itbion.ru / Видео / По рейтингу
Check Point: Architecting Consolidated Security with Infinity
Presenting The Good, The Bad and The Ugly. Where does your company’s architecture fit? Learn how to build the best Infinity architecture and chime into a live interview listening to those who have transformed Ugly into Good.
Cмотреть видео
Cмотреть видео
Check Point: Ask Us Anything: Dr. Dorit Dor and Team
Dr. Dorit Dor, Vice President of Products at , leads the company’s product management, business development, research and development (R&D) and quality assurance (QA). Together with the amazing product team at , they lead the initiatives fr...
Cмотреть видео
Cмотреть видео
Check Point: Protecting Your Mobile Workforce with SandBlast Mobile & Microsoft Intune Pt.1
Videos in this Series: Part 1 - Preparing Microsoft Intune for Integration with SandBlast Mobile Part 2 - Configuring Integration between SandBlast Mobile and Microsoft Intune Part 3 - Testing Integration Part 4 - Solution Overview and Star...
Cмотреть видео
Cмотреть видео
Check Point: Advanced Cyber Security for 2018 | Infinity
Learn more at Introducing Infinity, the world’s most advanced cyber security and management architecture. Infinity consolidates security across network, cloud and mobile, keeping you secured from known and unknown threats, today and in ...
Cмотреть видео
Cмотреть видео
Check Point: 700 Series Appliances for Small Business - Product Video | SMB Cyber Security
As a small business, your focus is on building unique products, driving sales, and providing excellent service to your customers. Security is important but it seems like every week there is some new piece of software or equipment to prote...
Cмотреть видео
Cмотреть видео
Check Point: What is CheckMates?
For more information: A brief introductory video about 's official user community: CheckMates!
Cмотреть видео
Cмотреть видео
Check Point: GDPR Recommendations for Data Privacy
Coming into effect in May 2018, the European Union’s General Data Protection Regulation (‘GDPR’) poses the biggest change to the regulatory landscape of data protection and privacy.
Cмотреть видео
Cмотреть видео
Check Point: Centralized Security Management Across the Enterprise
Managing security means having to deal with multiple point solutions. This is not only a challenge from an operations/TCO perspective, but also from a security standpoint (point solutions versus a consolidated approach will create security...
Cмотреть видео
Cмотреть видео
Check Point: Gil Shwed Keynote: Stepping Up to Gen V of Cyber Security
Gil Shwed's keynote from CPX 2018 on the future of Cyber Security. Find out what Gen V Cyber Attacks are and how you can prevent the next Cyber Attack. For more information visit -
Cмотреть видео
Cмотреть видео
Check Point: The Mobile Threat Landscape
From Judy to Blueborne, the proliferation of mobile threats has grown rapidly in the past year. In this session, we review the various types of mobile threats, how they spread and the damage they cause. We will also be providing practical ...
Cмотреть видео
Cмотреть видео
Check Point: Petya Malware Blocked by Anti-Ransomware | Ransomware Cyberattack | Tech Bytes
A massive ransomware attack erupted on June 27 worldwide by a variant of Petya, a form of ransomware that encrypts the entire hard-drive rather than each file individually. This attack by Petya crippled many large banks, government offices ...
Cмотреть видео
Cмотреть видео
Check Point: Anti-Ransomware: Solution Brief & Demo | Tech Bytes
Anti-Ransomware protects against sophisticated zero-day ransomware. It is included in SandBlast Agent. More information: Protect endpoints from sophisticated attacks and zero-day threats, enabling a deep understanding of security events f...
Cмотреть видео
Cмотреть видео
Check Point: Best of CheckMates: My Top CLI Commands
This presentation will highlight the most useful CLI commands submitted via CheckMates by real users just like you!+ For more information: Use cases, examples and case studies will be presented for the top CLI commands from the CheckMate...
Cмотреть видео
Cмотреть видео
Check Point: CheckMates First Birthday Award Winners
CheckMates, the user community for customers and partners, is celebrating it's first birthday by recognizing excellent contributors and content!
Cмотреть видео
Cмотреть видео
Check Point: Protect Your Mobile Workforce with SandBlast Mobile & Microsoft Intune
Videos in this Series: Part 1 - Preparing Microsoft Intune for Integration with SandBlast Mobile Part 2 - Configuring Integration between SandBlast Mobile and Microsoft Intune Part 3 - Testing Integration Part 4 - Solution Overview and Star...
