- Видео
- Технологии
- Безопасность
- Check Point: IPS Software Blade
Check Point: IPS Software Blade, Check Point: Through the Years

00:01:34
Обнаружено блокирование рекламы на сайте
Для существования нашего сайта необходим показ рекламы. Просим отнестись с пониманием и добавить сайт в список исключений вашей программы для блокировки рекламы (AdBlock и другие).
-
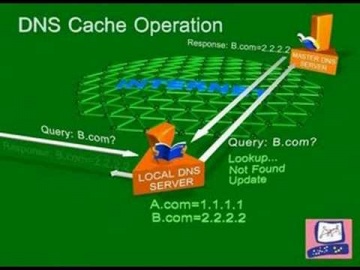
Check Point: DNS Cache Poisoning Attack | Internet Security
Check Point Software Technologies, Ltd. 00:01:45 -

Check Point: WebCheck
Check Point Software Technologies, Ltd. 00:05:31 -

Check Point: opens NASDAQ
Check Point Software Technologies, Ltd. 00:02:53 -

Check Point: ZoneAlarm vs. Windows 7
Check Point Software Technologies, Ltd. 00:03:38 -

Check Point: Best VPN Implementation | Security Management | Network Security
Check Point Software Technologies, Ltd. 00:09:04 -

Check Point: Choosing the right endpoint security solution
Check Point Software Technologies, Ltd. 00:05:57 -

Check Point: IPS Software Blade
Check Point Software Technologies, Ltd. 00:01:34 -

Check Point: Makes DLP Work | Data Loss Prevention
Check Point Software Technologies, Ltd. 00:02:39 -

Check Point: 3D Security.mov
Check Point Software Technologies, Ltd. 00:01:16 -

Check Point: Software Opens NASDAQ on 15th Year Anniversary of IPO
Check Point Software Technologies, Ltd. 00:09:18 -

Check Point: Data Centers Security Struggle
Check Point Software Technologies, Ltd. 00:02:37 -

Check Point: 3D Security
Check Point Software Technologies, Ltd. 00:02:07 -

Check Point: Cyber Security Plays Offense | Cyber Security
Check Point Software Technologies, Ltd. 00:03:02 -

Check Point: The Threat of Bots and Botnets | IoT | Network Security
Check Point Software Technologies, Ltd. 00:03:43 -
Check Point: Advanced Network Security: New Anti-Bot Software Blade
Check Point Software Technologies, Ltd. 00:03:18 -

Check Point: Unveils New Network Security Appliance Models
Check Point Software Technologies, Ltd. 00:06:47 -
Check Point: 's SSL Inspection Technology | Enterprise Network Security
Check Point Software Technologies, Ltd. 00:07:06 -
Check Point: Protecting Against Spy Eye Bot | Network Security
Check Point Software Technologies, Ltd. 00:03:31 -
Check Point: Milestones
Check Point Software Technologies, Ltd. 00:03:43 -

Check Point: Protected 24x7 With | Cyber Security
Check Point Software Technologies, Ltd. 00:02:44 -

Check Point: Anti-Bot Protection | IoT| Network Security
Check Point Software Technologies, Ltd. 00:02:00 -

Check Point: Overview of the 61000 Appliance | Data Center Security Systems
Check Point Software Technologies, Ltd. 00:07:01 -
Check Point: Denial of Service Attacks & How to Protect Against Them
Check Point Software Technologies, Ltd. 00:04:05 -

Check Point: Why Trust Matters for Security
Check Point Software Technologies, Ltd. 00:05:37 -

Check Point: Radio Interview Discussing 2013 Cyber Security Threats
Check Point Software Technologies, Ltd. 00:14:29 -

Check Point: Next-Generation Secure Web Gateway | Network Security
Check Point Software Technologies, Ltd. 00:04:43 -
Check Point: on National Czech Republic Television
Check Point Software Technologies, Ltd. 00:05:02 -
Check Point: DDoS Protector - Technical Overview | DDoS Protection
Check Point Software Technologies, Ltd. 00:03:59 -

Check Point: 2013 Security Report | Cyber Security
Check Point Software Technologies, Ltd. 00:02:08 -

Check Point: Third Party Security Validation | Threat Prevention
Check Point Software Technologies, Ltd. 00:03:20 -

Check Point: Denial of Service Cyber Attack Protector Overview
Check Point Software Technologies, Ltd. 00:05:30 -

