itbion.ru / Видео / New video (ENG)
Check Point: R80.10 Policy Revision
R80.10 Policy revision explained. Learn how to work with policy revision in R80.10. For more information: R80.10 features the most advanced threat prevention across networks and cloud, managed by a single security management console. Secu...
Cмотреть видео
Cмотреть видео
Check Point: Anti-Ransomware: Solution Brief & Demo | Tech Bytes
Anti-Ransomware protects against sophisticated zero-day ransomware. It is included in SandBlast Agent. More information: Protect endpoints from sophisticated attacks and zero-day threats, enabling a deep understanding of security events f...
Cмотреть видео
Cмотреть видео
Check Point: Helvetia Insurance : vSEC for NSXの導入事例
スイスで3番目に大きな保険会社Helvetia InsuranceのvSEC for NSXの導入事例です。保険とは信頼の上に成り立つビジネスなので、お客様の満足度は特に重要であり、セキュリティ対策に求めらるレベルも非常に高いです。ハイレベルなニーズに応えたのがチェック・ポイントのvSEC for NSXでした。 For more information:
Cмотреть видео
Cмотреть видео
Check Point: Gil Shwed & Marius Nacht Interview - Milan 2017
Gil Shwed & Marius Nacht discuss product innovation and the Experience over the years. For more information:
Cмотреть видео
Cмотреть видео
Check Point: Welcome to the Future of Cyber Security | Infinity
The future of cyber security is here. Learn and stay protected against today's cyber threat landscape. For more information: We are all living in a connected world which is affecting every aspect of our lives. In the past couple of ye...
Cмотреть видео
Cмотреть видео
Check Point: Infinity | The Cyber Security Architecture of the Future
Gabi Reish - VP, Product Management and Product Marketing, Software For more information on the Cyber Security Architecture of the Future, please go to:
Cмотреть видео
Cмотреть видео
Check Point: Hacking the Smartphone | Mobile Cyber Hack Demonstration
Live demonstration of a smartphone hack, from Experience 2017. For more information visit: Watch Michael Shaulov, Head of Mobility Products at Software hack a smart phone in real time. Today every business is a mobile business, with req...
Cмотреть видео
Cмотреть видео
Check Point: Cloud Security: Safe Journey to the Cloud
The era of cloud is upon us; firms of all sizes and in all walks of life are looking to leverage the agility and elasticity of cloud. For more information visit: But cloud carries a totally new and unique set of security challenges. In th...
Cмотреть видео
Cмотреть видео
Check Point: R80.10 SmartConsole Security Policies View | Threat Prevention
This video is an overview that describes important features and functionality of the R80.10 SmartConsole and focuses on: Unified Access and Threat Prevention Policies Example of inline layers for zone-based policy Using multiple blades in o...
Cмотреть видео
Cмотреть видео
Check Point: Start Building Your Unified Policy with R80.10 | Security Management | Tech Bytes
R80.10 policy management is unified so you can create and monitor these policies harmoniously. One single policy manages your users, devices, applications, data and networks. With this unified policy, you also get unparalleled granular cont...
Cмотреть видео
Cмотреть видео
Check Point: Simple Security Is Your Best Bet
Patrick Woods, CISO, Missouri State Highway Patrol This thought-provoking session will challenge current models in cyber security management and architecture that suggest that complex problems demand complex solutions. Instead, it is a sim...
Cмотреть видео
Cмотреть видео
Check Point: Evolving Role of the CISO - A Customer Story
In this session, CISO Joey Smith will discuss his understanding of the importance of compliance and security and their differences. For more information: Additionally, he will review what he has personally learned from his experience as...
Cмотреть видео
Cмотреть видео
Check Point: Top 5 Cloud Security Tips (How to Protect Your Data in the Cloud)
The era of cloud is upon us; firms of all sizes and in all walks of life are looking to leverage the agility and elasticity of cloud. But cloud carries a totally new and unique set of security challenges. In this informative and entertainin...
Cмотреть видео
Cмотреть видео
Check Point: Shedding Light on the Dark Web
Avi Rembaum + Neatsun Ziv The dark web is quickly evolving into a marketplace of information and tools that the hackers and adversaries use to breach company networks. The question we face as an industry is how to leverage an awareness of ...
Cмотреть видео
Cмотреть видео
Check Point: Cyber Security in the Era of Exponential Technology
Amnon Bar-Lev - President, Software We are in an extraordinary time in human history. Thanks to innovative and disruptive technologies we live longer, healthier and more educated than ever before. While technologies such as cloud computin...
Cмотреть видео
Cмотреть видео
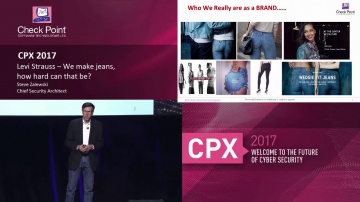
Check Point: We Make Jeans; How Hard Can That Be?
