Check Point: Malware Threat Prevention | Zero-Day, Zero-Second. → Похожие видео ролики , Страница 7
What can malware do in 60 seconds? One minute can change everything for a business. So what happens when the speed of business is overtaken by the speed of malware? The team devised a test to quantify that exact question. Learn More: As part of the SandBlast Zero-Day Protection solution, Threat Emulation prevents infections from new malware and targeted attacks. This innovative zero-day threat sandboxing capability within the SandBlast solution delivers the best possible catch rate for threats, and is virtually immune to attackers’ evasion techniques.
Подробнее в видео...
Подробнее в видео...
00:09:18
Check Point: Software Opens NASDAQ on 15th Year Anniversary of IPO
Founder, chairman and CEO, Gil Shwed, along with Tal Payne, the chief financial officer, and the company's board of directors participated in The NASDAQ Opening Bell ceremony at The NASDAQ Stock Market on Tuesday, June 28, 2011. The ceremon...
Cмотреть видео
Cмотреть видео
00:19:02
Check Point: Evolving Role of the CISO - A Customer Story
In this session, CISO Joey Smith will discuss his understanding of the importance of compliance and security and their differences. For more information: Additionally, he will review what he has personally learned from his experience as...
Cмотреть видео
Cмотреть видео
HD 00:02:13
Check Point: Daymark Secures Cloud with CloudGuard (formerly vSEC) for Microsoft Azure | Cloud Secur
Daymark solutions, trusted advisor to businesses in the Northeast, implemented CloudGuard (formerly vSEC) for Microsoft Azure and now recommends it to all its customers for ease of use, comprehensive visibility and threat prevention. Hea...
Cмотреть видео
Cмотреть видео
HD 00:02:13
Check Point: Daymark Secures Cloud with CloudGuard (formerly vSEC) for Microsoft Azure | Cloud Secur
Daymark solutions, trusted advisor to businesses in the Northeast, implemented CloudGuard (formerly vSEC) for Microsoft Azure and now recommends it to all its customers for ease of use, comprehensive visibility and threat prevention. Hea...
Cмотреть видео
Cмотреть видео
HD 00:02:00
Check Point: Anti-Bot Protection | IoT| Network Security
A bot is malicious software that allows cyber criminals to remotely control computers and execute illegal activities such as stealing data, spreading spam and distributing malware. More information: Anti-Bot security software detects bot...
Cмотреть видео
Cмотреть видео
HD 00:02:07
Check Point: ゼロデイの脅威からエンドポイントを保護するSandBlast Agent
脅威の進化に伴い、組織には、あらゆるレベルで攻撃を防ぎ、迅速に対応して被害を抑えるソリューションの導入が推奨されます。SandBlast Agentは、幅広い高度なエンドポイント保護技術により、社内および社外で利用するエンドポイントを保護します。攻撃の全体像をすばやく把握できるフォレンジック分析機能も搭載しており、インシデント・レスポンス・チームの生産性を最大限に高めます。
Cмотреть видео
Cмотреть видео
HD 00:06:29
Check Point: Globb TV interview: Amnon Bar-Lev
President Amnon Bar-Lev discusses the big business of today’s cybercrimes
Cмотреть видео
Cмотреть видео
HD 00:14:16
Check Point: Mal uso de las redes sociales Programa DÌ_a a DÌ_a Teleamazonas, Ecuador
Software Technologies Ltd. — крупнейший в мире поставщик в области безопасности. Компания предлагает покупателям ведущие в индустрии решения и защищает покупателей от кибератак с непревзойденным уровнем успешного обнаружения вре...
Cмотреть видео
Cмотреть видео
HD 00:04:19
Check Point: Analyst, Third Party Testing Validations 2014
Learn More: is excited to have received top awards from respected industry sources and certification bodies for its Next Generation Firewall, IPS and Threat Prevention Appliance products.
