itbion.ru / Видео / По рейтингу
Check Point: The Mississippi Secretary of State & CTO Prevents Ransomware
For more information visit Seeking to modernize its security infrastructure, the Mississippi Secretary of State upgraded to SandBlast and now prevents ransomware attacks and enjoys a peace of mind.
Cмотреть видео
Cмотреть видео
Check Point: Un Viaje Seguro a la Nube | CyberDay Spain 2017
Javier Hijas, Cloud Security Team Leader Europe
Cмотреть видео
Cмотреть видео
Check Point: R80.10 Security Management | Tech Bytes: Gateways, Logs, and Manage & Settings
This video is an overview that describes important features and functionality of the R80.10 SmartConsole. More information: To learn more about R80.10 Security Management: Infinity is the only fully consolidated cyber security architec...
Cмотреть видео
Cмотреть видео
Check Point: Orchestrating Gateway Operations
In this session, we will take you through some of the operations that are performed on gateways that are not the typical rule base changes.
Cмотреть видео
Cмотреть видео
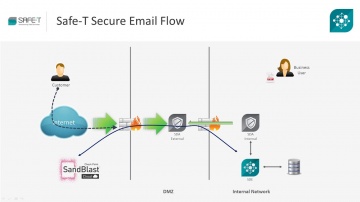
Check Point: Securing Data Exchange with SandBlast and Safe-T HDS
Organizations today face host of challenges in securing high risk data. SandBlast is most advanced protection against zero-day malware threats, while Safe-T HDS secures all data exchange scenarios including human data exchange such as secu...
Cмотреть видео
Cмотреть видео
Check Point: L’Oréal vSEC Case Study
As one of the world’s leading beauty brands, the L'Oréal group has spent the last century in the pursuit of perfection.
Cмотреть видео
Cмотреть видео
Check Point: R80.10 Best Practices – Migrating from R77.30
Get the insights from Professional Services on how to migrate from R77.30 to R80.10.
Cмотреть видео
Cмотреть видео
Check Point: Top 5 Cloud Security Tips (How to Protect Your Data in the Cloud)
The era of cloud is upon us; firms of all sizes and in all walks of life are looking to leverage the agility and elasticity of cloud. But cloud carries a totally new and unique set of security challenges. In this informative and entertainin...
Cмотреть видео
Cмотреть видео
Check Point: Upgrading from R77.3O to R80.10 Via CPUSE
This video demonstrates in-place upgrade of a real customer database from R77.30 to R80.10 via CPUSE interface in the Web UI.
Cмотреть видео
Cмотреть видео
Check Point: Compliance Software Blade | Network Security Best Practices
For more information: This is the second video in the Compliance Software Blade Demonstration Series. This video provides insight into aligning both security and compliance to security best practices.
Cмотреть видео
Cмотреть видео
Check Point: Moving to the Public Cloud, Securely - FireChat with AWS & Azure
More than 70% of the organizations are committed to a cloud strategy in 2017. Businesses are moving their applications to the Cloud to gain more agility and efficencies. At the same time, Cloud security remains their top concern. Customers...
Cмотреть видео
Cмотреть видео
Check Point: The Security Zone Ep. 2: Forget Zero Day, Hello Zero Second
Delayed response is no longer enough to protect your business from the speed of malware. We need a ZERO SECOND response. A recent benchmark test assessed how fast Threat Emulation and other competitive products stop malware from entering a...
Cмотреть видео
Cмотреть видео
Check Point: Advanced Endpoint Protection & Forensics | Advanced Threat Prevention
Continuously preventing even the most sophisticated cyber attacks and responding quickly to limit damages on endpoint devices is essential to all businesses today. More information: The SandBlast Agent extends Ûªs industry-leading zero-...
Cмотреть видео
Cмотреть видео
Check Point: Happy International Women's Day 2018
The women of share the best advice they ever received in recognition of International Women's Day 2018. Learn more about at
Cмотреть видео
Cмотреть видео
Check Point: IPS Software Blade
SSL Certificates attacks can compromise even the most secure sites. Learn how s IPS solutions protect against this specific kind of threats.
Cмотреть видео
Cмотреть видео
Check Point: CISO viewpoint on modern IT: Britney Hommertzheim, Director, Information Security, AMC
In this session, Britney Hommertzheim, Director, Information Security. AMC Theatres. will share his vision on modern IT, among others the importance of compliance and security and how they are very different. Additionally, he will review ...
Cмотреть видео
Cмотреть видео
Check Point: vSEC, The Future of Cloud Security
In this video, you’ll hear from Donald Meyer, Head of Marketing, Data Center and Cloud, where he discusses issues surrounding Cloud security and how organizations can better protect themselves from vulnerabilities in the Cloud. For more in...
