itbion.ru / Видео / New video (ENG)
Check Point: Automating vSEC in OpenStack | Tech Bytes
Demo video showcasing automation and orchestration of vSEC Security Gateway in OpenStack (without narration). For more information:
Cмотреть видео
Cмотреть видео
Check Point: Automating vSEC in OpenStack | Tech Bytes
Demo video showcasing automation and orchestration of vSEC Security Gateway in OpenStack (without narration). For more information:
Cмотреть видео
Cмотреть видео
Check Point: 2017 Cyber Security Survey
Donald Meyer, Head of Marketing, Data Center and Cloud, discusses top security concerns that IT professionals have regarding Cloud and Mobility security. For more information:
Cмотреть видео
Cмотреть видео
Check Point: vSEC, The Future of Cloud Security
In this video, you’ll hear from Donald Meyer, Head of Marketing, Data Center and Cloud, where he discusses issues surrounding Cloud security and how organizations can better protect themselves from vulnerabilities in the Cloud. For more in...
Cмотреть видео
Cмотреть видео
Check Point: SandBlast Agent Forensics
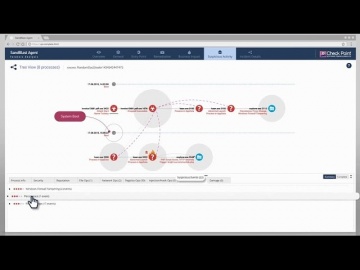
This video shows SandBlast Agent’s automated forensics analysis in action. For more information: It demonstrates SandBlast Agent’s power to instantly provide security teams with a crystal-clear understanding of cyber attacks, empowering t...
Cмотреть видео
Cмотреть видео
Check Point: Anatomy of a Smishing Attack: Czech Posta App
A new smishing attack targeted users in the Czech Republic was discovered January 26, 2017. Smishing, or SMS phishing, is a vector attackers use to send SMS messages from supposedly legitimate organizations. These messages persuade users t...
Cмотреть видео
Cмотреть видео
Check Point: Protecting Mobile Devices Together - ElevenPaths – Telefonica and | Mobile Security
“Mobile devices are critical to the way we do business today. With cyberattacks growing in sophistication and frequency, exposing both the business and personal data we store on smartphones and tablets, mobile devices are the newest enterpr...
Cмотреть видео
Cмотреть видео
Check Point: Hamas’ Cyber Tactics Exposed - Attacking IDF Soldier’s Mobile Phones
The Israeli Defense Forde uncovered a Hamas network that reached out to IDF soldiers online, sometimes in romantic ways, and ask them to download applications that would infect them with Trojan horse viruses. The applications used by Hamas ...
Cмотреть видео
Cмотреть видео
Check Point: vSEC for your AWS Workloads
Utilizing the same security management tool across your hybrid cloud architecture can help your organization be more secure and agile. Maximize the strength of your security posture and capacity for innovation in cloud environments with vSE...
Cмотреть видео
Cмотреть видео
Check Point: Secure Your AWS Apps and Data | Cloud Security
vSEC delivers comprehensive threat prevention security with consolidated management and enforcement for AWS hybrid clouds. For more information:
Cмотреть видео
Cмотреть видео
Check Point: Koch Media Crushes Advanced Attacks with SandBlast | Advanced Threat Prevention
Koch Media develops games globally, which is a process fraught with peril to the intellectual property in their games. Koch sought to replace Cisco and decided on SandBlast Zero DayProtection to crush advanced attacks. For more informat...
Cмотреть видео
Cмотреть видео
Check Point: Daymark Secures Cloud with CloudGuard (formerly vSEC) for Microsoft Azure | Cloud Secur
Daymark solutions, trusted advisor to businesses in the Northeast, implemented CloudGuard (formerly vSEC) for Microsoft Azure and now recommends it to all its customers for ease of use, comprehensive visibility and threat prevention. Hea...
Cмотреть видео
Cмотреть видео
Check Point: Daymark Secures Cloud with CloudGuard (formerly vSEC) for Microsoft Azure | Cloud Secur
Daymark solutions, trusted advisor to businesses in the Northeast, implemented CloudGuard (formerly vSEC) for Microsoft Azure and now recommends it to all its customers for ease of use, comprehensive visibility and threat prevention. Hea...
Cмотреть видео
Cмотреть видео
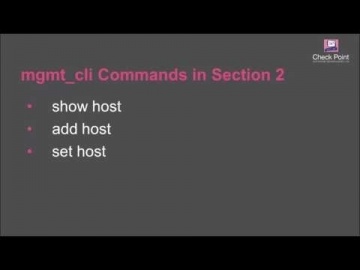
Check Point: Creating Host Objects with R80 Management API Tutorial | Security Management Tutorial
How to use R80 Management API to run a BASH script that automatically creates host objects in the Security Management server database. For more information: This video tutorial is intended for users that are familiar with automation scri...
