Безопасность
218 роликов  Data Loss Prevention - DLP - ПО для предотвращения утечек конфиденциальной информации/данных.
Data Loss Prevention - DLP - ПО для предотвращения утечек конфиденциальной информации/данных.
 Data Loss Prevention - DLP - ПО для предотвращения утечек конфиденциальной информации/данных.
Data Loss Prevention - DLP - ПО для предотвращения утечек конфиденциальной информации/данных. Предотвращение утечки данных, DLP
Обеспечение информационной безопасности, борьба с киберпреступностью. ИТ-безопасность.
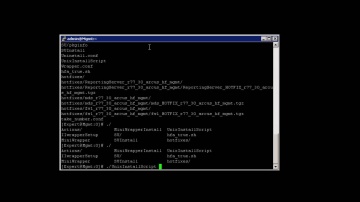
Check Point: Deployment Tools; DIY security appliance images using ISOmorphic
Deployment Tools; DIY security appliance images using ISOmorphic. For more information: In our second video on deployment tools we show you how to image Security Appliances and Open Servers. With the ISOmorphic utility you can inst...
Cмотреть видео
Cмотреть видео
Check Point: Customer & Partner Insights- FishNet Security
Learn More: speaks with customers and partners at RSA Conference 2014 in San Francisco. Watch as they share what makes them a fan.
Cмотреть видео
Cмотреть видео
Check Point: 01 Installing the Management Server Hotfix
Install the Hotfix on Gaia R77.30 Security Management Server and R77.20/R77.30 Security Gateways. It is required for both the vSEC Gateway and the vSEC Controller.
Cмотреть видео
Cмотреть видео
Check Point: Introducción a Compliance Blade
Introducción a Compliance Blade a Software
Cмотреть видео
Cмотреть видео
Check Point: Customer Success: Community Newspaper Group (CNG)
For More Information: Community Newspaper Groups seventeen newspapers provide readers with the latest in local news, sports, and entertainment in Perth, Australia. As a publishing outlet, its critical for Community Newspaper Group to kee...
Cмотреть видео
Cмотреть видео
Check Point: RSA Conference 2014 - Partner Insights - Avnet
Learn More: Gimv, a leading European private equity and venture capital investment company, leverages ThreatCloud Emulation technology to prevent against zero day attacks. Watch as IT Manager Kristof Poppe discusses his experience wi...
Cмотреть видео
Cмотреть видео
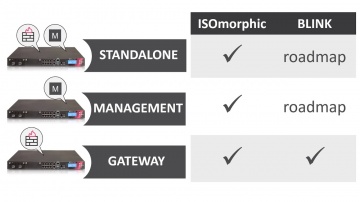
Check Point: Deployment Tools - ISOmorphic & Blink
Deploying Next Generation Firewalls just got easier with the introduction of the Blink utility. For more information: Blink creates a working snapshot of a cleanly installed security gateway with a completed First-Time Configuration Wizard...
Cмотреть видео
Cмотреть видео
Check Point: Ask Me Anything - How to Sell to a CISO
In this fireside chat with Jerry Pitman, CISO, Tenneco , will share what he looks for when meeting with security vendors and also the less effective sales pitches he experienced
Cмотреть видео
Cмотреть видео
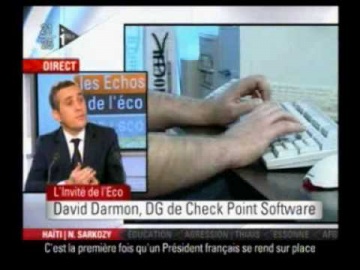
Check Point: Software commente les dernières tendances de la sécurité informatique en 2010
I Télé Les Echos de l'Eco David Darmon, Directeur General France de Software Technologies, lun des leaders mondiaux de la sécurité informatique, explique les tendances de la sécurité informatique en 2010 au vu des récents événements Inter...
Cмотреть видео
Cмотреть видео
Check Point: Entrevista a Juan Rivera, en el noticiero Buenos Dias Per̼
Juan Rivera, Gerente Regional de Cono Sur
Cмотреть видео
Cмотреть видео
Check Point: Stay One Step Ahead with SandBlast Zero-Day Protection
Watch this webcast to learn about SandBlast Zero-Day Protection, an innovative approach to stop unknown malware, zero-day and targeted attacks from infiltrating networks. More information: Zero-day protection offering network security wi...
Cмотреть видео
Cмотреть видео
Check Point: Helvetia Insurance : vSEC for NSXの導入事例
スイスで3番目に大きな保険会社Helvetia InsuranceのvSEC for NSXの導入事例です。保険とは信頼の上に成り立つビジネスなので、お客様の満足度は特に重要であり、セキュリティ対策に求めらるレベルも非常に高いです。ハイレベルなニーズに応えたのがチェック・ポイントのvSEC for NSXでした。
Cмотреть видео
Cмотреть видео
Check Point: Customer Quote: Uncovered Potential Risks with Security Checkup
Gimv IT Manager Kristof Poppe comments on 's Security Checkup report and how it influenced their decision to go with .
