Безопасность
218 роликов  Data Loss Prevention - DLP - ПО для предотвращения утечек конфиденциальной информации/данных.
Data Loss Prevention - DLP - ПО для предотвращения утечек конфиденциальной информации/данных.
 Data Loss Prevention - DLP - ПО для предотвращения утечек конфиденциальной информации/данных.
Data Loss Prevention - DLP - ПО для предотвращения утечек конфиденциальной информации/данных. Предотвращение утечки данных, DLP
Обеспечение информационной безопасности, борьба с киберпреступностью. ИТ-безопасность.
Check Point: RSA Conference 2014 - Customer Insights - Wanjiru Allen, Sr. Systems Admin., Florida Po
Find out more: speaks with customers and partners at RSA Conference 2014 in San Francisco. Watch as Wanjiru Allen of Florida Power & Light talks about 's management and ease of use. She also shares what makes her a fan.
Cмотреть видео
Cмотреть видео
Check Point: RSA Conference 2014 - Customer Insights -- Michael Wood, Network & Systems Admin., HP
Find out more: speaks with customers and partners at RSA Conference 2014 in San Francisco. Watch as Michael Wood of HP Enterprise Services shares what makes him a fan.
Cмотреть видео
Cмотреть видео
Check Point: RSA Conference 2014 - Partner Insights -- Joe Luciano, CEO, AccessIT Group
Find out more: speaks with customers and partners at RSA Conference 2014 in San Francisco. Watch as Joe Luciano of AccessIT Group shares why he's is a fan.
Cмотреть видео
Cмотреть видео
Check Point: RSA Conference 2014 - Customer Insights -- Leon Johnson, CISO, Securities America, Inc.
Find out more: speaks with customers and partners at RSA Conference 2014 in San Francisco. Watch as Leon Johnson of Securities America, Inc. speaks about the critical need to secure data in the financial industry and how integrates di...
Cмотреть видео
Cмотреть видео
Check Point: Partner Insights -- Jason Lawrence, Sr. Network Security Advisor, Dataway
Find out more: speaks with customers and partners at RSA Conference 2014 in San Francisco. Watch as Jason Lawrence of Dataway shares insights about 's model of annualized service behind its software blade architecture as well as 's cen...
Cмотреть видео
Cмотреть видео
Check Point: Migrating from R77.3O to R80.10 Using Advanced Upgrade Procedure
This video demonstrates advanced upgrade of a real customer database from R77.30 to R80.10.
Cмотреть видео
Cмотреть видео
Check Point: RSA Conference 2014 - Customer Insights -- Jaime Lopez, Director of IS, Verisight, Inc.
Find out more: speaks with customers and partners at RSA Conference 2014 in San Francisco. Watch as Jaime Lopez of Verisight, Inc. shares what makes him a fan.
Cмотреть видео
Cмотреть видео
Check Point: RSA Conference 2014 - Partner Insights -- Shannon Rodelander, X-Series Sales Rep., Blue
Find out more: speaks with customers and partners at RSA Conference 2014 in San Francisco. Watch as Shannon Rodelander of Blue Coat Systems speaks about issues like Cloud Security and Cost of Performance affecting her customers. She a...
Cмотреть видео
Cмотреть видео
Check Point: Overview of the 61000 Appliance - with Japanese subtitles
For more information:
Cмотреть видео
Cмотреть видео
Check Point: 2017 Cyber Security Survey
Donald Meyer, Head of Marketing, Data Center and Cloud, discusses top security concerns that IT professionals have regarding Cloud and Mobility security. For more information:
Cмотреть видео
Cмотреть видео
Check Point: Without the Best Security, Bad Things Happen
Two chatty security guards get distracted by a shiny coin, and their VIP client is swept away by criminals in a white van. For more information visit Takes real life security scenario, and demonstrates how the standard, traditional methods ...
Cмотреть видео
Cмотреть видео
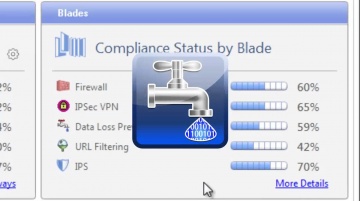
Check Point: Compliance Software Blade Demonstration
Introduction and overview to the Compliance Software Blade and its features and functions.For more information: The Compliance Software Blade monitors your management, Software Blades and security gateways to constantly validate that you...
Cмотреть видео
Cмотреть видео
Check Point: 10 Redirecting traffic to and installing policy
This video demonstrates how to redirect traffic to entities and then install Security policy to the vSEC cluster object.
Cмотреть видео
Cмотреть видео
Check Point: SandBlast Mobile: How It Works
Accurate threat detection is a critical component of preventing advanced attacks on smartphones and tablets. Traditional mobile anti-virus, signature-based solutions identify known threats, but they can't detect zero-day malware or apps tha...
Cмотреть видео
Cмотреть видео
Check Point: Customer Success: AlmavivA Group
Almaviva, Italy's number one Information & Communication Technology provider, describes how Technologies protects the organizations infrastructure.
