Check Point: IPS Software Blade, Check Point: How-to and Tutorials

00:01:34
Обнаружено блокирование рекламы на сайте
Для существования нашего сайта необходим показ рекламы. Просим отнестись с пониманием и добавить сайт в список исключений вашей программы для блокировки рекламы (AdBlock и другие).
Check Point Software Technologies, Ltd. 360 роликов
4217 просмотров на сайте 12n.ru
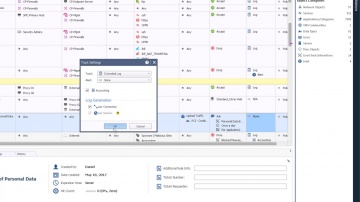
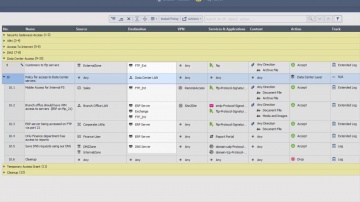
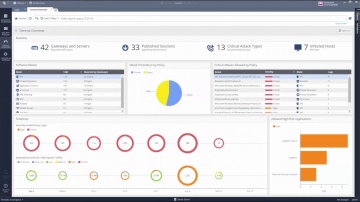
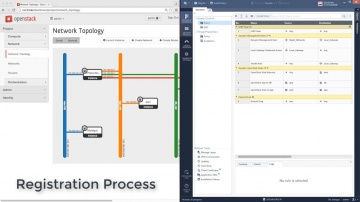
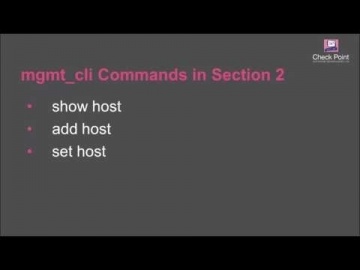
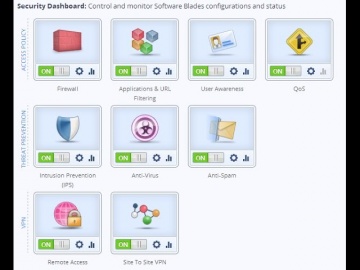
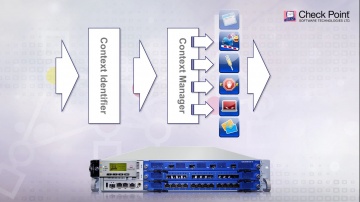
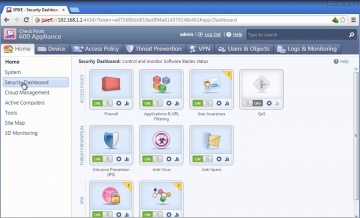
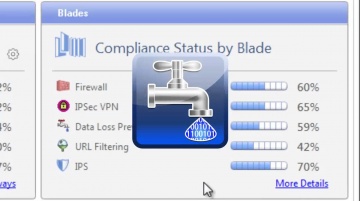
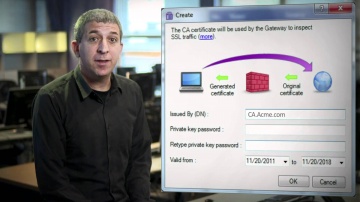
IPS Software Blade.
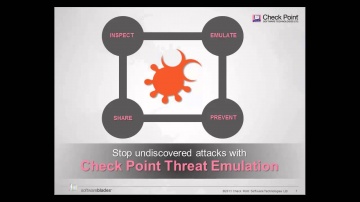
SSL Certificates attacks can compromise even the most secure sites. Learn how s IPS solutions protect against this specific kind of threats.
развернуть свернуть