Безопасность
218 роликов  Data Loss Prevention - DLP - ПО для предотвращения утечек конфиденциальной информации/данных.
Data Loss Prevention - DLP - ПО для предотвращения утечек конфиденциальной информации/данных.
 Data Loss Prevention - DLP - ПО для предотвращения утечек конфиденциальной информации/данных.
Data Loss Prevention - DLP - ПО для предотвращения утечек конфиденциальной информации/данных. Предотвращение утечки данных, DLP
Обеспечение информационной безопасности, борьба с киберпреступностью. ИТ-безопасность.
Check Point: Gil Shwed & Marius Nacht Interview - Milan 2017
Gil Shwed & Marius Nacht discuss product innovation and the Experience over the years. For more information:
Cмотреть видео
Cмотреть видео
Check Point: Understanding SandBlast - Zero-Day Protection
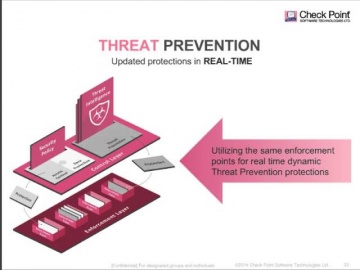
Understanding your exposure to threats—and what you can do about it is not only responsible business management—it’s critical to business survival. More information: Turn Security into an Enabler, Not a Disabler. SandBlast Zero-Day Prote...
Cмотреть видео
Cмотреть видео
Check Point: - CNN Report a Gil Shwed (sub español)
CNN analiza en este informe la creación de Gil Shwed, , una empresa dedicada a la creación de soluciones en el ámbito de la seguridad informática.
Cмотреть видео
Cмотреть видео
Check Point: DressCode Android Malware Discovered on Google Play | SandBlast Mobile Security | Andro
The mobile threat prevention research team discovered a new Android malware on Google Play, called DressCode, which was embedded into more than 40 apps, and found in more than 400 additional apps on third party app stores. notified Google...
Cмотреть видео
Cмотреть видео
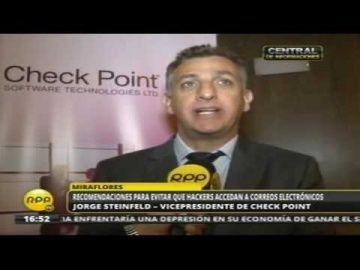
Check Point: Jorge Steinfeld, Software; Entrevista en RPP TV
Software Technologies Ltd. — крупнейший в мире поставщик в области безопасности. Компания предлагает покупателям ведущие в индустрии решения и защищает покупателей от кибератак с непревзойденным уровнем успешного обнаружения вре...
Cмотреть видео
Cмотреть видео
Check Point: Building a Secure Platform as CIO - CPX 360 Keynote
In his keynote, Sharon Schusheim will discuss what it takes to build and operate a secure platform as a CIO. For more information: CPX 360 promises to be the premier cyber security summit. For the first time, we will bring our customers...
Cмотреть видео
Cмотреть видео
Check Point: âÈâ_Ä´Ä»Ä â£¨Á ¨üÈ¡_¾¬©âÕÐâ_¾öȪR80
Äâ¤ÄÄâøÄÈÄâ_Ä_Äö¨R80âÈâ_Ä´Ä»Ä â£¨Á ÄÑÄ©ÄÄÄöÄ¥â©Ä_ÄÊøÛââäâ âÜÄ_Ä_â¦ÛÄàÄâ_â_ÛÄàÄ_âÀÛâ¢ÄÑÄ»â±Ä_âáĤÄ_âÕ÷üÛ¨â_Ä_â_Ä_ÄǬµ±üÛÎÐ¥âÎÙÄÄ»âáÄ_¤¨Á ÛâÇ÷¼_...