Cмотреть видео
Cмотреть видео
Check Point: DDoS Protector - Technical Overview | DDoS Protection
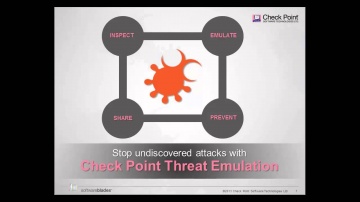
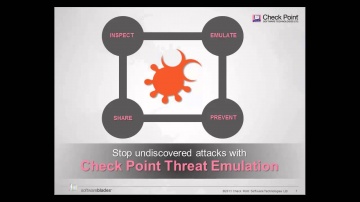
's new Threat Emulation Software Blade prevents infections from undiscovered exploits, zero-day and targeted attacks. For more information: This innovative solution quickly inspects suspicious files, emulates how they run to discover mali...
Cмотреть видео
Cмотреть видео
Check Point: 's Avi Rembaum: Shedding Light on the Dark Web
Leveraging intelligence culled from the Dark Web will help boost information security for enterprises, says Avi Rembaum of Software Technologies. "What's really becoming far more important is leveraging the intelligence coming from that r...
Cмотреть видео
Cмотреть видео
Check Point: Next-Generation Secure Web Gateway | Network Security
Learn More: Are you trying to secure Web 2.0 with 1.0 tools? The Web has evolved, threats have evolved, so should your Web Security! In this video, learn how to best protect against today's web-borne malware and help businesses to get th...
Cмотреть видео
Cмотреть видео
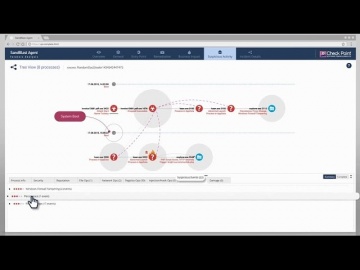
Check Point: SandBlast Agent Forensics
This video shows SandBlast Agent’s automated forensics analysis in action. For more information: It demonstrates SandBlast Agent’s power to instantly provide security teams with a crystal-clear understanding of cyber attacks, empowering t...
Cмотреть видео
Cмотреть видео
Check Point: Threat Emulation Explained by | Advanced Threat Prevention
's Threat new Threat Emulation Software Blade prevents infections from undiscovered exploits, zero-day and targeted attacks. For more information: 's Threat new Threat Emulation Software Blade prevents infections from undiscovered exploit...
Cмотреть видео
Cмотреть видео
Check Point: Threat Emulation Explained by | Advanced Threat Prevention
's Threat new Threat Emulation Software Blade prevents infections from undiscovered exploits, zero-day and targeted attacks. For more information: 's Threat new Threat Emulation Software Blade prevents infections from undiscovered exploit...
Cмотреть видео
Cмотреть видео
Check Point: Protecting Against Spy Eye Bot | Network Security
For more information: Learn how to protect against Spy Eye bot
Cмотреть видео
Cмотреть видео
Check Point: Your Second Pair of Eyes - Compliance Software Blade | Network Security
For more information: Keeping a close eye on security and compliance is a challenging task. The Compliance Software Blade can be your second pair of eyes to constantly monitor your security status, save time in preparing audits and compl...
Cмотреть видео
Cмотреть видео
Check Point: SandBlast Zero-Day Protection | Advanced Threat Prevention
Learn how to take the first steps to enable your security gateway to leverage the SandBlast Cloud Service or the SandBlast Appliance. Learn more at: See what end users would experience, and what security administrators can expect to see. ...
Cмотреть видео
Cмотреть видео
Check Point: Customer Success Video: Hotel Nikko San Francisco
Hotel Nikko relies on its network to support guest services, reservation systems, property management and other critical business operations. Keeping the network safe and secure is key, and even a brief outage means lost revenue, disappoin...
Cмотреть видео
Cмотреть видео
Check Point: Gil Shwed & Marius Nacht Interview - Milan 2017
Gil Shwed & Marius Nacht discuss product innovation and the Experience over the years. For more information:
Cмотреть видео
Cмотреть видео
Check Point: DressCode Android Malware Discovered on Google Play | SandBlast Mobile Security | Andro
The mobile threat prevention research team discovered a new Android malware on Google Play, called DressCode, which was embedded into more than 40 apps, and found in more than 400 additional apps on third party app stores. notified Google...
Cмотреть видео
Cмотреть видео
Check Point: Use R80.10 New Packet Mode Feature to Search Through Policy
Packet Mode, a new feature introduced within R80.10, enables you to search the rule base as if it were a packet going through the security policy. For more information visit: R80.10 features the most advanced threat prevention across netw...
Cмотреть видео
Cмотреть видео
Check Point: 600 Security Appliance: One Box, Complete Protection | SMB Cyber Security
Learn more about the 600 appliance: The 600 provides a complete security package with firewall, VPN, antivirus, intrusion prevention and more, at a price your small business can afford.
Cмотреть видео
Cмотреть видео