itbion.ru / Видео / По рейтингу
Check Point: SandBlast Zero-Day Protection | Advanced Threat Prevention
Hackers constantly modify their strategies and techniques to evade detection by traditional sandboxes to reach corporate resources. For more information visit: SandBlast Zero-Day Protection, with evasion-resistant malware detection, pro...
Cмотреть видео
Cмотреть видео
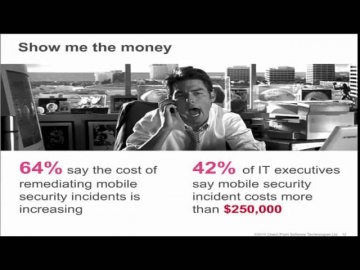
Check Point: The Security Zone Ep. 4: Bridge the Enterprise Mobile Security Gap
Mobile security continues to be a challenge for organizations providing business access on mobile platforms, whether it is on corporate owned or personal devices. While point products provide help with addressing some concerns, they do not ...
Cмотреть видео
Cмотреть видео
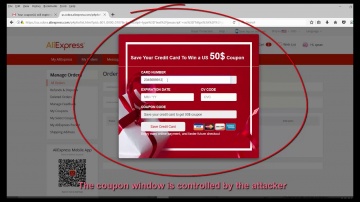
Check Point: Research Finds AliExpress Vulnerability: How It Works
To Read The Full Story Visit: Researchers at discovered that criminals have a new way to trick online shoppers via the massively popular AliExpress shopping portal using Java Script. After discovering the vulnerability, they immediate...
Cмотреть видео
Cмотреть видео
Check Point: CPU-level Sandboxing with SandBlast | Advanced Threat Prevention
s cutting-edge CPU-level inspection engine eliminates cyber threats at the point of pre-infection before cyber attack. VLearn more: This unrivaled exploit prevention technology provides a higher catch rate of threats and gives organizati...
Cмотреть видео
Cмотреть видео
Check Point: From HummingBad to Worse: Android Malware Campaign | SandBlast Mobile Security
For five months, mobile threat researchers had unprecedented access to the inner-workings of Yingmob, the Chinese cyber criminals behind HummingBad, a malware that establishes a persistent rootkit on Android devices, generates fraudulent a...
Cмотреть видео
Cмотреть видео
Check Point: Secure Your AWS Apps and Data | Cloud Security
vSEC delivers comprehensive threat prevention security with consolidated management and enforcement for AWS hybrid clouds. For more information:
Cмотреть видео
Cмотреть видео
Check Point: The Security Zone Ep. 5: Impact of Mobile Devices on Information Security
teamed up with Dimensional Analysis to survey over 700 IT and security professionals in 6 countries to learn the current attitudes and trends regarding the impact of mobile devices on information security.
Cмотреть видео
Cмотреть видео
Check Point: Guerra cibernÌ©tica, nuestro paÌ_s es vulnerable a ataques en la red
Juan Rivera, Gerente Regional de Cono Sur
Cмотреть видео
Cмотреть видео
Check Point: Tutorial: Configuring Application Control
How to use R80 SmartConsole to get started with the Application Control, URL Filtering Software Blades, and URL Filtering Settings with R80 Security Management. For more information: Infinity, the first consolidated security across net...
Cмотреть видео
Cмотреть видео
Check Point: 3D Security.mov
For more information visit: 3D Security vision redefines security as a 3-dimensional business process that combines policies, people and enforcement for stronger protection across all layers of security—including network, data and endpoi...
Cмотреть видео
Cмотреть видео
Check Point: What To Do When It Happens to You - Incident Response
Based on real world experiences of helping customers, this candid discussion will focus on ensuring that your organization is prepared when a breach occurs in your network. The discussion will provide real world examples of what works and w...
Cмотреть видео
Cмотреть видео
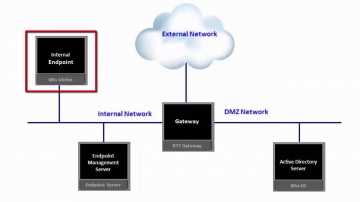
Check Point: Installing SandBlast Agent on the Enterprise Endpoint
This video provides an overview of recommended process for deployment of SandBlast Agent on the Enterprise Endpoints. SandBlast Agent defends endpoints with a complete set of real-time advanced endpoint protection technologies, including T...
Cмотреть видео
Cмотреть видео
Check Point: Cyber Security Trends: Thierry Karsenti - CPX 360 2018
Security spending is up 8% year over year, yet security incidents are up ~40%. Why does the security "ball of yarn" continue to unravel as we pull the string. In this session, you will learn why our security problems continue to get worse ...
Cмотреть видео
Cмотреть видео
Check Point: R80.10 Policy Revision
R80.10 Policy revision explained. Learn how to work with policy revision in R80.10. For more information: R80.10 features the most advanced threat prevention across networks and cloud, managed by a single security management console. Secu...
Cмотреть видео
Cмотреть видео
Check Point: SandBlast - ゼロデイ攻撃対策ソリューション
攻撃者は、検出をすり抜け企業の資産にアクセスする目的で、絶えず新たな戦略や手法を編み出しています。このような攻撃に対処するチェック・ポイントのゼロデイ攻撃対策ソリューションは、より深いレベルで検査を実施しマルウェアやゼロデイ攻撃からの保護を強化しながら、安全なコンテンツをユーザにすばやく確実に転送します。
Cмотреть видео
Cмотреть видео
Check Point: Malware Protection 2018 - Public Health Service Prevents, Not Just Detects, Advanced Th
For more information: Malware Protection in 2018 is about prevention not just detection. As a leading West Coast provider of emergency health services, this Public Health Service organization has over two million patients and runs over...
