Check Point: Next Generation Firewall, How To Choose The Right One | Network Security, Check Point: How-to and Tutorials HD

00:05:29
Обнаружено блокирование рекламы на сайте
Для существования нашего сайта необходим показ рекламы. Просим отнестись с пониманием и добавить сайт в список исключений вашей программы для блокировки рекламы (AdBlock и другие).
Check Point Software Technologies, Ltd. 360 роликов
17250 просмотров на сайте 12n.ru
Next Generation Firewall, How To Choose The Right One | Network Security.
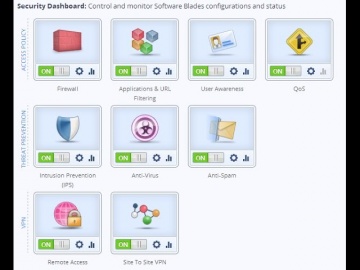
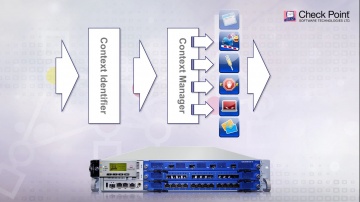
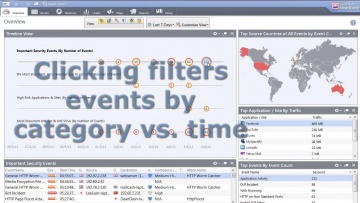
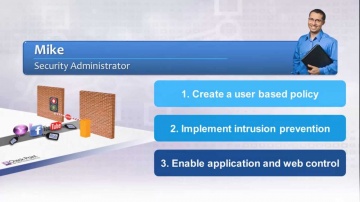
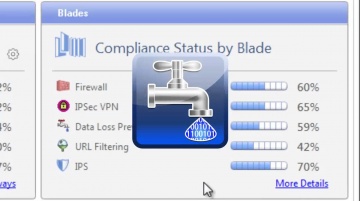
What questions should you ask when choosing the right network security protection in an integrated next generation firewall platform? For more information: provides customers of all sizes with the latest data and network security protection in an integrated next generation firewall platform, reducing complexity and lowering the total cost of ownership. Whether you need next-generation security for your data center, enterprise, small business or home office, has a cyber security solution for you.Cloud | cyber security: CloudGuard products protect assets in the cloud from the most sophisticated threats with dynamic scalability, intelligent provisioning and consistent control across physical and virtual networks. Data Center | cyber security: ’s data center security solutions provide a comprehensive security architecture with flexible enforcement points for advanced protection against the latest cyberattacks.Midsize & Enterprise | cyber security: Enterprises deploy security along well defined boundaries at the perimeter and internally within software defined data centers. has next generation firewall solutions for protecting both north-south and east-west traffic.Small Business | cyber security: has an affordable, easy to use and effective solution to secure small businesses. This includes turn-key appliances and a cloud-based Managed Security Service option, giving you the freedom to focus on growing your business.Consumer & Home Office | cyber security: ZoneAlarm, our award-winning product used by more than 90 million people, is the smart choice for protecting your computer from online threats.
развернуть свернуть