This talk will present some of the business challenges, experiences and road maps from a security perspective to protect the global Levi Brand. Steve Zalewski, Chief Security Architect, Levi Strauss For more information:
Cмотреть видео
Cмотреть видео
Check Point: Moving to the Public Cloud, Securely - FireChat with AWS & Azure
More than 70% of the organizations are committed to a cloud strategy in 2017. Businesses are moving their applications to the Cloud to gain more agility and efficencies. At the same time, Cloud security remains their top concern. Customers...
Cмотреть видео
Cмотреть видео
Check Point: What To Do When It Happens to You - Incident Response
Based on real world experiences of helping customers, this candid discussion will focus on ensuring that your organization is prepared when a breach occurs in your network. The discussion will provide real world examples of what works and w...
Cмотреть видео
Cмотреть видео
Check Point: Preventing the Ransomware Plague | Ransomware Protection
Ransomware reached epidemic proportions in 2016. Organizations of all sizes and sectors fell victim to malware that locked down, encrypted – and in some cases threatened to destroy – critical systems and data. How would you avoid becoming t...
Cмотреть видео
Cмотреть видео
Check Point: Choosing The Right Security Architecture | Cyber Security | Network Security
Moti Sagey - Head of Strategic Marketing & Intelligence, Software When it comes to choosing the right security architecture & security vendor, what does it take to win your trust? In this session Moti Sagey will cover three key pillars th...
Cмотреть видео
Cмотреть видео
Check Point: Anti-Ransomware vs WannaCry | Ransomware Protection Demonstration
WannaCry ransomware hits more than 75,000 organizations in over 99 countries and is quickly spreading. Here's how you can prevent ransomware attacks against your organization with SandBlast Agent, Anti-Ransomware. For more information on h...
Cмотреть видео
Cмотреть видео
Check Point: R80.10 Security Management | Tech Bytes: Gateways, Logs, and Manage & Settings
This video is an overview that describes important features and functionality of the R80.10 SmartConsole. More information: To learn more about R80.10 Security Management: Infinity is the only fully consolidated cyber security architec...
Cмотреть видео
Cмотреть видео
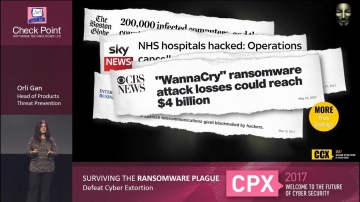
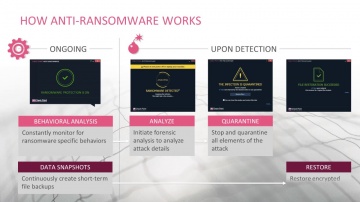
Check Point: Introducing Anti-Ransomware: Defeat Cyber Extortion
Did you know ransomware hit 1 in 3 businesses during 2016? Today more than ever you need a new way to effectively prevent ransomware from impacting your organization. Watch our webinar replay to learn how you can automatically detect, block...
Cмотреть видео
Cмотреть видео
Check Point: Advanced Cyber Security for 2018 | Infinity
Learn more at Introducing Infinity, the world’s most advanced cyber security and management architecture. Infinity consolidates security across network, cloud and mobile, keeping you secured from known and unknown threats, today and in ...
Cмотреть видео
Cмотреть видео
Check Point: and Tufin: Security Management for the Future | Enterprise Network Security
and Tufin provide complete, simplified and automated security management for the enterprise network of the future. For more information: Together, the Tufin Orchestration Suite with Firewalls and Security Management products provide ad...
Cмотреть видео
Cмотреть видео
Check Point: and Savvius Partnership
and Savvius’ joint solution captures mission-critical security alerts and investigates any abnormalities in your network. For more information:
Cмотреть видео
Cмотреть видео
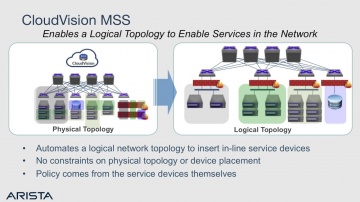
Check Point: & Arista: The Journey to Secure Cloud Networking
Learn from our experts about how and Arista’s Macro-Segmentation Service (MSS) protects the modern data center. For more information: With and Arista CloudVision MSS, ’s data center firewalls can be attached anywhere in the network on ...
Cмотреть видео
Cмотреть видео
Check Point: Technical Assistance Center | Network Security Support
's team of vigilant security experts are here to help our customers. Well trained engineers are available to assist you 24/7 via web service request, live chat, or by phone. For more information:
Cмотреть видео
Cмотреть видео
Check Point: Optimizes Security with Gigamon’s Full Network Visibility
and Gigamon’s joint solution provides comprehensive network visibility, optimal performance and advanced threat prevention capabilities. For more information:
Cмотреть видео
Cмотреть видео
Check Point: 2017 Mobile Security Media Tour
Our Michael Shaulov, Head of Product, Mobile Security discusses the importance of mobile security and common vulnerabilities and threats mobile data of individuals and the enterprise. For more information:
Cмотреть видео
Cмотреть видео