C#: СОЗДАНИЕ СЕРВЕРА НА RAGE:MP (JS) #1 [События, команды, методы] - видео → Похожие видео ролики , Страница 16
Изучим как работают события, создаются команды, методы подключения скриптов с сервера на клиентскую часть и наоборот, в конце в качестве закрепляющего материала, создадим первый наш клиентский ресурс, на основе записей форума.
Подробнее в видео...
Подробнее в видео...
HD 00:01:41
Check Point: From HummingBad to Worse: Android Malware Campaign | SandBlast Mobile Security
For five months, mobile threat researchers had unprecedented access to the inner-workings of Yingmob, the Chinese cyber criminals behind HummingBad, a malware that establishes a persistent rootkit on Android devices, generates fraudulent a...
Cмотреть видео
Cмотреть видео
00:18:31
Check Point: The Security Zone Ep. 5: Impact of Mobile Devices on Information Security
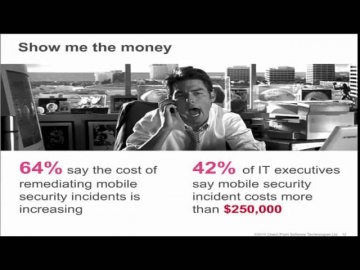
teamed up with Dimensional Analysis to survey over 700 IT and security professionals in 6 countries to learn the current attitudes and trends regarding the impact of mobile devices on information security.
Cмотреть видео
Cмотреть видео
HD 00:02:22
Check Point: Malware Protection 2018 - Public Health Service Prevents, Not Just Detects, Advanced Th
For more information: Malware Protection in 2018 is about prevention not just detection. As a leading West Coast provider of emergency health services, this Public Health Service organization has over two million patients and runs over...
Cмотреть видео
Cмотреть видео
HD 00:01:41
Check Point: Viking Horde: A New Type of Android Malware on Google Play | Mobile Security
Blog: More information: The research team uncovered a new Android malware campaign on Google Play it calls Viking Horde. Viking Horde conducts ad fraud, but can also be used for other attack purposes such as DDoS attacks, spam messages...
Cмотреть видео
Cмотреть видео
HD 00:38:04
Check Point: Identifying The Best Sandboxing Solution Featuring Miercom | Advanced Threat Prevention
Learn More: Protecting against known, and new, advanced, unknown threats requires the most rapid and precise detection and protection technologies. With multiple solutions available, finding the best one can be challenging. Independent te...
Cмотреть видео
Cмотреть видео
HD 00:03:30
Check Point: Tutorial: Configuring IPS Settings with R80 Security Management Server | Advanced Threa
How to use R80 SmartConsole to configure the settings for the IPS Software Blade. For more information visit:
Cмотреть видео
Cмотреть видео
HD 00:07:14
Check Point: Creating Host Objects with R80 Management API Tutorial | Security Management Tutorial
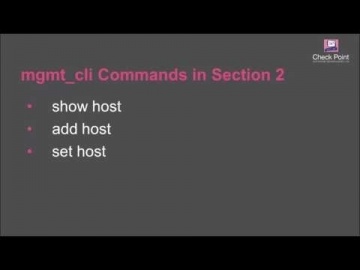
How to use R80 Management API to run a BASH script that automatically creates host objects in the Security Management server database. For more information: This video tutorial is intended for users that are familiar with automation scri...
Cмотреть видео
Cмотреть видео
HD 00:03:59
Check Point: Pokemon GO Repackaged Malware Demonstration | SandBlast Mobile Security Demo
The excitement over the new game Pokemon GO has taken the world by storm. Because it's available only in limited countries right now, some people may be tempted to download the app from sources other than Google Play or the Apple App Store....
Cмотреть видео
Cмотреть видео
HD 00:02:13
Check Point: Daymark Secures Cloud with CloudGuard (formerly vSEC) for Microsoft Azure | Cloud Secur
Daymark solutions, trusted advisor to businesses in the Northeast, implemented CloudGuard (formerly vSEC) for Microsoft Azure and now recommends it to all its customers for ease of use, comprehensive visibility and threat prevention. Hea...