Cмотреть видео
Cмотреть видео
Check Point: Optimizes Security with Gigamon’s Full Network Visibility
and Gigamon’s joint solution provides comprehensive network visibility, optimal performance and advanced threat prevention capabilities. For more information:
Cмотреть видео
Cмотреть видео
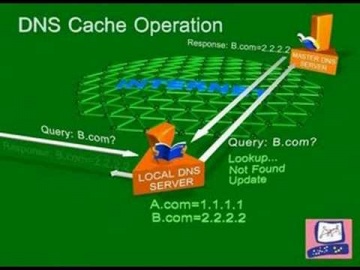
Check Point: DNS Cache Poisoning Attack | Internet Security
Software explains common DNS attacks. Learn More: DNS is the glue that holds the Internet, including web and e-mail together. A successful attack may severely impact the availability of an organization’s public facing web sites and e-mail...
Cмотреть видео
Cмотреть видео
Check Point: SMB Security Unique Challenges
The Small and Medium Business market has the same security challenges as larger enterprises. What they don't have a lot of is time or money.
Cмотреть видео
Cмотреть видео
Check Point: Trial Threat Emulation on Small Business Appliances
Watch our tutorial on how to trial Threat Emulation (sandboxing) on our 700 Appliance URL for more information:
Cмотреть видео
Cмотреть видео
Check Point: Learn from the Masters: Maximize the value of your Threat Prevention
Would you like to use SandBlast like a Cyber Jedi? Find out how to achieve the best possible prevention and visibility utilizing the full power of SandBlast’s cutting-edge cyber technologies. Learn from our top experts' cool tricks and be...
Cмотреть видео
Cмотреть видео
Check Point: Advanced Cyber Security for 2018 | Infinity | Technical Deep Dive with Jeff Schwartz
Infinity is the first consolidated security across networks, cloud, and mobile, providing the highest level of threat prevention against both known and unknown targeted attacks to keep you protected now and in the future. Jeff Schwartz, our...
Cмотреть видео
Cмотреть видео
Check Point: SandBlast Mobile: Quick Start Guide | Tech Bytes
This video is meant to show how easily you can get started protecting your Enterprise's Android and iOS Devices with SandBlast Mobile. More information: Topics covered: Ch1 - Activating Your Admin Account Ch2 - Logging into Your SandBlast...
Cмотреть видео
Cмотреть видео
Check Point: Ä¢Äâ_ÄÇãɬø__Ð
More information: Report: IDC Technology Spotlight: Why Comprehensive Security Requires Mobile Threat Prevention: Protecting Your Enterprise From Mobile Threats (Japanese Subtitles) Keeping your business safe from cyberattacks is no ea...
Cмотреть видео
Cмотреть видео
Check Point: Cyber Threat Incident Response War Stories
The Cloud is an amazing game changer. It provides the ability to revolutionize IR. But it can also have a much darker side. Join the head of the Cyber Threat Incident Response Team as we explore the darker side of the Cloud and provide...
Cмотреть видео
Cмотреть видео
Check Point: Who's Responsible for your Cloud Security?
A full breakdown of what is shared responsibility and the layers of security needed to protect you from security breaches in the cloud. For more information:
Cмотреть видео
Cмотреть видео
Check Point: Artificial Intelligence in Managed Incident Response
The presentation is focused on the Managed Incident Response 5.(MIR) and it will be based on the case studies of our two award-winning** customer projects, ITC and GSTN. We have successfully executed & extended the Sandblast Solution to ...
Cмотреть видео
Cмотреть видео
Check Point: Bienvenida e Introduccion a Infinity | CyberDay Spain 2017
Mario García, Director General España y Portugal Infinity, la arquitectura de ciberseguridad del futuro. Gabi Reish , VP Worldwide Product Management
Cмотреть видео
Cмотреть видео
Check Point: Welcome to the Future of Cyber Security | Infinity
The future of cyber security is here. Learn and stay protected against today's cyber threat landscape. For more information: We are all living in a connected world which is affecting every aspect of our lives. In the past couple of ye...
Cмотреть видео
Cмотреть видео
Check Point: You Asked, VP of Products Dorit Dor Answers!
Is Dr. Dorit Dor a morning person or a night owl? Our VP of Products talks about her favorite apps, drones, future roadmap, and recognizes the winners in our CheckMates Birthday Awards!
Cмотреть видео
Cмотреть видео
Check Point: Preventing the Ransomware Plague | Ransomware Protection
Ransomware reached epidemic proportions in 2016. Organizations of all sizes and sectors fell victim to malware that locked down, encrypted – and in some cases threatened to destroy – critical systems and data. How would you avoid becoming t...
Cмотреть видео
Cмотреть видео