Безопасность
218 роликов  Data Loss Prevention - DLP - ПО для предотвращения утечек конфиденциальной информации/данных.
Data Loss Prevention - DLP - ПО для предотвращения утечек конфиденциальной информации/данных.
 Data Loss Prevention - DLP - ПО для предотвращения утечек конфиденциальной информации/данных.
Data Loss Prevention - DLP - ПО для предотвращения утечек конфиденциальной информации/данных. Предотвращение утечки данных, DLP
Обеспечение информационной безопасности, борьба с киберпреступностью. ИТ-безопасность.
Check Point: Customer Quote: ThreatCloud Emulation Discovers and Prevents Zero-Day Attacks
Gimv IT Manager Kristof Poppe comments on 's Threat Emulation and zero day attacks.
Cмотреть видео
Cмотреть видео
Check Point: 06 Creating a vSEC Gateway IP Address Pool
We recommend that you create pool for automatic assignment of management interface IP addresses.
Cмотреть видео
Cмотреть видео
Check Point: Why Trust Matters for Security
Following a press round table event held in London in December 2012, panelists looked at why trust is fundamental to security, and how organizations can prove that they and their employees can be trusted. The spokespeople are: - Kevin B...
Cмотреть видео
Cмотреть видео
Check Point: : A Founding Member of the AirWatch Mobile Security Alliance | Mobile Threat Prevention
President Amnon Bar-Lev addresses the audience during the keynote speech at AirWatch Connect 2015 in Atlanta on September 22, 2015, and announces ’s participation as a founding member of the AirWatch Mobile Security Alliance.
Cмотреть видео
Cмотреть видео
Check Point: SmartEvent | Security Management Walk-Through
Are you tired of managing security by manually searching through millions of logs to find the information you need? There is a better way! Watch this SmartEvent Video to learn how to manage your security more efficiently. For more informa...
Cмотреть видео
Cмотреть видео
Check Point: EU GDPR Webinar Replay
The European Union’s General Data Protection Regulation (‘GDPR’) poses the biggest change to the regulatory landscape of data privacy. To learn more visit: GDPR places significant policy and technical responsibilities on ANY organization ...
Cмотреть видео
Cмотреть видео
Check Point: 05 Registering a vSEC Gateway Service and Host Preparation
Software Technologies Ltd. — крупнейший в мире поставщик в области безопасности. Компания предлагает покупателям ведущие в индустрии решения и защищает покупателей от кибератак с непревзойденным уровнем успешного обнаружения вре...
Cмотреть видео
Cмотреть видео
Check Point: RSA Conference 2014 - Partner Insights - Soluciones Seguras
Find out more: speaks with customers and partners at RSA Conference 2014 in San Francisco. Watch as Eli Fashka of Soluciones Seguras shares how they are using solutions with their customers. He also speaks to 's management and consol...
Cмотреть видео
Cмотреть видео
Check Point: CloudGuard SaaS Demo Series: Identity Protection for Office 365
Watch this short demonstration video to learn how CloudGuard SaaS, an industry-first software-as-a-service (SaaS) security solution, provides advanced security and identity protection including account takeover protection for SaaS applicat...
Cмотреть видео
Cмотреть видео
Check Point: Webinar replay – Auto-scale advanced security for Microsoft Azure
For more information visit: Webinar replay - hear from customer George Dialectakis, IT Consultant at Eversource Energy, on how they leverage CloudGuard IaaS advanced threat prevention security for their Microsoft Azure cloud environme...
Cмотреть видео
Cмотреть видео
Check Point: ThreatCloud | Complete Cyber Security Intelligence Infrastructure | Network Security
For more information: Introducing ThreatCloud, the first collaborative network to fight cyber-attacks.
Cмотреть видео
Cмотреть видео
Check Point: RSA Conference 2014 - Partner Insights - Dataway
Find out more: speaks with customers and partners at RSA Conference 2014 in San Francisco. Watch as Heather Zalatimo from partner Dataway shares thoughts about 's superior management capabilities and what makes her a fan.
Cмотреть видео
Cмотреть видео
Check Point: Threat Intelligence | Threat Prevention
Learn More: In 2012, established ThreatCloud, the first collaborative security infrastructure to fight cybercrime. ThreatCloud dynamically reinforces Threat Prevention Software Blades with real-time threat intelligence derived from res...
Cмотреть видео
Cмотреть видео
Check Point: 04 Installing the OVF Package and Configuring Global Parameters
Software Technologies Ltd. — крупнейший в мире поставщик в области безопасности. Компания предлагает покупателям ведущие в индустрии решения и защищает покупателей от кибератак с непревзойденным уровнем успешного обнаружения вре...
