Безопасность
218 роликов  Data Loss Prevention - DLP - ПО для предотвращения утечек конфиденциальной информации/данных.
Data Loss Prevention - DLP - ПО для предотвращения утечек конфиденциальной информации/данных.
 Data Loss Prevention - DLP - ПО для предотвращения утечек конфиденциальной информации/данных.
Data Loss Prevention - DLP - ПО для предотвращения утечек конфиденциальной информации/данных. Предотвращение утечки данных, DLP
Обеспечение информационной безопасности, борьба с киберпреступностью. ИТ-безопасность.
GroupIB: Тенденции и прогнозы киберугроз
Ежегодное исследование Group-IB — Hi-Tech Crime Trends 2017 —
Cмотреть видео
Cмотреть видео
GroupIB: ICO – новая цель для хакеров
Ежегодное исследование Group-IB — Hi-Tech Crime Trends 2017 —
Cмотреть видео
Cмотреть видео
GroupIB: Продажа фальшивых полисов ОСАГО в интернете
ТВ Центр, программа «Городское собрание», январь 2016 В России участились случаи продажи поддельных полисов ОСАГО и постепенно география продаж плавно перемещается из фургончиков в интернет-пространство. Мошенники запускают сайты, где откр...
Cмотреть видео
Cмотреть видео
GroupIB: Киберугрозы для банков
Ежегодное исследование Group-IB — Hi-Tech Crime Trends 2017 —GroupIB: Киберугрозы для банков
Cмотреть видео
Cмотреть видео
GroupIB: О компании
Узнавайте об угрозах, утечках, взломах и хакерской активности до того, как они смогут вам навредить. Российский поставщик Threat Intelligence, вошедший в топ мировых рейтингов Gartner, IDC и Forrester.
Cмотреть видео
Cмотреть видео
GroupIB: Советы по безопасной работе ребенка в интернете
ParentChannel.Ru "Родители должны объяснить ребенку, что интернет, как и улица, это среда, которая может быть опасной для него, для его личной безопасности, для его эмоционального состояния", - основатель и гендиректор компании Group-IB ИЛ...
Cмотреть видео
Cмотреть видео
GroupIB: Group IB CyberCrimeCon 2017
Узнавайте об угрозах, утечках, взломах и хакерской активности до того, как они смогут вам навредить. Российский поставщик Threat Intelligence, вошедший в топ мировых рейтингов Gartner, IDC и Forrester.
Cмотреть видео
Cмотреть видео
GroupIB: Современные способы отъёма денег у населения в Интернете
По оценке экспертов только за год киберпреступники украли 2,5 млрд. долларов. Какие существуют способы обмана в интернете, рассказывает Сергей Никитин, эксперт Group-IB
Cмотреть видео
Cмотреть видео
GroupIB: В школьной программе может появиться новый обязательный предмет по кибербезопасности
Life News, 18.02.2015 В школьной программе может появиться новый обязательный предмет по кибербезопасности – основы информационной безопасности. С такой инициативой выступил Илья Сачков, сопредседатель комиссии по кибербезопасности РАЭК и г...
Cмотреть видео
Cмотреть видео
GroupIB: Президент России Владимир Путин ознакомился с решением Bot-Trek Cyber Intelligence
Президент РФ Владимир Путин во время посещения форума "Территория смыслов 2015" познакомился с ведущими разработками специалистов в области IT-технологий. На стенде Group-IB и ФРИИ главе государства продемонстрировали уникальную разработку...
Cмотреть видео
Cмотреть видео
GroupIB: Threat Intelligence — киберразведка по подписке
Узнавайте об угрозах, утечках, взломах и хакерской активности до того, как они смогут вам навредить. Первый российский поставщик Threat Intelligence, вошедший в топ мировых рейтингов Gartner, IDC и Forrester. Подпишитесь бесплатно на 14...
Cмотреть видео
Cмотреть видео
GroupIB: Как не стать жертвой виртуального мошенничества
Канал Москва 24 Интернет все чаще стали использовать мошенники для незаконного обогащения. Одни аферисты дистанционно снимают деньги с банковских карт, другие "зарабатывают" шантажом. О том, как не стать жертвой виртуального обмана, смотрит...
Cмотреть видео
Cмотреть видео
GroupIB: Обзор новых угроз ИБ, подробности расследований Group-IB и уязвимостях разных платформ
Сергей Никитин, заместитель руководителя лаборатории компьютерной криминалистики Group-IB, дал интервью программе "Персоналии ИКТ" и рассказал про новые угрозы и тренды высокотехнологичных преступлений, раскрыл подробности некоторых расслед...
Cмотреть видео
Cмотреть видео
GroupIB: Threat Intelligence rated by Gartner, IDC, Forrester
Prevent cyber attacks with Threat Intelligence — an effective tool to counter against targeted attacks and data breaches as well as effectively manage information security risks. Group-IB is a leading cyber threat intelligence provide...
