Check Point: Malware Threat Prevention | Zero-Day, Zero-Second. → Похожие видео ролики , Страница 10
What can malware do in 60 seconds? One minute can change everything for a business. So what happens when the speed of business is overtaken by the speed of malware? The team devised a test to quantify that exact question. Learn More: As part of the SandBlast Zero-Day Protection solution, Threat Emulation prevents infections from new malware and targeted attacks. This innovative zero-day threat sandboxing capability within the SandBlast solution delivers the best possible catch rate for threats, and is virtually immune to attackers’ evasion techniques.
Подробнее в видео...
Подробнее в видео...
HD 00:15:01
Check Point: Do You Know What's Hiding On Your Network?
This video summarizes the analysis and findings in the 2013 Security Report. For more information: provides organizations of all sizes with the latest data and network security protection in an integrated next generation firewall platfo...
Cмотреть видео
Cмотреть видео
HD 00:02:08
Check Point: Capsule Docs – Keep Your Business Documents Protected | Enterprise | Network Security
Capsule Docs protects your sensitive business documents to ensure they don’t get unintentionally exposed. See how Capsule Docs works to provide document security.
Cмотреть видео
Cмотреть видео
HD 00:03:11
Check Point: Choose the Right Next Generation Firewall - Multi-Layer Security
Why Multi-Layer Security and how 's Software Blade Architecture is the most secure and scalable solution in this market. For more information: provides organizations of all sizes with the latest data and network security protection in a...
Cмотреть видео
Cмотреть видео
HD 00:00:37
Check Point: 03 Adding the vCenter IP Address to the Runtime Settings
VMware requires you to add the vCenter IP address to the Runtime Settings tab on the vCenter Server Setting page
Cмотреть видео
Cмотреть видео
HD 00:01:17
Check Point: RSA Conference 2014 - Customer Insights - Leidos
Find out more: speaks with customers and partners at RSA Conference 2014 in San Francisco. Watch as Joseph Royal of Leidos shares what makes him a fan.
Cмотреть видео
Cмотреть видео
HD 00:02:44
Check Point: Protected 24x7 With | Cyber Security
For more information visit:
Cмотреть видео
Cмотреть видео
HD 00:03:11
Check Point: Choose the Right Next Generation Firewall - Multi-Layer Security
Why Multi-Layer Security and how 's Software Blade Architecture is the most secure and scalable solution in this market. For more information: provides organizations of all sizes with the latest data and network security protection in a...
Cмотреть видео
Cмотреть видео
HD 00:01:24
Check Point: Capsule Docs - Secure Business Documents Everywhere | Network Security
Capsule Docs ensures that only authorized individuals can access your business documents. Confidently share documents with coworkers, business partners, clients, and vendors, because you are in control of their access and sharing rights.
Cмотреть видео
Cмотреть видео
HD 00:02:44
Check Point: CloudGuard SaaS Demo Series: Protecting Sensitive Data
For more information: Watch this short demonstration video to learn how CloudGuard SaaS, an industry-first software-as-a-service (SaaS) security solution, provides advanced security and sensitive data protection for SaaS applications such ...
Cмотреть видео
Cмотреть видео
HD 00:01:41
Check Point: 04 Installing the OVF Package and Configuring Global Parameters
Software Technologies Ltd. — крупнейший в мире поставщик в области безопасности. Компания предлагает покупателям ведущие в индустрии решения и защищает покупателей от кибератак с непревзойденным уровнем успешного обнаружения вре...
Cмотреть видео
Cмотреть видео
HD 00:01:27
Check Point: RSA Conference 2014 - Partner Insights - Dataway
Find out more: speaks with customers and partners at RSA Conference 2014 in San Francisco. Watch as Heather Zalatimo from partner Dataway shares thoughts about 's superior management capabilities and what makes her a fan.
Cмотреть видео
Cмотреть видео
HD 00:07:01
Check Point: Overview of the 61000 Appliance | Data Center Security Systems
For more information:
Cмотреть видео
Cмотреть видео
HD 01:04:31
Check Point: Webinar replay – Auto-scale advanced security for Microsoft Azure
For more information visit: Webinar replay - hear from customer George Dialectakis, IT Consultant at Eversource Energy, on how they leverage CloudGuard IaaS advanced threat prevention security for their Microsoft Azure cloud environme...
Cмотреть видео
Cмотреть видео
HD 00:01:48
Check Point: Mobile Security: Capsule
Introducing Capsule – Your Complete Secure Mobility Solution. Learn More: Only provides ONE solution that addresses ALL your mobile security needs: Protect devices (smartphones, tablets, and laptops) from threats everywhere, establish a...
Cмотреть видео
Cмотреть видео
HD 00:01:38
Check Point: CloudGuard SaaS Demo Series: Identity Protection for Office 365
Watch this short demonstration video to learn how CloudGuard SaaS, an industry-first software-as-a-service (SaaS) security solution, provides advanced security and identity protection including account takeover protection for SaaS applicat...
