Поиск по тегу «firewall» в разделе Видеокаталог
HD 00:06:01
Check Point: Advanced Cyber Security for 2018 - Cyber Security Demo
This video is a technical demonstration of what the cyber security architecture of the future is all about. For more information visit: Infinity is the first consolidated cyber security across networks, cloud and mobile. Unlike other so...
Cмотреть видео
Cмотреть видео
HD 00:26:55
Айдеко: Релиз Ideco ICS 7.3: что нового в версии
Запись нашего вебинара, посвященного выходу новой версии шлюза безопасности Ideco ICS 7.3. В новой версии существенно улучшена работа Ideco ICS в режиме прямых подключений к прокси-серверу: решена проблема с трафиком клиент-банков и другого...
Cмотреть видео
Cмотреть видео
HD 00:26:45
Check Point: Step-By-Step Guide for Securing a Web Server on Azure using CloudGuard IaaS (prev. vSE
Learn to create and deploy a web server on top of Azure public cloud and to securely publish it through a vSEC standalone server. More information:
Cмотреть видео
Cмотреть видео
HD 00:26:53
Айдеко: Релиз Ideco ICS 7.1: что нового в версии
Данное большое обновление уверенно продолжает развитие Ideco ICS, как комплексного UTM-решения, обеспечивающего многовекторную защиту от интернет-угроз, а также предоставляющего администратору все возможности для контроля сетевого периметра...
Cмотреть видео
Cмотреть видео
HD 00:04:12
Check Point: SandBlast Agent Protects From Advanced Zero-day Malware
What happens if employees roam outside enterprise network that protect them from advanced zero-day invasions? For more information: SandBlast Agent protects the enterprise end-points from advanced zero-day malware, by using advanced C-P-U...
Cмотреть видео
Cмотреть видео
HD 00:03:15
Check Point: Installing SandBlast Agent on the Enterprise Endpoint
This video provides an overview of recommended process for deployment of SandBlast Agent on the Enterprise Endpoints. SandBlast Agent defends endpoints with a complete set of real-time advanced endpoint protection technologies, including T...
Cмотреть видео
Cмотреть видео
HD 01:02:17
Айдеко: Ideco ICS: сравнение с конкурентами и миграция с устаревших решений
На вебинаре мы расскажем о преимуществах Ideco ICS по сравнению с конкурирующими решениями: Microsoft TMG, Kerio Control, Traffic Inspector, Интернет Контроль Сервер, Usergate Proxy&Firewall и др. А также расскажем о возможностях по миграци...
Cмотреть видео
Cмотреть видео
HD 00:47:26
Айдеко: Ideco SMB: новая редакция
Вебинар посвященный бесплатной редакции шлюза безопасности Ideco ICS. https://smb.ideco.ru/ - страница посвященная редакции. https://ideco.ru/obtain - скачать Ideco ICS. http://doc.ideco.ru/ - документация по Ideco ICS.
Cмотреть видео
Cмотреть видео
HD 00:04:00
Check Point: SandBlast Mobile: Quick Start Guide | Tech Bytes
This video is meant to show how easily you can get started protecting your Enterprise's Android and iOS Devices with SandBlast Mobile. More information: Topics covered: Ch1 - Activating Your Admin Account Ch2 - Logging into Your SandBlast...
Cмотреть видео
Cмотреть видео
HD 00:04:45
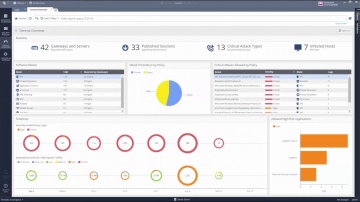
Check Point: R80.10 Policy Revision
R80.10 Policy revision explained. Learn how to work with policy revision in R80.10. For more information: R80.10 features the most advanced threat prevention across networks and cloud, managed by a single security management console. Secu...
Cмотреть видео
Cмотреть видео
HD 00:18:47
Check Point: Gil Shwed & Marius Nacht Interview - Milan 2017
Gil Shwed & Marius Nacht discuss product innovation and the Experience over the years. For more information:
Cмотреть видео
Cмотреть видео
HD 00:24:49
Check Point: Welcome to the Future of Cyber Security | Infinity
The future of cyber security is here. Learn and stay protected against today's cyber threat landscape. For more information: We are all living in a connected world which is affecting every aspect of our lives. In the past couple of ye...