Cмотреть видео
Cмотреть видео
Check Point: Viking Horde: A New Type of Android Malware on Google Play | Mobile Security
Blog: More information: The research team uncovered a new Android malware campaign on Google Play it calls Viking Horde. Viking Horde conducts ad fraud, but can also be used for other attack purposes such as DDoS attacks, spam messages...
Cмотреть видео
Cмотреть видео
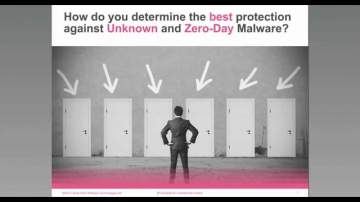
Check Point: Identifying The Best Sandboxing Solution Featuring Miercom | Advanced Threat Prevention
Learn More: Protecting against known, and new, advanced, unknown threats requires the most rapid and precise detection and protection technologies. With multiple solutions available, finding the best one can be challenging. Independent te...
Cмотреть видео
Cмотреть видео
Check Point: Tutorial: Configuring IPS Settings with R80 Security Management Server | Advanced Threa
How to use R80 SmartConsole to configure the settings for the IPS Software Blade. For more information visit:
Cмотреть видео
Cмотреть видео
Check Point: Anti-Ransomware: Tecnología y Demostración
Anti-Ransomware protege contra el ransomware de día cero. Está incluido en el paquete de SandBlast Agent. Este video presenta la descripción de la solución seguido por una demonstración. Anti-Ransomware usa las habilidades del análisis for...
Cмотреть видео
Cмотреть видео
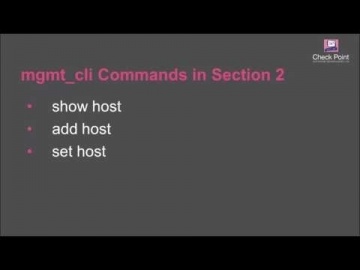
Check Point: Creating Host Objects with R80 Management API Tutorial | Security Management Tutorial
How to use R80 Management API to run a BASH script that automatically creates host objects in the Security Management server database. For more information: This video tutorial is intended for users that are familiar with automation scri...
Cмотреть видео
Cмотреть видео
Check Point: Overview of SandBlast Agent Forensics Report | Tech Bytes
This video provides an overview of SandBlast Agent’s Forensics Report. SandBlast Agent defends endpoints and web browsers with a complete set of real-time advanced browser and endpoint protection technologies, including Threat Emulation, T...
Cмотреть видео
Cмотреть видео
Check Point: Artificial Intelligence: a Silver Bullet in Cyber Security? CPX 360 Keynote
Artificial Intelligence is the Industrial Revolution of our time. It is already reshaping our world and is likely to transform practically every facet of our human lives. Learn more here: Fighting cybercrime is one of its many application...
Cмотреть видео
Cмотреть видео
Check Point: Software Opens NASDAQ on 15th Year Anniversary of IPO
Founder, chairman and CEO, Gil Shwed, along with Tal Payne, the chief financial officer, and the company's board of directors participated in The NASDAQ Opening Bell ceremony at The NASDAQ Stock Market on Tuesday, June 28, 2011. The ceremon...
Cмотреть видео
Cмотреть видео
Check Point: Evolving Role of the CISO - A Customer Story
In this session, CISO Joey Smith will discuss his understanding of the importance of compliance and security and their differences. For more information: Additionally, he will review what he has personally learned from his experience as...
Cмотреть видео
Cмотреть видео
Check Point: Pokemon GO Repackaged Malware Demonstration | SandBlast Mobile Security Demo
The excitement over the new game Pokemon GO has taken the world by storm. Because it's available only in limited countries right now, some people may be tempted to download the app from sources other than Google Play or the Apple App Store....
Cмотреть видео
Cмотреть видео
Check Point: Daymark Secures Cloud with CloudGuard (formerly vSEC) for Microsoft Azure | Cloud Secur
Daymark solutions, trusted advisor to businesses in the Northeast, implemented CloudGuard (formerly vSEC) for Microsoft Azure and now recommends it to all its customers for ease of use, comprehensive visibility and threat prevention. Hea...
Cмотреть видео
Cмотреть видео
Check Point: Daymark Secures Cloud with CloudGuard (formerly vSEC) for Microsoft Azure | Cloud Secur
Daymark solutions, trusted advisor to businesses in the Northeast, implemented CloudGuard (formerly vSEC) for Microsoft Azure and now recommends it to all its customers for ease of use, comprehensive visibility and threat prevention. Hea...
Cмотреть видео
Cмотреть видео
Check Point: Anti-Bot Protection | IoT| Network Security
A bot is malicious software that allows cyber criminals to remotely control computers and execute illegal activities such as stealing data, spreading spam and distributing malware. More information: Anti-Bot security software detects bot...
Cмотреть видео
Cмотреть видео
Check Point: ゼロデイの脅威からエンドポイントを保護するSandBlast Agent
脅威の進化に伴い、組織には、あらゆるレベルで攻撃を防ぎ、迅速に対応して被害を抑えるソリューションの導入が推奨されます。SandBlast Agentは、幅広い高度なエンドポイント保護技術により、社内および社外で利用するエンドポイントを保護します。攻撃の全体像をすばやく把握できるフォレンジック分析機能も搭載しており、インシデント・レスポンス・チームの生産性を最大限に高めます。
Cмотреть видео
Cмотреть видео