Cмотреть видео
Cмотреть видео
HD 00:02:18
Check Point: RSA Conference 2014 - Partner Insights - Soluciones Seguras
Find out more: speaks with customers and partners at RSA Conference 2014 in San Francisco. Watch as Eli Fashka of Soluciones Seguras shares how they are using solutions with their customers. He also speaks to 's management and consol...
Cмотреть видео
Cмотреть видео
HD 00:02:15
Check Point: 05 Registering a vSEC Gateway Service and Host Preparation
Software Technologies Ltd. — крупнейший в мире поставщик в области безопасности. Компания предлагает покупателям ведущие в индустрии решения и защищает покупателей от кибератак с непревзойденным уровнем успешного обнаружения вре...
Cмотреть видео
Cмотреть видео
HD 01:01:35
Check Point: EU GDPR Webinar Replay
The European Union’s General Data Protection Regulation (‘GDPR’) poses the biggest change to the regulatory landscape of data privacy. To learn more visit: GDPR places significant policy and technical responsibilities on ANY organization ...
Cмотреть видео
Cмотреть видео
HD 00:04:23
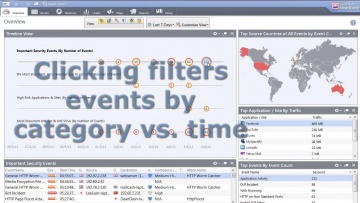
Check Point: SmartEvent | Security Management Walk-Through
Are you tired of managing security by manually searching through millions of logs to find the information you need? There is a better way! Watch this SmartEvent Video to learn how to manage your security more efficiently. For more informa...
Cмотреть видео
Cмотреть видео
HD 00:04:05
Check Point: Denial of Service Attacks & How to Protect Against Them
DDoS Protector™Appliances block Denial of Service attacks within seconds with multi-layered protection and up to 40 Gbps of performance. For more information: Alon Kantor, Corporate Development Architect at talks about the threat of dist...
Cмотреть видео
Cмотреть видео
00:05:37
Check Point: Why Trust Matters for Security
Following a press round table event held in London in December 2012, panelists looked at why trust is fundamental to security, and how organizations can prove that they and their employees can be trusted. The spokespeople are: - Kevin B...
Cмотреть видео
Cмотреть видео
HD 00:00:47
Check Point: 06 Creating a vSEC Gateway IP Address Pool
We recommend that you create pool for automatic assignment of management interface IP addresses.
Cмотреть видео
Cмотреть видео
HD 00:01:15
Check Point: Advanced Cyber Attack Business Protection
SandBlast mobile offers the best advanced cyber attack protection for your business. More information: Cybercriminals are better than ever at stealing sensitive information from your smartphone or tablet. Whether it's personal information...
Cмотреть видео
Cмотреть видео
HD 00:03:04
Check Point: Choosing the Right Next Generation Firewall | NGFW Explained
For more information: What is a Next Generation Firewall, where did the term come from and why is leading this market.
Cмотреть видео
Cмотреть видео
HD 00:01:32
Check Point: 07 Deploying the Service
This procedure uses an Agent VM, for an environment with a local Datastore. If you will use an external Datastore, have its details ready before you begin.
Cмотреть видео
Cмотреть видео
HD 00:02:05
Check Point: Secure your Mobile Phone Now | Introducing SandBlast Mobile
Protecting your enterprise from mobile threats and cyber attacks. More information: Worried about your Mobile Privacy? Secure your mobile phone now against mobile threats. Keeping your business safe from cyberattacks is no easy task, and...
Cмотреть видео
Cмотреть видео
HD 00:03:49
Check Point: A Day in the Life of Mike, a Next Generation Firewall Administrator
For more information: See how security admins can easily create granular policies—based on users or groups—to identify, block or limit usage of over Web 2.0 applications and educate users on safe Internet use with our Next Generation Fire...
Cмотреть видео
Cмотреть видео
HD 00:01:51
Check Point: 08 Creating Security Group and IP Sets
Software Technologies Ltd. — крупнейший в мире поставщик в области безопасности. Компания предлагает покупателям ведущие в индустрии решения и защищает покупателей от кибератак с непревзойденным уровнем успешного обнаружения вре...
Cмотреть видео
Cмотреть видео
HD 00:04:43
Check Point: Next-Generation Secure Web Gateway | Network Security
Learn More: Are you trying to secure Web 2.0 with 1.0 tools? The Web has evolved, threats have evolved, so should your Web Security! In this video, learn how to best protect against today's web-borne malware and help businesses to get th...
Cмотреть видео
Cмотреть видео
HD 00:02:10
Check Point: SandBlast Mobile: Protecting Against Malicious Apps
Our mobile devices are used for both personal and business purposes. Installing new apps may compromise both your private and corporate data. Every year, malicious apps downloaded from official app stores infect millions of mobile devices....
Cмотреть видео
Cмотреть видео