Cмотреть видео
Cмотреть видео
Check Point: CloudGuard SaaS Demo Series: Protecting Sensitive Data
For more information: Watch this short demonstration video to learn how CloudGuard SaaS, an industry-first software-as-a-service (SaaS) security solution, provides advanced security and sensitive data protection for SaaS applications such ...
Cмотреть видео
Cмотреть видео
Check Point: Capsule Docs - Secure Business Documents Everywhere | Network Security
Capsule Docs ensures that only authorized individuals can access your business documents. Confidently share documents with coworkers, business partners, clients, and vendors, because you are in control of their access and sharing rights.
Cмотреть видео
Cмотреть видео
Check Point: Choose the Right Next Generation Firewall - Multi-Layer Security
Why Multi-Layer Security and how 's Software Blade Architecture is the most secure and scalable solution in this market. For more information: provides organizations of all sizes with the latest data and network security protection in a...
Cмотреть видео
Cмотреть видео
Check Point: RSA Conference 2014 - Customer Insights - Leidos
Find out more: speaks with customers and partners at RSA Conference 2014 in San Francisco. Watch as Joseph Royal of Leidos shares what makes him a fan.
Cмотреть видео
Cмотреть видео
Check Point: 03 Adding the vCenter IP Address to the Runtime Settings
VMware requires you to add the vCenter IP address to the Runtime Settings tab on the vCenter Server Setting page
Cмотреть видео
Cмотреть видео
Check Point: Choose the Right Next Generation Firewall - Multi-Layer Security
Why Multi-Layer Security and how 's Software Blade Architecture is the most secure and scalable solution in this market. For more information: provides organizations of all sizes with the latest data and network security protection in a...
Cмотреть видео
Cмотреть видео
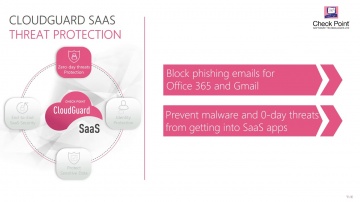
Check Point: Zero-day Threat Protection for SaaS Email | CloudGuard SaaS Demo
Demo showing how CloudGuard Saas provides advanced security and threat prevention for SaaS applications. For more information: Watch this short demonstration video to learn how CloudGuard SaaS, an industry-first software-as-a-service (Saa...
Cмотреть видео
Cмотреть видео
Check Point: Capsule Docs – Keep Your Business Documents Protected | Enterprise | Network Security
Capsule Docs protects your sensitive business documents to ensure they don’t get unintentionally exposed. See how Capsule Docs works to provide document security.
Cмотреть видео
Cмотреть видео
Check Point: Do You Know What's Hiding On Your Network?
This video summarizes the analysis and findings in the 2013 Security Report. For more information: provides organizations of all sizes with the latest data and network security protection in an integrated next generation firewall platfo...
Cмотреть видео
Cмотреть видео
Check Point: Do You Know What's Hiding On Your Network?
This video summarizes the analysis and findings in the 2013 Security Report. For more information: provides organizations of all sizes with the latest data and network security protection in an integrated next generation firewall platfo...
Cмотреть видео
Cмотреть видео
Check Point: RSA Conference 2014 - Customer Insights - Securities America, Inc.
Find out more: speaks with customers and partners at RSA Conference 2014 in San Francisco. Watch as Leon Johnson from Securities America, Inc. speaks about the critical need to secure data in the financial industry and how integrates ...
Cмотреть видео
Cмотреть видео
Check Point: 02 Configuring Agent VM
To use a local Datastore on multiple ESX hosts (recommended) for the vSEC Gateway, or to use a non-distributed vSwitch for vSEC Gateway communication to the Security Management Server, you must configure Agent VM settings
Cмотреть видео
Cмотреть видео
Check Point: Gen V Cyber Security with Moti Sagey - CPX 360
In his keynote, Moti Sagey will discuss in a pragmatic fact based way what it takes to build a Gen V security solution and how the cyber landscape matches the must have for effective security.
Cмотреть видео
Cмотреть видео
Check Point: Stop Advanced Mobile Threats Before They Start | SandBlast Mobile Security
Learn More: Report: IDC Technology Spotlight: Why Comprehensive Security Requires Mobile Threat Prevention: Cyber criminals may be stealing data from your smartphone or tablet without your knowledge. They’re experts at exploiting vulner...
Cмотреть видео
Cмотреть видео