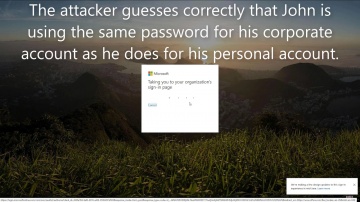
Безопасность
218 роликов  Data Loss Prevention - DLP - ПО для предотвращения утечек конфиденциальной информации/данных.
Data Loss Prevention - DLP - ПО для предотвращения утечек конфиденциальной информации/данных.
 Data Loss Prevention - DLP - ПО для предотвращения утечек конфиденциальной информации/данных.
Data Loss Prevention - DLP - ПО для предотвращения утечек конфиденциальной информации/данных. Предотвращение утечки данных, DLP
Обеспечение информационной безопасности, борьба с киберпреступностью. ИТ-безопасность.
DLP: TEC37 E16: Top Considerations When Building Your Security Architecture - видео
How do you know if your cybersecurity investments are being made in the right areas? Our collective rush to remote work has exposed additional surface ripe for security attacks. Spending may be also be on the rise but, hopefully, not at the...
Cмотреть видео
Cмотреть видео
GroupIB: RedCurl. The pentest you didn’t know about
Group-IB has released a report on the previously unknown APT group RedCurl, which focuses on corporate espionage. In less than three years, RedCurl attacked dozens of targets all over the world — from Russia to Canada. A presumably Ru...
Cмотреть видео
Cмотреть видео
GroupIB: Fxmsp: The untold story of infamous seller of access to corporate networks
Group-IB, a Singapore-based cybersecurity company, has issued a comprehensive report on Fxmsp – a heavyweight of the Russian-speaking cyber underground who made a name for himself selling access to corporate networks. Group-IB researchers a...
Cмотреть видео
Cмотреть видео
Digital Security: RDS mulpitle connections error to shell demo
Читайте статью, для которой записано демо: https://dsec.ru/blog/remote-desktop-glazami-atakuy...
Cмотреть видео
Cмотреть видео
GroupIB: Group-IB Secure Bank - client-side online fraud prevention in real time
Client-side fraud and attack prevention across sessions, platforms, and devices in real time for online & mobile banking.
Cмотреть видео
Cмотреть видео
GroupIB: Group-IB Secure Portal - client-side fraud prevention in real time
Prevention of client-side fraud and attacks across sessions, platforms, and devices in real time for online & mobile banking, ecommerce, and other online portals.
Cмотреть видео
Cмотреть видео
GroupIB: Graph Network: Group-IB has launched a new tool, which helps to predict and attribute attac
Group-IB has launched a new tool (https://www.group-ib.com/ti/graph.html) for clients, which helps to predict and attribute attacks, even before they can occur. The company has granted its clients access to the company’s internal tool ...
Cмотреть видео
Cмотреть видео
GroupIB: Ransomware Revival: Troldesh becomes a leader by the number of attacks
Group-IB, a Singapore-based cybersecurity company: ransomware accounted for over a half of all malicious mailings in H1 2019, detected and analyzed by Group-IB’s Computer Emergency Response Team (CERT-GIB), with Troldesh being the most popu...
Cмотреть видео
Cмотреть видео
НПЦ "БизнесАвтоматика": Visary Platform - видео
Visary is a unique platform solution for building complex and secure information and analytical systems, meets all the requirements of the Federal Security Service, Federal Service for Technical and Export Control and the Russian Ministry o...
Cмотреть видео
Cмотреть видео
GroupIB: Brand Protection - brand protection driven by cybersecurity innovations
Group-IB Brand Protection is a solution designed to detect and eliminate threats to your brand on the Internet. We prevent financial and reputational damage caused to businesses by brand abuse, Internet fraud, online piracy, and counterfei...
Cмотреть видео
Cмотреть видео
GroupIB: Group-IB Anti-Piracy - smart protection of digital content
Group-IB Anti-Piracy helps right holders combat piracy on the Internet and prevent the distribution of copied content online. Save your profits and develop legal distribution channels!
Cмотреть видео
Cмотреть видео
Check Point: CheckMates TechTalk: Analysis of SiliVaccine
SiliVaccine is an Anti-Virus tool used in North Korea. Security Researchers at got a copy of it to see if it had any abnormal behavior or undocumented features. Sure enough, it did!
Cмотреть видео
Cмотреть видео
L3 ProVision 2
Система ProVision 2 с функцией Автоматического Обнаружения Опасных предметов характеризуется таким же отличным качеством обнаружения опасных предметов и высокой пропускной способностью на контрольных пунктах в аэропортах, как и широко распр...
Cмотреть видео
Cмотреть видео
Check Point: You Asked, CEO Gil Shwed Answers!
Is Gil Shwed a morning person or a night owl? CEO Gil Shwed talks about his favorite apps, drones, future roadmap, and recognizes the winners in our CheckMates Birthday Awards!
