C#: СОЗДАНИЕ СЕРВЕРА НА RAGE:MP (JS) #1 [События, команды, методы] - видео → Похожие видео ролики , Страница 17
Изучим как работают события, создаются команды, методы подключения скриптов с сервера на клиентскую часть и наоборот, в конце в качестве закрепляющего материала, создадим первый наш клиентский ресурс, на основе записей форума.
Подробнее в видео...
Подробнее в видео...
HD 00:03:13
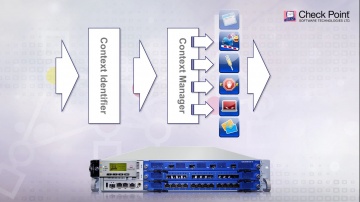
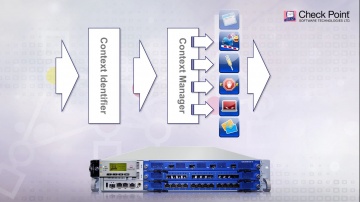
Check Point: Managing Security Policy Changes with R80.10 | Tech Bytes
When new services are introduced and your security policy needs to be adjusted accordingly, what tools will you be using? R80.10 makes it easier to implement changes. The “Where Used” and “Replace” tools will help security administrators ma...
Cмотреть видео
Cмотреть видео
HD 00:06:47
Check Point: Unveils New Network Security Appliance Models
Gabi Reish, Head of Product Management at Software Technologies, introduces the new 2012 line of Appliances. For more information: provides organizations of all sizes with the latest data and network security protection in an integrated...
Cмотреть видео
Cмотреть видео
HD 00:19:45
Check Point: How to Hack a Cell Phone | Demo for Understanding Mobile Security
Want to hack a Smartphone? A hands-on approach to understanding mobile security. Learn more here: Ever wanted to know how to hack a smartphone? Join this exciting live demo to see first-hand how easy it is! Learn more:
Cмотреть видео
Cмотреть видео
HD 00:44:57
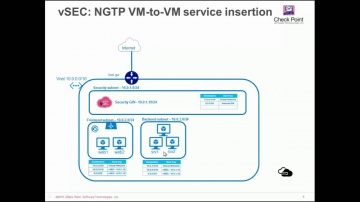
Check Point: vSEC for Microsoft Azure Hybrid Cloud : Deployment Scenarios and Demo
Cloud Security Architect provides overview of deployment scenarios, use cases and demos vSEC for Microsoft Azure for Hybrid Cloud.
Cмотреть видео
Cмотреть видео
HD 00:00:54
Check Point: 01 Installing the Management Server Hotfix
Install the Hotfix on Gaia R77.30 Security Management Server and R77.20/R77.30 Security Gateways. It is required for both the vSEC Gateway and the vSEC Controller.
Cмотреть видео
Cмотреть видео
HD 00:02:24
Check Point: Stop Advanced Mobile Threats Before They Start | SandBlast Mobile Security
Learn More: Report: IDC Technology Spotlight: Why Comprehensive Security Requires Mobile Threat Prevention: Cyber criminals may be stealing data from your smartphone or tablet without your knowledge. They’re experts at exploiting vulner...
Cмотреть видео
Cмотреть видео
HD 00:22:53
Check Point: Gen V Cyber Security with Moti Sagey - CPX 360
In his keynote, Moti Sagey will discuss in a pragmatic fact based way what it takes to build a Gen V security solution and how the cyber landscape matches the must have for effective security.
Cмотреть видео
Cмотреть видео
HD 00:01:43
Check Point: Malware Threat Prevention | Zero-Day, Zero-Second.
What can malware do in 60 seconds? One minute can change everything for a business. So what happens when the speed of business is overtaken by the speed of malware? The team devised a test to quantify that exact question. Learn More: As ...
Cмотреть видео
Cмотреть видео
HD 00:03:11
Check Point: Choose the Right Next Generation Firewall - Multi-Layer Security
Why Multi-Layer Security and how 's Software Blade Architecture is the most secure and scalable solution in this market. For more information: provides organizations of all sizes with the latest data and network security protection in a...
Cмотреть видео
Cмотреть видео
HD 00:03:11
Check Point: Choose the Right Next Generation Firewall - Multi-Layer Security
Why Multi-Layer Security and how 's Software Blade Architecture is the most secure and scalable solution in this market. For more information: provides organizations of all sizes with the latest data and network security protection in a...
Cмотреть видео
Cмотреть видео
HD 01:04:31
Check Point: Webinar replay – Auto-scale advanced security for Microsoft Azure
For more information visit: Webinar replay - hear from customer George Dialectakis, IT Consultant at Eversource Energy, on how they leverage CloudGuard IaaS advanced threat prevention security for their Microsoft Azure cloud environme...
Cмотреть видео
Cмотреть видео
HD 00:01:48
Check Point: Mobile Security: Capsule
Introducing Capsule – Your Complete Secure Mobility Solution. Learn More: Only provides ONE solution that addresses ALL your mobile security needs: Protect devices (smartphones, tablets, and laptops) from threats everywhere, establish a...
Cмотреть видео
Cмотреть видео
HD 00:01:58
Check Point: Threat Prevention: Receives Top Marks For Zero-Day Malware Block Rates
In a world of ever-changing cyber threats, organizations are facing the unprecedented growth of unknown malware. These attacks focus on stealing data, sabotaging business continuity, or damaging a company’s reputation. To protect against th...
Cмотреть видео
Cмотреть видео
HD 00:04:23
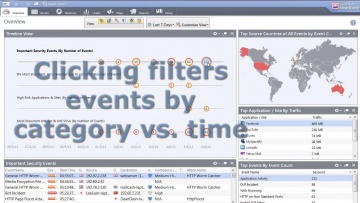
Check Point: SmartEvent | Security Management Walk-Through
Are you tired of managing security by manually searching through millions of logs to find the information you need? There is a better way! Watch this SmartEvent Video to learn how to manage your security more efficiently. For more informa...
