Check Point: Malware Threat Prevention | Zero-Day, Zero-Second. → Похожие видео ролики , Страница 4
What can malware do in 60 seconds? One minute can change everything for a business. So what happens when the speed of business is overtaken by the speed of malware? The team devised a test to quantify that exact question. Learn More: As part of the SandBlast Zero-Day Protection solution, Threat Emulation prevents infections from new malware and targeted attacks. This innovative zero-day threat sandboxing capability within the SandBlast solution delivers the best possible catch rate for threats, and is virtually immune to attackers’ evasion techniques.
Подробнее в видео...
Подробнее в видео...
HD 00:06:37
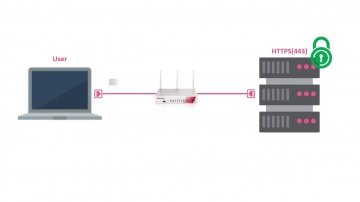
Check Point: HTTPS Inspection on Small Business Appliances
Watch our tutorial on how to enable HTTPS inspection on our 700 Appliance to improve your small business security. More information:
Cмотреть видео
Cмотреть видео
HD 00:08:24
Check Point: Lightboard Series: Dynamic Revisions
This video elaborates on the logic behind the R80.10 Security Management architecture focusing on the dynamic revisions feature. This feature automatically stores the full history of database changes, with very little footprint, consuming ...
Cмотреть видео
Cмотреть видео
HD 00:26:30
Check Point: Infinity | The Cyber Security Architecture of the Future
Gabi Reish - VP, Product Management and Product Marketing, Software For more information on the Cyber Security Architecture of the Future, please go to:
Cмотреть видео
Cмотреть видео
HD 00:01:54
Check Point: Advanced Cyber Security for 2018 | Prevent 5th Generation Cyber Attacks with Infinity
More information: Infinity is the first consolidated security across networks, cloud and mobile, providing the highest level of threat prevention against both known and unknown targeted attacks to keep you protected now and in the future...
Cмотреть видео
Cмотреть видео
HD 00:01:57
Check Point: Anti-Ransomware vs WannaCry | Ransomware Protection Demonstration
WannaCry ransomware hits more than 75,000 organizations in over 99 countries and is quickly spreading. Here's how you can prevent ransomware attacks against your organization with SandBlast Agent, Anti-Ransomware. For more information on h...
Cмотреть видео
Cмотреть видео
HD 00:01:10
Check Point: RSA 2016: Prevent Cyberattacks from Entering the Endpoint with SandBlast Agent
More information:
Cмотреть видео
Cмотреть видео
00:02:53
Check Point: opens NASDAQ
Gil Shwed, CEO of Software Technologies, Ltd., opens NASDAQ on 12 August 2009.
Cмотреть видео
Cмотреть видео
HD 00:02:14
Check Point: 1200R: Ruggedized Security for Industrial Control Systems | SCADA | ICS Security
Overview of ICS and 1200R appliance:
Cмотреть видео
Cмотреть видео
HD 00:03:55
Check Point: Deploy Small Business Appliances with the Zero Touch Cloud Service
Watch our overview of the Zero Touch Cloud Service to see how you can save valuable time in the initial deployment of our small business security appliances. For more information:
Cмотреть видео
Cмотреть видео
HD 00:02:43
Check Point: and Savvius Partnership
and Savvius’ joint solution captures mission-critical security alerts and investigates any abnormalities in your network. For more information:
Cмотреть видео
Cмотреть видео
HD 00:23:38
Check Point: Adaptive Security Framework for Internet of Drones
Internet of Drones is an architecture designed for providing coordinated access to controlled airspace for Unmanned aerial vehicles (UAVs).
Cмотреть видео
Cмотреть видео
HD 00:17:15
Check Point: Infinity - A Day in the Life of a Security Administrator
Having worked with access control as a basic security level for over 20 years, the speakers reminisce about how much better it was in the past.
Cмотреть видео
Cмотреть видео
HD 00:14:41
Check Point: CheckMates TechTalk: Remote Code Execution Vulnerability on LG Smartphones
Neatsun Ziv and Jonathan Shimonovich discuss our recent publication of vulnerabilities that reside in the default keyboard of all mainstream LG smartphone models. More details:
Cмотреть видео
Cмотреть видео
HD 00:22:11
Check Point: WannaCry 3.0, próximamente en sus pantallas… del móvil | CyberDay Spain 2017
Ran Schwartz, Product Manager para Mobile Security Products
Cмотреть видео
Cмотреть видео
HD 00:06:00
Check Point: [Part 4] Protecting Your Mobile Workforce with SandBlast Mobile & Microsoft Intune
Videos in this Series: Part 1 - Preparing Microsoft Intune for Integration with SandBlast Mobile Part 2 - Configuring Integration between SandBlast Mobile and Microsoft Intune Part 3 - Testing Integration Part 4 - Solution Overview and Star...
Cмотреть видео
Cмотреть видео
HD 00:00:38
Check Point: vSEC for your AWS Workloads
Utilizing the same security management tool across your hybrid cloud architecture can help your organization be more secure and agile. Maximize the strength of your security posture and capacity for innovation in cloud environments with vSE...
Cмотреть видео
Cмотреть видео
HD 00:00:49
Check Point: RSA 2016: Receives "Recommended" Rating in NSS Next Generation Firewall Test
More Information: NSS Labs, Inc. released their results for the 2016 Generation Firewall Test. In their independent assessment of the security effectiveness and value, NSS once again recognized with the "Recommended" rating. This marks t...