Cмотреть видео
Cмотреть видео
Check Point: R80 Streamlines Security Management at Appvion | Data Center Security
Appvion, a manufacturer of specialty papers, tested R80 security management during development and now uses it every day to gain efficiency, high visibility and concurrent management capabilities.
Cмотреть видео
Cмотреть видео
Check Point: R80 Enhances Efficiency at the University of Kansas
The University of Kansas tested R80 security management and liked what they saw. Today they enjoy increased operational efficiency through concurrent administration capabilities, APIs for automation and a single pane of glass.
Cмотреть видео
Cмотреть видео
Check Point: Tutorial: Configuring Application Control
How to use R80 SmartConsole to get started with the Application Control, URL Filtering Software Blades, and URL Filtering Settings with R80 Security Management. For more information: Infinity, the first consolidated security across net...
Cмотреть видео
Cмотреть видео
Check Point: From HummingBad to Worse: Android Malware Campaign | SandBlast Mobile Security
For five months, mobile threat researchers had unprecedented access to the inner-workings of Yingmob, the Chinese cyber criminals behind HummingBad, a malware that establishes a persistent rootkit on Android devices, generates fraudulent a...
Cмотреть видео
Cмотреть видео
Check Point: Tutorial: Configuring IPS Settings with R80 Security Management Server | Advanced Threa
How to use R80 SmartConsole to configure the settings for the IPS Software Blade. For more information visit:
Cмотреть видео
Cмотреть видео
Check Point: Entrevista a Juan Rivera, en el noticiero Buenos Dias Per̼
Juan Rivera, Gerente Regional de Cono Sur
Cмотреть видео
Cмотреть видео
Check Point: Entrevista a Francisco Robayo, sobre los delitos en la red Teleamazonas Ecuador
Francisco Robayo, Gerente IngenierÌ_a,
Cмотреть видео
Cмотреть видео
Check Point: Jorge Steinfeld, Software; Entrevista en RPP TV
Software Technologies Ltd. — крупнейший в мире поставщик в области безопасности. Компания предлагает покупателям ведущие в индустрии решения и защищает покупателей от кибератак с непревзойденным уровнем успешного обнаружения вре...
Cмотреть видео
Cмотреть видео
Check Point: Presentan lo ̼ltimo en seguridad informatica, Cloud Computing y VirtualizaciÌ_n
Software Technologies Ltd. — крупнейший в мире поставщик в области безопасности. Компания предлагает покупателям ведущие в индустрии решения и защищает покупателей от кибератак с непревзойденным уровнем успешного обнаружения вре...
Cмотреть видео
Cмотреть видео
Check Point: Juan Rivera, habla sobre seguridad en redes sociales
Juan Rivera, Gerente Regional de Cono Sur
Cмотреть видео
Cмотреть видео
Check Point: Vicente Amozurrutia Director MÌ©xico de en TV Azteca Noticias
Software Technologies Ltd. — крупнейший в мире поставщик в области безопасности. Компания предлагает покупателям ведущие в индустрии решения и защищает покупателей от кибератак с непревзойденным уровнем успешного обнаружения вре...
Cмотреть видео
Cмотреть видео
Check Point: Mal uso de las redes sociales Programa DÌ_a a DÌ_a Teleamazonas, Ecuador
Software Technologies Ltd. — крупнейший в мире поставщик в области безопасности. Компания предлагает покупателям ведущие в индустрии решения и защищает покупателей от кибератак с непревзойденным уровнем успешного обнаружения вре...
Cмотреть видео
Cмотреть видео
Check Point: Guerra cibernÌ©tica, nuestro paÌ_s es vulnerable a ataques en la red
Juan Rivera, Gerente Regional de Cono Sur
Cмотреть видео
Cмотреть видео
Check Point: Hunze en Aa Water Resource Board enhances Network Security, SCADA Systems with SandBlas
For more information: To help ensure safe operation of its pumping stations and other key systems, the Hunze en Aa Water Resource Board implemented NGTX appliances with SandBlast zero-day protection. Through the solutions centralized mana...
Cмотреть видео
Cмотреть видео
Check Point: 700 Appliance Setup | SMB Cyber Security
For more information: Watch our tutorial on how to setup our 700 Appliance, 's latest addition to the product family to protect small businesses against the latest cyber threats.
Cмотреть видео
Cмотреть видео