Cмотреть видео
Cмотреть видео
00:02:37
Check Point: Data Centers Security Struggle
Gil Shwed, CEO of Software, talks with James Rogers of TheStreet.com
Cмотреть видео
Cмотреть видео
HD 00:02:07
Check Point: R80 Enhances Efficiency at the University of Kansas
The University of Kansas tested R80 security management and liked what they saw. Today they enjoy increased operational efficiency through concurrent administration capabilities, APIs for automation and a single pane of glass.
Cмотреть видео
Cмотреть видео
HD 00:01:48
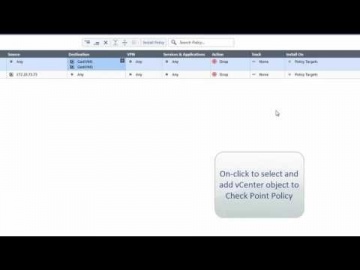
Check Point: vSEC controller Demo with R80 Smart Management | Cloud Security
This video demos the vSEC cloud security integration with VMware vCenter and NSX. It shows you how to integrate a vCenter server in the Smart Console, provision a security rule based on imported vCenter objects like VM name, integrate wit...
Cмотреть видео
Cмотреть видео
HD 00:02:11
Check Point: R80 Streamlines Security Management at Appvion | Data Center Security
Appvion, a manufacturer of specialty papers, tested R80 security management during development and now uses it every day to gain efficiency, high visibility and concurrent management capabilities.
Cмотреть видео
Cмотреть видео
HD 00:20:33
Check Point: We Make Jeans; How Hard Can That Be?
This talk will present some of the business challenges, experiences and road maps from a security perspective to protect the global Levi Brand. Steve Zalewski, Chief Security Architect, Levi Strauss For more information:
Cмотреть видео
Cмотреть видео
HD 00:01:15
Check Point: ââÑââÛâ»Ù¨â_Ä_ÄÝÎ_Ñ£ÐâäâÎÙâä
¾÷¬È_¨âµâ_ÄÄ__ø_»¨¾äÜ£ø_ª_ªá¤_ªÇ»â_Ûâ_Ä_Ä_ÄöÄ¥â©Ä_âãâÀÄÐÄÂÄÄÄöÜâ侩Ùø ¾ÄÉʱâÕã¬ââ¡Á÷ÇÝÑÀà¼Ñ_ªÛââµâ_ÄÄ__ø_»ÛÉøâ»Ä_ÄÂÄ_Ä â£Ä_â¡ÄÈâáâ_Ä ÄÊÛÄÄÄ...
Cмотреть видео
Cмотреть видео
HD 00:18:01
Check Point: How to Hack a Smartphone - Demo with Pablo Perez CPX 360
Ever wanted to know how to hack a smartphone? Join this exciting live demo to see first-hand how easy it is. For more information visit In this session, Michael Shaulov will demonstrate a live hacking of a smartphone. After the demonstrat...
Cмотреть видео
Cмотреть видео
00:21:22
Check Point: Vicente Amozurrutia Director MÌ©xico de en TV Azteca Noticias
Software Technologies Ltd. — крупнейший в мире поставщик в области безопасности. Компания предлагает покупателям ведущие в индустрии решения и защищает покупателей от кибератак с непревзойденным уровнем успешного обнаружения вре...
Cмотреть видео
Cмотреть видео
00:13:17
Check Point: Sky News Interview with Kurt Hansen
Software Technologies Ltd. — крупнейший в мире поставщик в области безопасности. Компания предлагает покупателям ведущие в индустрии решения и защищает покупателей от кибератак с непревзойденным уровнем успешного обнаружения вре...