Cмотреть видео
Cмотреть видео
HD 00:02:13
Check Point: Daymark Secures Cloud with CloudGuard (formerly vSEC) for Microsoft Azure | Cloud Secur
Daymark solutions, trusted advisor to businesses in the Northeast, implemented CloudGuard (formerly vSEC) for Microsoft Azure and now recommends it to all its customers for ease of use, comprehensive visibility and threat prevention. Hea...
Cмотреть видео
Cмотреть видео
HD 00:04:12
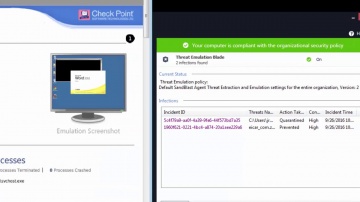
Check Point: SandBlast Agent Protects From Advanced Zero-day Malware
What happens if employees roam outside enterprise network that protect them from advanced zero-day invasions? For more information: SandBlast Agent protects the enterprise end-points from advanced zero-day malware, by using advanced C-P-U...
Cмотреть видео
Cмотреть видео
HD 00:04:02
Check Point: SideStepper: Anatomy of an iOS Vulnerability | Mobile Threat Prevention
For more information, visit: Report: IDC Technology Spotlight: Why Comprehensive Security Requires Mobile Threat Prevention: disclosed details about SideStepper, a vulnerability that can be used to install malicious enterprise apps o...
Cмотреть видео
Cмотреть видео
HD 00:01:48
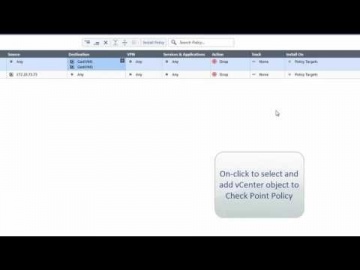
Check Point: vSEC controller Demo with R80 Smart Management | Cloud Security
This video demos the vSEC cloud security integration with VMware vCenter and NSX. It shows you how to integrate a vCenter server in the Smart Console, provision a security rule based on imported vCenter objects like VM name, integrate wit...
Cмотреть видео
Cмотреть видео
HD 00:02:11
Check Point: R80 Streamlines Security Management at Appvion | Data Center Security
Appvion, a manufacturer of specialty papers, tested R80 security management during development and now uses it every day to gain efficiency, high visibility and concurrent management capabilities.
Cмотреть видео
Cмотреть видео
HD 00:20:33
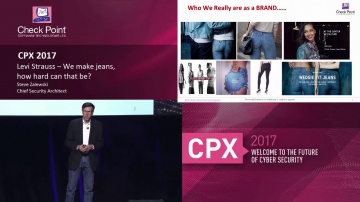
Check Point: We Make Jeans; How Hard Can That Be?
This talk will present some of the business challenges, experiences and road maps from a security perspective to protect the global Levi Brand. Steve Zalewski, Chief Security Architect, Levi Strauss For more information:
Cмотреть видео
Cмотреть видео
HD 00:02:35
Check Point: SandBlast Agent Backs Up Anti-Virus by Preventing Recently Discovered Malware | Tech By
What happens if your anti-virus signature database is not updated with a very recently discovered malware? SandBlast Agent defends endpoints with a complete set of real-time advanced endpoint protection technologies, by using the up-to-date...
Cмотреть видео
Cмотреть видео
HD 00:00:39
Check Point: Automation with VMware vCenter Orchestrator and R80 Smart Management
Use VMware vCenter Orchestrator to provision security policies in Ûªs R80 Smart Management Console leveraging the open API interface. This video demos automated security policy provisioning. Rules that are provisioned include Stealth rul...
Cмотреть видео
Cмотреть видео
HD 00:01:32
Check Point: SandBlast Mobile Security: Man-in-the-Middle Mobile Attacks
Our mobile devices are more vulnerable then we think. A man-in-the middle attack is a potential threat every time you connect to a Wi-Fi network. For more information: Imagine you are at a coffee shop and you want to connect to Wi-Fi and...
Cмотреть видео
Cмотреть видео
HD 00:02:46
Check Point: Denham Capital Enjoys Agility and Security in the vSEC Protected Microsoft Azure Cloud
More information: A leading private equity firm with great success in the often unpredictable energy industry, Denham Capital needed to move to the cloud for increased agility without compromising security. With Microsoft Azure and vSEC ...