Cмотреть видео
Cмотреть видео
GroupIB: Фальшивые авиабилеты в сети интернет
Россия 1. Специалисты по кибербезопасности Group-IB констатируют в интернете новый всплеск мошенничества с авиабилетами: в сезон отпусков каждую неделю появляются десятки сайтов-двойников и страничек однодневок, где продают липовые электрон...
Cмотреть видео
Cмотреть видео
GroupIB: CyberCrimeCon 2017 — конференция Group-IB о тенденциях киберугроз
*English below CyberCrimeCon 2017 — крупнейшая в России конференция по информационной безопасности: 14 звездных спикеров, 1000+ участников, актуальные проблемы, тренды и прогнозы. Спасибо всем, кто был с нами! Скачать ежегодный отчет об ак...
Cмотреть видео
Cмотреть видео
GroupIB: Нигерийские письма счастья
ТВ Центр. Программа "Полезная экономика" Нигерийские письма - это один из видов очень распространённого мошенничества в сети Интернет. Эксперт компании Group-IB Сергей Никитин дал несколько полезных советов, как рассмотреть уловку и не поп...
Cмотреть видео
Cмотреть видео
GroupIB: Как выбрать правильный сайт для покупки авиабилетов
Каждый день в интернете появляются мошеннические сайты, который продают фальшивые билеты. На что стоит обратить внимание, выбирая сайт для покупки авиабилетов? Первое - загляните на ресурс настоящийбилет.рф, который запустили трэвел-компан...
Cмотреть видео
Cмотреть видео
GroupIB: Один день из жизни Ильи Сачкова, основателя Group-IB.
Group-IB — международная высокотехнологичная компания, ведущий разработчик решений по предотвращению и расследованию преступлений в сфере высоких технологий. Один из мировых лидеров Threat Intelligence-решений (Киберразведка).
Cмотреть видео
Cмотреть видео
GroupIB: Топ-5 способов кражи денег с банковских карт
Повсеместное использование пластиковых карточек привлекает многих мошенников, они постоянно находят все новые способы, чтобы добывать информацию о пластиковых картах и снимать с них деньги. Специалисты Group-IB – специализирующейся на ...
Cмотреть видео
Cмотреть видео
GroupIB: "Ограбление века" группировкой хакеров Anunak (Carbanak)
Вести 24, программа Вести.net 16 февраля был выпущен отчет о деятельности хакеров из группировки Карбанак (Carbanak), известные так же как Anunak, и предположительно имеющие российские корни. Они сумели ограбить более 100 банков в 30 страна...
Cмотреть видео
Cмотреть видео
Layta: Сравнительное видео с обычных и тепловизионных камер AXIS
Сравнительное видео с обычных и тепловизионных камер AXIS. Ссылки на тепловизионные камеры:
Cмотреть видео
Cмотреть видео
Layta: D-Link DCS-2210 (дневная съемка) - IP-камера видеонаблюдения миниатюрная беспроводная
Пример записи камер серии D-Link DCS-2210 в дневное время. Ссылки на камеры:
Cмотреть видео
Cмотреть видео
Layta: Монтаж электронной проходной PERCo KTC01
Монтаж и ввод в эксплуатацию электронных проходных PERCo KTC01. #СКУД #Электронная_проходная #PERCo
Cмотреть видео
Cмотреть видео
Layta: IronLogic Z-5R Web особенности и конфигурирование сетевого контроллера
Ссылка на оборудование:
Cмотреть видео
Cмотреть видео
Layta: Светильник светодиодный Световые технологии BELL/S
Обзор светодиодных светильников акцентирующего света высокой мощности – BELL LED и JET LED. Светильники отличаются высокой технологичностью и функциональностью. А благодаря лаконичному дизайну идеально впишутся в дизайн-концепцию любого сов...
Cмотреть видео
Cмотреть видео
Layta: IronLogic Z-595 - Электронный замок
IronLogic Z-595 - Электронный замок Z-595 EHT- это считыватель бесконтактных ключей и контроллер с питанием от 1шт. батарейки крона 9V. Одного заряда батарейки будет хватать на 20000 открываний или около 2,5 года в режиме ожидания. Уникальн...
Cмотреть видео
Cмотреть видео
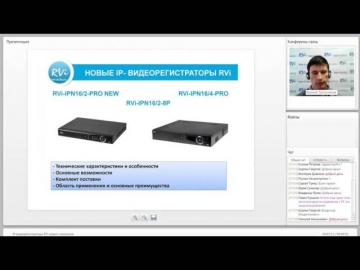
Layta: Вебинар 'IP видеорегистраторы RVi нового поколения' 26.08.2014
Вебинар посвящен IP-видеорегистраторам RVi-IPN16/2-PRO NEW, RVi-IPN16/4-PRO и RVi-IPN16/2-8P. Будут рассмотрены: - Технические характеристики и особенности - Основные возможности - Комплект поставки - Область применения и основные преимущес...
Cмотреть видео
Cмотреть видео