Cмотреть видео
Cмотреть видео
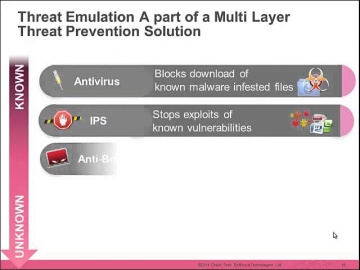
Check Point: The Security Zone Ep. 3: How to Choose Your Next Generation Threat Emulation Solution
Organizations are facing unprecedented growth in the number of security threats from malware. New attack types combine known and unknown threats to exploit vulnerabilities. Join us to learn how can protect against unknown malware.
Cмотреть видео
Cмотреть видео
Check Point: CAN News, Colin Pennan talks on 'Advanced Persistent Threats'
For More Information Visit: Advanced Persistent Threats are not your average cyber-threat . Learn what makes "Advanced Persistent Attacks" unique and the intricate planning goes into these targeted attacks. In this interview Colin P...
Cмотреть видео
Cмотреть видео
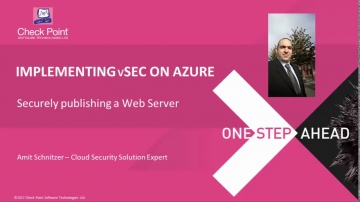
Check Point: Step-By-Step Guide for Securing a Web Server on Azure using CloudGuard IaaS (prev. vSE
Learn to create and deploy a web server on top of Azure public cloud and to securely publish it through a vSEC standalone server. More information:
Cмотреть видео
Cмотреть видео
Check Point: Security Blueprint for the Cloud Era
Discover the recommended blueprint for multi-cloud security. Take a deep dive on perimeter security, east-west security, connected clouds, auto-scale, and auto provisioning.
Cмотреть видео
Cмотреть видео
Check Point: Choosing The Right Security Architecture | Cyber Security | Network Security
Moti Sagey - Head of Strategic Marketing & Intelligence, Software When it comes to choosing the right security architecture & security vendor, what does it take to win your trust? In this session Moti Sagey will cover three key pillars th...
Cмотреть видео
Cмотреть видео
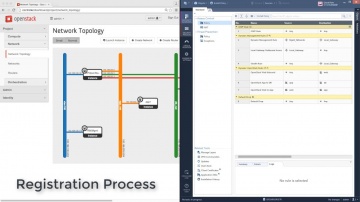
Check Point: Automating vSEC in OpenStack | Tech Bytes
Demo video showcasing automation and orchestration of vSEC Security Gateway in OpenStack (without narration). For more information:
Cмотреть видео
Cмотреть видео
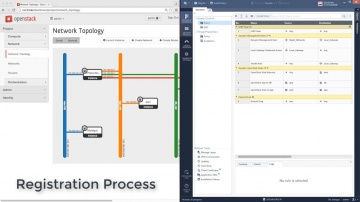
Check Point: Automating vSEC in OpenStack | Tech Bytes
Demo video showcasing automation and orchestration of vSEC Security Gateway in OpenStack (without narration). For more information:
Cмотреть видео
Cмотреть видео
Check Point: Sobrevivir a la plaga de ransomware | CyberDay Spain 2017
Eusebio Nieva, Director Técnico España y Portugal
Cмотреть видео
Cмотреть видео
Check Point: Cloud Security - VMware & CloudGuard - CPX 360 2018
Businesses that use the public cloud are vulnerable to cyber threats. Learn how to close the security gaps in the cloud. Public and hybrid cloud adoption is exploding among enterprises, but so are cloud hacks and breaches. Cloud asset...
Cмотреть видео
Cмотреть видео
Check Point: 時代はゼロデイからゼロセカンド(秒)へ – サンドボックス機能比較
時代はゼロデイからゼロセカンド(秒)へ。セキュリティの脅威への対応が1分遅れただけでも取り返しのつかないことになる今日、いかに早く脅威を阻止するかが重要です。
Cмотреть видео
Cмотреть видео
Check Point: Koch Media Crushes Advanced Attacks with SandBlast | Advanced Threat Prevention
Koch Media develops games globally, which is a process fraught with peril to the intellectual property in their games. Koch sought to replace Cisco and decided on SandBlast Zero DayProtection to crush advanced attacks. For more informat...
Cмотреть видео
Cмотреть видео
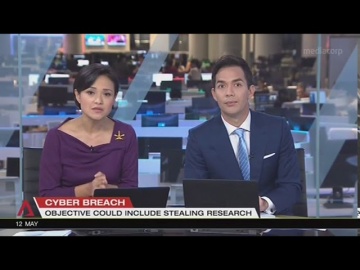
Check Point: Hamas’ Cyber Tactics Exposed - Attacking IDF Soldier’s Mobile Phones
The Israeli Defense Forde uncovered a Hamas network that reached out to IDF soldiers online, sometimes in romantic ways, and ask them to download applications that would infect them with Trojan horse viruses. The applications used by Hamas ...
Cмотреть видео
Cмотреть видео
Check Point: Makes DLP Work | Data Loss Prevention
's new DLP Software Blade combines innovative technology with a unique approach that blocks intentional and unintentional data breaches and educates employees in the process to help prevent future incidents. Watch this video to see how...
Cмотреть видео
Cмотреть видео