Cмотреть видео
Cмотреть видео
Check Point: Customer Success: Community Newspaper Group (CNG)
Watch as Infrastructure Manager, Michael Brine discusses his experience with SandBlast Agent in this customer success video. Community Newspaper Group's seventeen newspapers provide readers with the latest in local news, sports, and ente...
Cмотреть видео
Cмотреть видео
Check Point: and VMware Partnership delivers advanced security for the SDDC | Cloud Security
More Information: VMware and Partnership delivers advanced security for the Software-Defined Data Center. vSEC integration with VMware NSX delivers dynamic orchestration of advanced threat prevention for all traffic in the Software-Def...
Cмотреть видео
Cмотреть видео
Check Point: Security Management Customer Success Story: Talisys | R80 Security Management
More information on R80 Security Management visit Talisys, an innovator in financial securities processing software, leverages R80 to reduce security management complexity. Building on Ûªs leadership in speedy root cause analysis, they a...
Cмотреть видео
Cмотреть видео
Check Point: Software - 20 Years of Innovation
An overview in pictures of key milestones in 's 20 year history
Cмотреть видео
Cмотреть видео
Check Point: Use R80.10 New Packet Mode Feature to Search Through Policy
Packet Mode, a new feature introduced within R80.10, enables you to search the rule base as if it were a packet going through the security policy. For more information visit: R80.10 features the most advanced threat prevention across netw...
Cмотреть видео
Cмотреть видео
Check Point: The Threat of Bots and Botnets | IoT | Network Security
Learn More: explains: What is a bot? What is a botnet? What is an Advance Persistent Threat?
Cмотреть видео
Cмотреть видео
Check Point: Presentan lo ̼ltimo en seguridad informatica, Cloud Computing y VirtualizaciÌ_n
Software Technologies Ltd. — крупнейший в мире поставщик в области безопасности. Компания предлагает покупателям ведущие в индустрии решения и защищает покупателей от кибератак с непревзойденным уровнем успешного обнаружения вре...
Cмотреть видео
Cмотреть видео
Check Point: CeBIT Global Conferences - Interview with Amnon Bar-Lev, Software Technologies
For five days of the year, CeBIT is the pulsing heart of the digital industry. More than 4,000 companies from over 70 countries showcased the latest innovations from the high-tech sector. Get more information about CeBIT at !
Cмотреть видео
Cмотреть видео
Check Point: Hacking the Boardroom - CPX 360 2018
Cybersecurity is a boardroom discussion for enterprise corporations globally. In this fun & entertaining presentation, you will learn how to approach senior executive for an effective discussion on Cybersecurity & how the Internet of Everyt...
Cмотреть видео
Cмотреть видео
Check Point: Hacking the Smartphone | Mobile Cyber Hack Demonstration
Live demonstration of a smartphone hack, from Experience 2017. For more information visit: Watch Michael Shaulov, Head of Mobility Products at Software hack a smart phone in real time. Today every business is a mobile business, with req...
Cмотреть видео
Cмотреть видео
Check Point: vSEC for VMware NSXで実現するSoftware-Defined Datacenter (SDDC)による高度なセキュリティ
チェック・ポイントのvSEC for VMware NSX は、VMware NSX と連携し、SDDCにおけるすべてのトラフィックを高度な脅威から防御する動的なオーケストレーションを実現します。 製品情報はこちらhttp://www.checkpoint.co.jp/products/vsec-vmware-nsx/index.html
Cмотреть видео
Cмотреть видео
Check Point: Hunze en Aa Water Resource Board enhances Network Security, SCADA Systems with SandBlas
For more information: To help ensure safe operation of its pumping stations and other key systems, the Hunze en Aa Water Resource Board implemented NGTX appliances with SandBlast zero-day protection. Through the solutions centralized mana...
Cмотреть видео
Cмотреть видео
Check Point: Big Bad Mobile Threats of 2015 - Mobile Threat Prevention
The mobile threat landscape changed dramatically in 2015. Simple hacks and rudimentary malware was quickly replaced by sophisticated cyber thieves who know exactly what sensitive data they can take from you and how. Along with the growing s...