Cмотреть видео
Cмотреть видео
00:02:36
Check Point: Global TV Interviews Kellman Meghu
Software Technologies Ltd. — крупнейший в мире поставщик в области безопасности. Компания предлагает покупателям ведущие в индустрии решения и защищает покупателей от кибератак с непревзойденным уровнем успешного обнаружения вре...
Cмотреть видео
Cмотреть видео
HD 00:01:25
Check Point: R80 Security Management | Advanced Threat Prevention
's R80 Security Management helps you consolidate security functions so you can be more efficient and effective at deploying the strongest protections across your organization. More Information:
Cмотреть видео
Cмотреть видео
HD 00:02:17
Check Point: Big Bad Mobile Threats of 2015 - Mobile Threat Prevention
The mobile threat landscape changed dramatically in 2015. Simple hacks and rudimentary malware was quickly replaced by sophisticated cyber thieves who know exactly what sensitive data they can take from you and how. Along with the growing s...
Cмотреть видео
Cмотреть видео
HD 00:17:56
Check Point: Hacking the Smartphone | Mobile Cyber Hack Demonstration
Live demonstration of a smartphone hack, from Experience 2017. For more information visit: Watch Michael Shaulov, Head of Mobility Products at Software hack a smart phone in real time. Today every business is a mobile business, with req...
Cмотреть видео
Cмотреть видео
HD 00:04:03
Check Point: Use R80.10 New Packet Mode Feature to Search Through Policy
Packet Mode, a new feature introduced within R80.10, enables you to search the rule base as if it were a packet going through the security policy. For more information visit: R80.10 features the most advanced threat prevention across netw...
Cмотреть видео
Cмотреть видео
HD 00:01:44
Check Point: Security Management Customer Success Story: Talisys | R80 Security Management
More information on R80 Security Management visit Talisys, an innovator in financial securities processing software, leverages R80 to reduce security management complexity. Building on Ûªs leadership in speedy root cause analysis, they a...
Cмотреть видео
Cмотреть видео
HD 00:01:34
Check Point: DressCode Android Malware Discovered on Google Play | SandBlast Mobile Security | Andro
The mobile threat prevention research team discovered a new Android malware on Google Play, called DressCode, which was embedded into more than 40 apps, and found in more than 400 additional apps on third party app stores. notified Google...
Cмотреть видео
Cмотреть видео
HD 00:18:47
Check Point: Gil Shwed & Marius Nacht Interview - Milan 2017
Gil Shwed & Marius Nacht discuss product innovation and the Experience over the years. For more information:
Cмотреть видео
Cмотреть видео
HD 00:20:42
Check Point: Microsoft Azure and CloudGuard - Intelligent Cloud Security - CPX 360 2018
In his keynote, Avi Ben Menahem, Director of Azure Security Microsoft will discuss what it takes to build and operate a secure cloud platform, the approach the team at Microsoft takes to secure Azure, and the importance of a strong develope...
Cмотреть видео
Cмотреть видео
HD 00:02:29
Check Point: 24/7 Protection with ThreatCloud Managed Security Service | Threat Prevention
For more information visit ThreatCloud Managed Security Service is a cloud-based service providing actionable attack alerts for IPS, Anti-Bot and Antivirus customers. experts remotely monitor, manage and escalate attack incidents. Custo...
Cмотреть видео
Cмотреть видео
HD 00:03:39
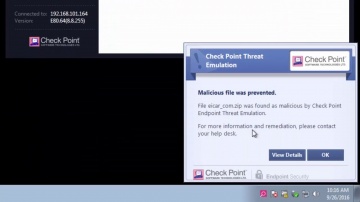
Check Point: Mobile Threat Prevention Demo - Malware Invasion on an iOS Device
In this video, demonstrates an end-to-end threat and remediation situation on an iOS device using Mobile Threat Prevention. To learn more about Mobile Threat Prevention for iOS and Android devices, visit Report: IDC Technology Spotligh...
Cмотреть видео
Cмотреть видео