Cмотреть видео
Cмотреть видео
Check Point: CheckMates TechTalk: Remote Code Execution Vulnerability on LG Smartphones
Neatsun Ziv and Jonathan Shimonovich discuss our recent publication of vulnerabilities that reside in the default keyboard of all mainstream LG smartphone models. More details:
Cмотреть видео
Cмотреть видео
Check Point: You Asked, VP of Products Dorit Dor Answers!
Is Dr. Dorit Dor a morning person or a night owl? Our VP of Products talks about her favorite apps, drones, future roadmap, and recognizes the winners in our CheckMates Birthday Awards!
Cмотреть видео
Cмотреть видео
Check Point: CheckMates First Birthday Award Winners
CheckMates, the user community for customers and partners, is celebrating it's first birthday by recognizing excellent contributors and content!
Cмотреть видео
Cмотреть видео
Check Point: Lightboard Series: Dynamic Revisions
This video elaborates on the logic behind the R80.10 Security Management architecture focusing on the dynamic revisions feature. This feature automatically stores the full history of database changes, with very little footprint, consuming ...
Cмотреть видео
Cмотреть видео
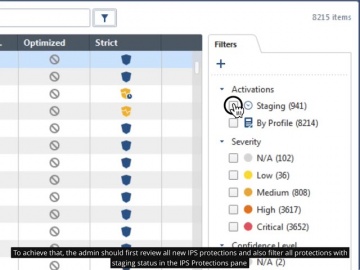
Check Point: R80.10 Policy Management – IPS Protections in Detect (Staging) State
This video elaborates on the logic behind new IPS protections status after IPS update operation and introduces best practice on changing the status of detect-staging on prevent when enough information was gathered regarding the new IPS prot...
Cмотреть видео
Cмотреть видео
Check Point: CloudGuard SaaS Demo Series: Identity Protection for Office 365
Watch this short demonstration video to learn how CloudGuard SaaS, an industry-first software-as-a-service (SaaS) security solution, provides advanced security and identity protection including account takeover protection for SaaS applicat...
Cмотреть видео
Cмотреть видео
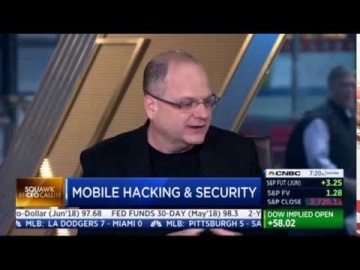
Check Point: Founder & CEO Gil Shwed on CNBC Squawk Box
CNBC Squawk Box featured Check Point CEO & Founder Gil Shwed. Gil Shwed discusses 5th generation cyber attacks. For more https://www.checkpoint.com/gen-v-cybe...Talking about level three attacks, level four attacks; what are fifth and s...
Cмотреть видео
Cмотреть видео
Check Point: EU GDPR Webinar Replay
The European Union’s General Data Protection Regulation (‘GDPR’) poses the biggest change to the regulatory landscape of data privacy. To learn more visit: GDPR places significant policy and technical responsibilities on ANY organization ...
Cмотреть видео
Cмотреть видео
Check Point: Who's Responsible for your Cloud Security?
A full breakdown of what is shared responsibility and the layers of security needed to protect you from security breaches in the cloud. For more information:
Cмотреть видео
Cмотреть видео
Check Point: The Mobile Threat Landscape
From Judy to Blueborne, the proliferation of mobile threats has grown rapidly in the past year. In this session, we review the various types of mobile threats, how they spread and the damage they cause. We will also be providing practical ...
Cмотреть видео
Cмотреть видео
Check Point: SMB Security Unique Challenges
The Small and Medium Business market has the same security challenges as larger enterprises. What they don't have a lot of is time or money.
Cмотреть видео
Cмотреть видео
Check Point: GDPR Recommendations for Data Privacy
Coming into effect in May 2018, the European Union’s General Data Protection Regulation (‘GDPR’) poses the biggest change to the regulatory landscape of data protection and privacy.
Cмотреть видео
Cмотреть видео
Check Point: Orchestrating Gateway Operations
In this session, we will take you through some of the operations that are performed on gateways that are not the typical rule base changes.
Cмотреть видео
Cмотреть видео
Check Point: Mobile Security: Configuration and Policy Management Best Practices
What is your mobility policy? Have you ever considered the impact of your mobility policy on your organization? On your employees? Whether it is BYOD, CYOD or corporate owned, traditional mobile management will not cover the security aspe...
Cмотреть видео
Cмотреть видео
Check Point: L’Oréal vSEC Case Study
As one of the world’s leading beauty brands, the L'Oréal group has spent the last century in the pursuit of perfection.
Cмотреть видео
Cмотреть видео
Check Point: Infinity - A Day in the Life of a Security Administrator
Having worked with access control as a basic security level for over 20 years, the speakers reminisce about how much better it was in the past.
Cмотреть видео
Cмотреть видео