Cмотреть видео
Cмотреть видео
Check Point: Continuing Policy Work-in-Progress with R80.10 Session Take Over | Tech Bytes
R80.10 enables security administrators to work on the same policy at the same time. But what happens if a project needs to be finished and the security administrator is not available to do so? R80.10 Session Take Over feature allows for oth...
Cмотреть видео
Cмотреть видео
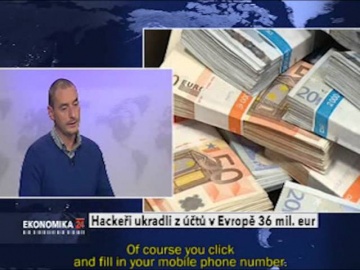
Check Point: on National Czech Republic Television
Eurograbber was launched against banking customers, using a sophisticated combination of malware directed at computers and mobile devices. For more information click here: The malware, in conjunction with the attackers' command and contr...
Cмотреть видео
Cмотреть видео
Check Point: How to Hack a Cell Phone | Demo for Understanding Mobile Security
Want to hack a Smartphone? A hands-on approach to understanding mobile security. Learn more here: Ever wanted to know how to hack a smartphone? Join this exciting live demo to see first-hand how easy it is! Learn more:
Cмотреть видео
Cмотреть видео
Check Point: Unveils New Network Security Appliance Models
Gabi Reish, Head of Product Management at Software Technologies, introduces the new 2012 line of Appliances. For more information: provides organizations of all sizes with the latest data and network security protection in an integrated...
Cмотреть видео
Cмотреть видео
Check Point: vSEC Advanced Security for Software-Defined Data Centers | Cloud Security
For more information visit: vSEC integration with VMware NSX delivers dynamic orchestration of advanced threat prevention for all traffic in the Software-Defined Data Center. Learn more
Cмотреть видео
Cмотреть видео
Check Point: Helvetia Insurance : vSEC for NSXの導入事例
スイスで3番目に大きな保険会社Helvetia InsuranceのvSEC for NSXの導入事例です。保険とは信頼の上に成り立つビジネスなので、お客様の満足度は特に重要であり、セキュリティ対策に求めらるレベルも非常に高いです。ハイレベルなニーズに応えたのがチェック・ポイントのvSEC for NSXでした。 For more information:
Cмотреть видео
Cмотреть видео
Check Point: Managing Security Policy Changes with R80.10 | Tech Bytes
When new services are introduced and your security policy needs to be adjusted accordingly, what tools will you be using? R80.10 makes it easier to implement changes. The “Where Used” and “Replace” tools will help security administrators ma...
Cмотреть видео
Cмотреть видео
Check Point: CRN Interviews Amnon Bar-Lev | Network Security
Amnon Bar-Lev talks to CRN about how to better target products for sales and that there should be a focus on evaluating existing network security architecture and protecting organizations.
Cмотреть видео
Cмотреть видео
Check Point: Entrevista a Francisco Robayo, sobre los delitos en la red Teleamazonas Ecuador
Francisco Robayo, Gerente IngenierÌ_a,
Cмотреть видео
Cмотреть видео
Check Point: 24/7 Protection with ThreatCloud Managed Security Service | Threat Prevention
For more information visit ThreatCloud Managed Security Service is a cloud-based service providing actionable attack alerts for IPS, Anti-Bot and Antivirus customers. experts remotely monitor, manage and escalate attack incidents. Custo...
Cмотреть видео
Cмотреть видео
Check Point: Microsoft Azure and CloudGuard - Intelligent Cloud Security - CPX 360 2018
In his keynote, Avi Ben Menahem, Director of Azure Security Microsoft will discuss what it takes to build and operate a secure cloud platform, the approach the team at Microsoft takes to secure Azure, and the importance of a strong develope...
Cмотреть видео
Cмотреть видео
Check Point: Advanced Network Security: New Anti-Bot Software Blade
Infinity is the first consolidated security across networks, cloud and mobile, providing the highest level of threat prevention. More information: provides organizations of all sizes with the latest data and network security protection i...
Cмотреть видео
Cмотреть видео
Check Point: Understanding SandBlast - Zero-Day Protection
Understanding your exposure to threats—and what you can do about it is not only responsible business management—it’s critical to business survival. More information: Turn Security into an Enabler, Not a Disabler. SandBlast Zero-Day Prote...
Cмотреть видео
Cмотреть видео
Check Point: - CNN Report a Gil Shwed (sub español)
CNN analiza en este informe la creación de Gil Shwed, , una empresa dedicada a la creación de soluciones en el ámbito de la seguridad informática.
Cмотреть видео
Cмотреть видео
Check Point: Jorge Steinfeld, Software; Entrevista en RPP TV
Software Technologies Ltd. — крупнейший в мире поставщик в области безопасности. Компания предлагает покупателям ведущие в индустрии решения и защищает покупателей от кибератак с непревзойденным уровнем успешного обнаружения вре...
Cмотреть видео
Cмотреть видео
Check Point: Building a Secure Platform as CIO - CPX 360 Keynote
In his keynote, Sharon Schusheim will discuss what it takes to build and operate a secure platform as a CIO. For more information: CPX 360 promises to be the premier cyber security summit. For the first time, we will bring our customers...
Cмотреть видео
Cмотреть видео