Cмотреть видео
Cмотреть видео
Check Point: 600 Security Appliance: One Box, Complete Protection | SMB Cyber Security
Learn more about the 600 appliance: The 600 provides a complete security package with firewall, VPN, antivirus, intrusion prevention and more, at a price your small business can afford.
Cмотреть видео
Cмотреть видео
Check Point: Partner Success Story - RoundTower on vSEC Solution | Cloud Security
For More Information: ... Partner Round Tower shares a vSEC success story highlighting the features and benefits of vSEC for VMware NSX advanced security for the Software-Defined Data Center. vSEC integration with VMware NSX delivers dyn...
Cмотреть видео
Cмотреть видео
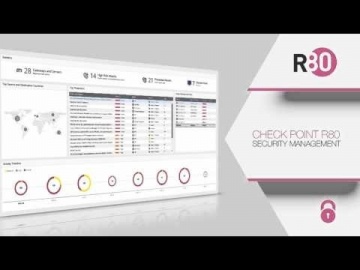
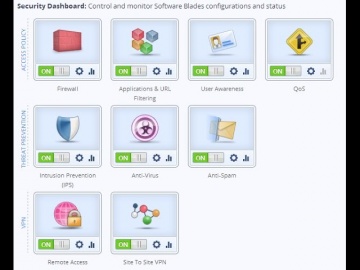
Check Point: R80 Security Management | Advanced Threat Prevention
's R80 Security Management helps you consolidate security functions so you can be more efficient and effective at deploying the strongest protections across your organization. More Information:
Cмотреть видео
Cмотреть видео
Check Point: SandBlast Agent Anti-Bot Protects the Endpoint from Bot Invasions | Tech Bytes
What happens if employees roam outside enterprise network that protect them from Bot invasions? SandBlast Agent protects the enterprise endpoints from Bot threats, by detecting the communication with command-and-control server. Its Anti-Bot...
Cмотреть видео
Cмотреть видео
Check Point: Cyber Security Plays Offense | Cyber Security
For more information: Gil Shwed, CEO of talks to James Rogers of TheStreet.com
Cмотреть видео
Cмотреть видео
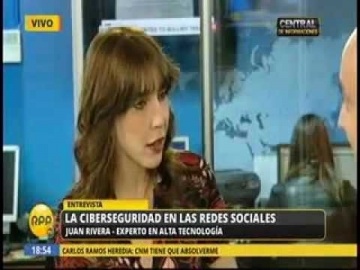
Check Point: Juan Rivera, habla sobre seguridad en redes sociales
Juan Rivera, Gerente Regional de Cono Sur
Cмотреть видео
Cмотреть видео
Check Point: Tackling a Complex Threat Landscape with Software-defined Protection
Description: In this 30-minute webinar we'll examine software-defined protection (SDP). This new architecture addresses today's security challenges by providing operational resilience and real-time, proactive protection. You'll learn: • ...
Cмотреть видео
Cмотреть видео
Check Point: Global TV Interviews Kellman Meghu
Software Technologies Ltd. — крупнейший в мире поставщик в области безопасности. Компания предлагает покупателям ведущие в индустрии решения и защищает покупателей от кибератак с непревзойденным уровнем успешного обнаружения вре...
Cмотреть видео
Cмотреть видео
Check Point: SMB Cyber Security - 600 Appliance Setup
Small businesses need cost-effective security that provides robust protections and ease of use. For more information: brings its long-standing history of security expertise to a range of solutions optimized for the unique demands of smal...
Cмотреть видео
Cмотреть видео
Check Point: Internet of Things: The Dangers of IoT - CPX 360 2018
The concept of Internet of Things (IoT) truly represents a radical shift in how companies will operate, governments will govern and individuals will live their lives. Micro compute technologies and autonomous systems will permeate our day-t...
Cмотреть видео
Cмотреть видео