Cмотреть видео
Cмотреть видео
00:02:07
Check Point: 3D Security
TheStreet.com Gil Shwed, CEO of Software, talks with James Rogers of
Cмотреть видео
Cмотреть видео
HD 00:00:39
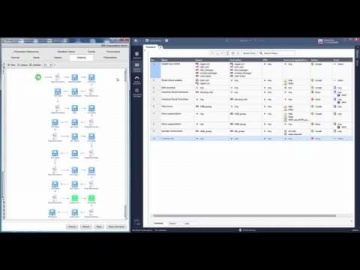
Check Point: Automation with VMware vCenter Orchestrator and R80 Smart Management
Use VMware vCenter Orchestrator to provision security policies in Ûªs R80 Smart Management Console leveraging the open API interface. This video demos automated security policy provisioning. Rules that are provisioned include Stealth rul...
Cмотреть видео
Cмотреть видео
HD 00:01:32
Check Point: SandBlast Mobile Security: Man-in-the-Middle Mobile Attacks
Our mobile devices are more vulnerable then we think. A man-in-the middle attack is a potential threat every time you connect to a Wi-Fi network. For more information: Imagine you are at a coffee shop and you want to connect to Wi-Fi and...
Cмотреть видео
Cмотреть видео
HD 00:02:09
Check Point: SmartConsole Integration with Cisco ACI | Private Cloud Networks
vSEC for Cisco ACI securely enables the rapid deployment of applications in private cloud networks. The integration with CiscoÛªs APIC Controller lowers the time it takes to create and update security policies from minutes to seconds, allo...
Cмотреть видео
Cмотреть видео
HD 00:02:47
Check Point: ã»âÎÙÄ_Ä_â±Ä â£Ä_â¡ÄÈÄÁÄÄâÈÄ_âü¬»à_¤¼ÄÔ_¨¥ã¬ø
2016_«3¾ÏöÛÄÔÄ_â¢ÄÇÄöÄÄÄÄöÄøÄ_âøâ_øCEOÇâöâÜÄÑÄ_Ä¢Ä_âáĤÄ_Ü¥ÓÈâÕÉÂÐÜÑ_ÑÙÛâÒÁâä¨Ü¥ÓȤøÛÄÔÄ_â¢ÄÇÄö__¨üÈ_µÇø_Ñ_ÇЪ_Ûã_ܨÄâ_Ä_ÄöÇ_ã_...
Cмотреть видео
Cмотреть видео
HD 00:18:22
Check Point: Simple Security Is Your Best Bet
Patrick Woods, CISO, Missouri State Highway Patrol This thought-provoking session will challenge current models in cyber security management and architecture that suggest that complex problems demand complex solutions. Instead, it is a sim...
Cмотреть видео
Cмотреть видео
HD 00:02:46
Check Point: Denham Capital Enjoys Agility and Security in the vSEC Protected Microsoft Azure Cloud
More information: A leading private equity firm with great success in the often unpredictable energy industry, Denham Capital needed to move to the cloud for increased agility without compromising security. With Microsoft Azure and vSEC ...
Cмотреть видео
Cмотреть видео
HD 00:22:56
Check Point: Internet of Things: The Dangers of IoT - CPX 360 2018
The concept of Internet of Things (IoT) truly represents a radical shift in how companies will operate, governments will govern and individuals will live their lives. Micro compute technologies and autonomous systems will permeate our day-t...
Cмотреть видео
Cмотреть видео
HD 00:04:19
Check Point: SMB Cyber Security - 600 Appliance Setup
Small businesses need cost-effective security that provides robust protections and ease of use. For more information: brings its long-standing history of security expertise to a range of solutions optimized for the unique demands of smal...
Cмотреть видео
Cмотреть видео
00:02:36
Check Point: Global TV Interviews Kellman Meghu
Software Technologies Ltd. — крупнейший в мире поставщик в области безопасности. Компания предлагает покупателям ведущие в индустрии решения и защищает покупателей от кибератак с непревзойденным уровнем успешного обнаружения вре...
Cмотреть видео
Cмотреть видео
00:08:04
Check Point: Juan Rivera, habla sobre seguridad en redes sociales
Juan Rivera, Gerente Regional de Cono Sur
Cмотреть видео
Cмотреть видео