Cмотреть видео
Cмотреть видео
HD 00:02:49
Check Point: Advanced Cyber Security for 2018 | Prevent Gen V Cyber Attacks with Infinity
More information: ... Infinity is the first consolidated security across networks, cloud and mobile, providing the highest level of threat prevention against both known and unknown targeted attacks to keep you protected now and in the fut...
Cмотреть видео
Cмотреть видео
HD 00:27:09
Check Point: Shedding Light on the Dark Web
Avi Rembaum + Neatsun Ziv The dark web is quickly evolving into a marketplace of information and tools that the hackers and adversaries use to breach company networks. The question we face as an industry is how to leverage an awareness of ...
Cмотреть видео
Cмотреть видео
HD 00:02:38
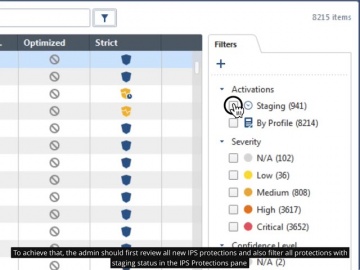
Check Point: R80.10 Policy Management – IPS Protections in Detect (Staging) State
This video elaborates on the logic behind new IPS protections status after IPS update operation and introduces best practice on changing the status of detect-staging on prevent when enough information was gathered regarding the new IPS prot...
Cмотреть видео
Cмотреть видео
HD 00:21:03
Check Point: Cyber Security Trends, Jeff Schwartz - CPX 360 2018, Why Our Security Problems are Gett
Security spending is up 8% year over year, yet security incidents are up ~40%. Why does the security "ball of yarn" continue to unravel as we pull the string. In this session, you will learn why our security problems continue to get worse ...
Cмотреть видео
Cмотреть видео
HD 00:03:20
Check Point: 2017 Mobile Security Media Tour
Our Michael Shaulov, Head of Product, Mobile Security discusses the importance of mobile security and common vulnerabilities and threats mobile data of individuals and the enterprise. For more information:
Cмотреть видео
Cмотреть видео
HD 00:11:59
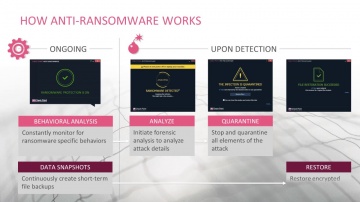
Check Point: Introducing Anti-Ransomware: Defeat Cyber Extortion
Did you know ransomware hit 1 in 3 businesses during 2016? Today more than ever you need a new way to effectively prevent ransomware from impacting your organization. Watch our webinar replay to learn how you can automatically detect, block...
Cмотреть видео
Cмотреть видео
00:03:38
Check Point: ZoneAlarm vs. Windows 7
Microsoft has made a much anticipated new operating system. However, the hackers will continue to find ways to bypass whatever security measures the operating system puts in place. Due to the fact consumers should use an advanced security s...
Cмотреть видео
Cмотреть видео
HD 00:02:44
Check Point: You Asked, CEO Gil Shwed Answers!
Is Gil Shwed a morning person or a night owl? CEO Gil Shwed talks about his favorite apps, drones, future roadmap, and recognizes the winners in our CheckMates Birthday Awards!
Cмотреть видео
Cмотреть видео
HD 00:06:03
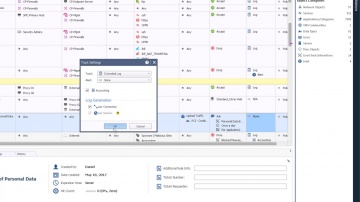
Check Point: Compliance Software Blade - Regulatory Compliance
For more information: This is the third video in the Compliance Software Blade Demonstration Series. See how the Compliance Software Blade can help you easily review your regulatory compliance status, and quickly prepare detailed reports ...
Cмотреть видео
Cмотреть видео
HD 00:01:46
Check Point: RSA 2016: Day 1 - Software
For more information visit: An overview of RSA 2016, Day 1 with Software.
Cмотреть видео
Cмотреть видео
HD 00:05:27
Check Point: Start Building Your Unified Policy with R80.10 | Security Management | Tech Bytes
R80.10 policy management is unified so you can create and monitor these policies harmoniously. One single policy manages your users, devices, applications, data and networks. With this unified policy, you also get unparalleled granular cont...
Cмотреть видео
Cмотреть видео
HD 00:38:26
Check Point: Estado de la Ciberseguridad en Operadores de ICS Españolas | CyberDay Spain 2017
Miguel García, VP Centro de Ciberseguridad Industrial Cofundador y Presidente, iTTi, The [Digital] Accountability Think Tank.
Cмотреть видео
Cмотреть видео
HD 00:01:54
Check Point: SMB 700 Appliance - チェック・ポイントのSMB向け700アプライアンス・シリーズ
オールインワンのUTMで中小規模環境にエンタープライズ・レベルのセキュリティを提供するチェック・ポイントの700アプライアンス・シリーズをご紹介します。
Cмотреть видео
Cмотреть видео













![Check Point: [Part 4] Protecting Your Mobile Workforce with SandBlast Mobile & Microsoft Intune](https://12n.ru/upload/video/images/small/08/9e/089e1d1073d9c60b3f3c157ce45a81cb.jpg)