Check Point: CRN Interviews Amnon Bar-Lev | Network Security
Check Point Software Technologies, Ltd. 00:05:19 -

Check Point: Compliance Software Blade | Network Security Best Practices
Check Point Software Technologies, Ltd. 00:03:58 -
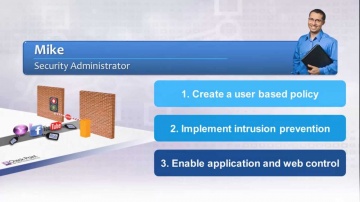
Check Point: A Day in the Life of Mike, a Next Generation Firewall Administrator
Check Point Software Technologies, Ltd. 00:03:49 -

Check Point: Choosing the Right Next Generation Firewall | NGFW Explained
Check Point Software Technologies, Ltd. 00:03:04 -
Check Point: Q&A: Compliance and Regulations with Jeremy Kaye | Network Security Risk and Compliance
Check Point Software Technologies, Ltd. 00:43:43 -
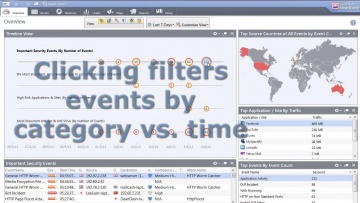
Check Point: SmartEvent | Security Management Walk-Through
Check Point Software Technologies, Ltd. 00:04:23 -

Check Point: ThreatCloud | Complete Cyber Security Intelligence Infrastructure | Network Security
Check Point Software Technologies, Ltd. 00:04:08 -
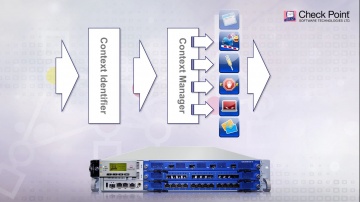
Check Point: Choose the Right Next Generation Firewall - Multi-Layer Security
Check Point Software Technologies, Ltd. 00:03:11 -

Check Point: Do You Know What's Hiding On Your Network?
Check Point Software Technologies, Ltd. 00:15:01 -
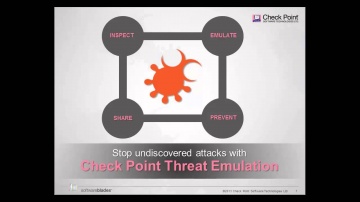
Check Point: Threat Emulation Explained by | Advanced Threat Prevention
Check Point Software Technologies, Ltd. 00:03:59 -
Check Point: Your Second Pair of Eyes - Compliance Software Blade | Network Security
Check Point Software Technologies, Ltd. 00:02:38 -

Check Point: Compliance Software Blade - Regulatory Compliance
Check Point Software Technologies, Ltd. 00:06:03 -

Check Point: Customer Success Video: MLB Network Maintains 100 Percent Network Uptime
Check Point Software Technologies, Ltd. 00:02:58 -

Check Point: Next Generation Firewall, How To Choose The Right One | Network Security
Check Point Software Technologies, Ltd. 00:05:29 -

Check Point: Introducing ThreatCloud Emulation Services | Cloud Security
Check Point Software Technologies, Ltd. 00:01:46 -
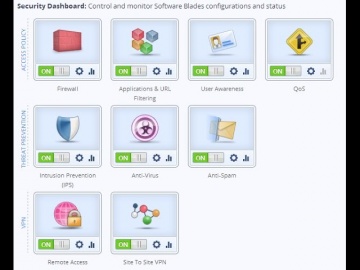
Check Point: SMB Cyber Security - 600 Appliance Setup
Check Point Software Technologies, Ltd. 00:04:19 -

Check Point: : Introducing Software-defined Protection | Cyber Security Software
Check Point Software Technologies, Ltd. 00:05:24 -

Check Point: Customer & Partner Insights- California DMV
Check Point Software Technologies, Ltd. 00:01:44 -

Check Point: Employee Testimonial - Why work at ?
Check Point Software Technologies, Ltd. 00:01:42
Check Point Software Technologies, Ltd. 360 роликов
4217 просмотров на сайте 12n.ru
IPS Software Blade.
SSL Certificates attacks can compromise even the most secure sites. Learn how s IPS solutions protect against this specific kind of threats.
× Отменить
развернуть свернуть
- 1 комментарий
RSS
Abdul Raheem
16:11
# ↓
Nice video










