infrastructure | Network Security
Check Point Software Technologies, Ltd. 00:04:08 -
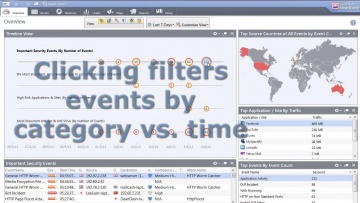
Check Point: SmartEvent | Security Management Walk-Through
Check Point Software Technologies, Ltd. 00:04:23 -
Check Point: Q&A: Compliance and Regulations with Jeremy Kaye | Network Security Risk and Compliance
Check Point Software Technologies, Ltd. 00:43:43 -

Check Point: Choosing the Right Next Generation Firewall | NGFW Explained
Check Point Software Technologies, Ltd. 00:03:04 -
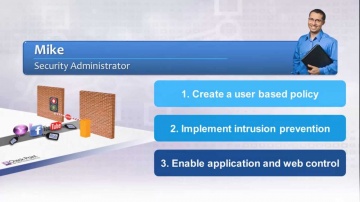
Check Point: A Day in the Life of Mike, a Next Generation Firewall Administrator
Check Point Software Technologies, Ltd. 00:03:49 -

Check Point: Compliance Software Blade | Network Security Best Practices
Check Point Software Technologies, Ltd. 00:03:58 -
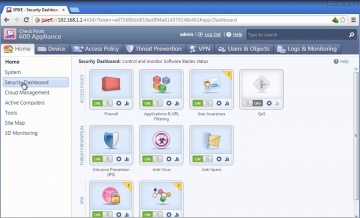
Check Point: 600 Appliance Setup
Check Point Software Technologies, Ltd. 00:04:19 -

Check Point: Denial of Service Cyber Attack Protector Overview
Check Point Software Technologies, Ltd. 00:05:30 -

Check Point: Third Party Security Validation | Threat Prevention
Check Point Software Technologies, Ltd. 00:03:20 -
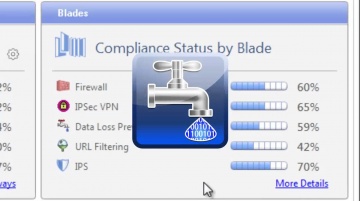
Check Point: Compliance Software Blade Demonstration
Check Point Software Technologies, Ltd. 00:07:07 -
Check Point: DDoS Protector - Technical Overview | DDoS Protection
Check Point Software Technologies, Ltd. 00:03:59 -

Check Point: Next-Generation Secure Web Gateway | Network Security
Check Point Software Technologies, Ltd. 00:04:43 -

Check Point: Overview of the 61000 Appliance - with Japanese subtitles
Check Point Software Technologies, Ltd. 00:07:01 -

Check Point: Overview of the 61000 Appliance | Data Center Security Systems
Check Point Software Technologies, Ltd. 00:07:01 -
Check Point: Protecting Against Spy Eye Bot | Network Security
Check Point Software Technologies, Ltd. 00:03:31 -
Check Point: 's SSL Inspection Technology | Enterprise Network Security
Check Point Software Technologies, Ltd. 00:07:06 -

Check Point: The Threat of Bots and Botnets | IoT | Network Security
Check Point Software Technologies, Ltd. 00:03:43 -
Check Point: Advanced Network Security: New Anti-Bot Software Blade
Check Point Software Technologies, Ltd. 00:03:18 -

Check Point: Unveils New Network Security Appliance Models
Check Point Software Technologies, Ltd. 00:06:47 -

Check Point: Cyber Security Plays Offense | Cyber Security
Check Point Software Technologies, Ltd. 00:03:02 -

Check Point: Makes DLP Work | Data Loss Prevention
Check Point Software Technologies, Ltd. 00:02:39 -

Check Point: IPS Software Blade
Check Point Software Technologies, Ltd. 00:01:34 -

Check Point: Best VPN Implementation | Security Management | Network Security
Check Point Software Technologies, Ltd. 00:09:04 -
Check Point: Threat Emulation Explained by | Advanced Threat Prevention
Check Point Software Technologies, Ltd. 00:03:59 -

Check Point: Do You Know What's Hiding On Your Network?
Check Point Software Technologies, Ltd. 00:15:01 -
Check Point: Choose the Right Next Generation Firewall - Multi-Layer Security
Check Point Software Technologies, Ltd. 00:03:11
Check Point Software Technologies, Ltd. 360 роликов
3151 просмотр на сайте 12n.ru
Protecting Against Spy Eye Bot | Network Security.
For more information: Learn how to protect against Spy Eye bot
× Отменить
развернуть свернуть
- 1 комментарий
RSS
Jacqueline RED25
01:39
# ↓
+1
HOW TO STAY SAFE FROM SPYEYE