Cмотреть видео
Cмотреть видео
HD 00:01:12
Check Point: : A Founding Member of the AirWatch Mobile Security Alliance | Mobile Threat Prevention
President Amnon Bar-Lev addresses the audience during the keynote speech at AirWatch Connect 2015 in Atlanta on September 22, 2015, and announces ’s participation as a founding member of the AirWatch Mobile Security Alliance.
Cмотреть видео
Cмотреть видео
00:05:37
Check Point: Why Trust Matters for Security
Following a press round table event held in London in December 2012, panelists looked at why trust is fundamental to security, and how organizations can prove that they and their employees can be trusted. The spokespeople are: - Kevin B...
Cмотреть видео
Cмотреть видео
HD 00:02:05
Check Point: Secure your Mobile Phone Now | Introducing SandBlast Mobile
Protecting your enterprise from mobile threats and cyber attacks. More information: Worried about your Mobile Privacy? Secure your mobile phone now against mobile threats. Keeping your business safe from cyberattacks is no easy task, and...
Cмотреть видео
Cмотреть видео
HD 00:03:49
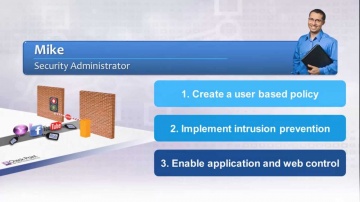
Check Point: A Day in the Life of Mike, a Next Generation Firewall Administrator
For more information: See how security admins can easily create granular policies—based on users or groups—to identify, block or limit usage of over Web 2.0 applications and educate users on safe Internet use with our Next Generation Fire...
Cмотреть видео
Cмотреть видео
HD 00:02:10
Check Point: SandBlast Mobile: Protecting Against Malicious Apps
Our mobile devices are used for both personal and business purposes. Installing new apps may compromise both your private and corporate data. Every year, malicious apps downloaded from official app stores infect millions of mobile devices....
Cмотреть видео
Cмотреть видео
HD 00:00:40
Check Point: Customer Quote: Industry Leading NGFW Performance with Integrated Management
Gimv IT Manager Kristof Poppe comments on 's industry leading next generation firewall performance with integrated management.
Cмотреть видео
Cмотреть видео
HD 00:02:24
Check Point: SandBlast Mobile: How It Works
Accurate threat detection is a critical component of preventing advanced attacks on smartphones and tablets. Traditional mobile anti-virus, signature-based solutions identify known threats, but they can't detect zero-day malware or apps tha...
Cмотреть видео
Cмотреть видео
HD 00:02:20
Check Point: SandBlast Prevents Ransomware at the Mississippi Secretary of State
Learn more about how SadBlast helped Mississippi's Secretary of State here: The Mississippi Secretary of State was spending a lot of time remediating attacks on the endpoint. Seeking to enhance endpoint security, the agency adopted Sand...
Cмотреть видео
Cмотреть видео
HD 00:01:56
Check Point: Defeats Mobile Cyberattacks
Advanced cybercrimes aren’t science fiction; they’re real – and have real consequences. is at the forefront of mobile security, ensuring that devices and data everywhere remain safe. We don’t just build cutting edge technology: we stand be...
Cмотреть видео
Cмотреть видео
HD 00:02:24
Check Point: SandBlast Prevents Ransomware at the Mississippi Secretary of State
Learn more about how SadBlast helped Mississippi's Secretary of State here: Concerned about mounting advanced threats, the mississippi Secretary of state adopts SandBlast. Just 2 days after deployment, SandBlast prevents a ransomware at...
Cмотреть видео
Cмотреть видео
HD 00:02:58
Check Point: Customer Success Video: MLB Network Maintains 100 Percent Network Uptime
The MLB Network turns to to help launch the cable network and achieve 100 percent uptime. 's easy, flexible and scalable security solution enables the MLB Network to maintain zero downtime and address the needs of its viewing fans in 70 m...
Cмотреть видео
Cмотреть видео
HD 00:01:04
Check Point: RSA Conference 2014 - Partner Insights -- Christina Ebert, Business Development Manager
Find out more: speaks with customers and partners at RSA Conference 2014 in San Francisco. Watch as Christina Ebert of Avnet shares her thoughts about distribution and mobility as major issues her customers are facing. She also shares...
Cмотреть видео
Cмотреть видео
HD 00:03:05
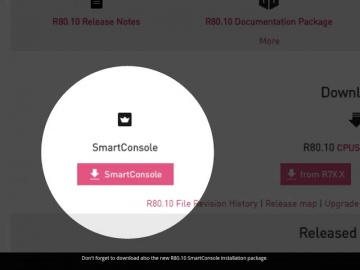
Check Point: Migrating from R77.3O to R80.10 Using Advanced Upgrade Procedure
This video demonstrates advanced upgrade of a real customer database from R77.30 to R80.10.
Cмотреть видео
Cмотреть видео
HD 00:01:53
Check Point: Customer Insights -- Michael Wood, HP Enterprise Services
Find out more: speaks with customers and partners at RSA Conference 2014 in San Francisco. Watch as Michael Wood of HP Enterprise Services shares what makes him a fan.
Cмотреть видео
Cмотреть видео
HD 00:01:06
Check Point: RSA Conference 2014 - Customer Insights - Joseph Royal, Network Security Manager, Leido
Find out more: speaks with customers and partners at RSA Conference 2014 in San Francisco. Watch as Joseph Royal of Leidos shares what makes him a fan.
Cмотреть видео
Cмотреть видео