Cмотреть видео
Cмотреть видео
HD 00:26:30
Check Point: Infinity | The Cyber Security Architecture of the Future
Gabi Reish - VP, Product Management and Product Marketing, Software For more information on the Cyber Security Architecture of the Future, please go to:
Cмотреть видео
Cмотреть видео
HD 00:18:41
Check Point: Cloud Security: Safe Journey to the Cloud
The era of cloud is upon us; firms of all sizes and in all walks of life are looking to leverage the agility and elasticity of cloud. For more information visit: But cloud carries a totally new and unique set of security challenges. In th...
Cмотреть видео
Cмотреть видео
HD 00:04:32
Check Point: R80.10 Security Management | Tech Bytes: Gateways, Logs, and Manage & Settings
This video is an overview that describes important features and functionality of the R80.10 SmartConsole. More information: To learn more about R80.10 Security Management: Infinity is the only fully consolidated cyber security architec...
Cмотреть видео
Cмотреть видео
HD 00:01:25
Check Point: Advanced Cyber Security for 2018 | Infinity
Learn more at Introducing Infinity, the world’s most advanced cyber security and management architecture. Infinity consolidates security across network, cloud and mobile, keeping you secured from known and unknown threats, today and in ...
Cмотреть видео
Cмотреть видео
HD 01:03:18
Check Point: and Tufin: Security Management for the Future | Enterprise Network Security
and Tufin provide complete, simplified and automated security management for the enterprise network of the future. For more information: Together, the Tufin Orchestration Suite with Firewalls and Security Management products provide ad...
Cмотреть видео
Cмотреть видео
HD 00:02:43
Check Point: and Savvius Partnership
and Savvius’ joint solution captures mission-critical security alerts and investigates any abnormalities in your network. For more information:
Cмотреть видео
Cмотреть видео
HD 00:43:39
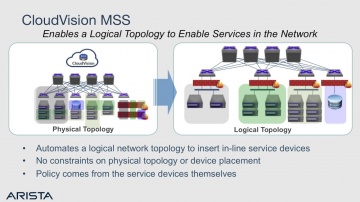
Check Point: & Arista: The Journey to Secure Cloud Networking
Learn from our experts about how and Arista’s Macro-Segmentation Service (MSS) protects the modern data center. For more information: With and Arista CloudVision MSS, ’s data center firewalls can be attached anywhere in the network on ...
Cмотреть видео
Cмотреть видео
HD 00:02:24
Check Point: Technical Assistance Center | Network Security Support
's team of vigilant security experts are here to help our customers. Well trained engineers are available to assist you 24/7 via web service request, live chat, or by phone. For more information:
Cмотреть видео
Cмотреть видео
HD 00:04:49
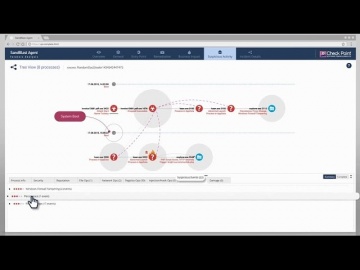
Check Point: SandBlast Agent Forensics
This video shows SandBlast Agent’s automated forensics analysis in action. For more information: It demonstrates SandBlast Agent’s power to instantly provide security teams with a crystal-clear understanding of cyber attacks, empowering t...
Cмотреть видео
Cмотреть видео
HD 00:02:12
Check Point: Anatomy of a Smishing Attack: Czech Posta App
A new smishing attack targeted users in the Czech Republic was discovered January 26, 2017. Smishing, or SMS phishing, is a vector attackers use to send SMS messages from supposedly legitimate organizations. These messages persuade users t...
Cмотреть видео
Cмотреть видео
HD 00:03:03
Check Point: Koch Media Crushes Advanced Attacks with SandBlast | Advanced Threat Prevention
Koch Media develops games globally, which is a process fraught with peril to the intellectual property in their games. Koch sought to replace Cisco and decided on SandBlast Zero DayProtection to crush advanced attacks. For more informat...
Cмотреть видео
Cмотреть видео
HD 00:02:07
Check Point: R80 Enhances Efficiency at the University of Kansas
The University of Kansas tested R80 security management and liked what they saw. Today they enjoy increased operational efficiency through concurrent administration capabilities, APIs for automation and a single pane of glass.
Cмотреть видео
Cмотреть видео
HD 00:02:11
Check Point: R80 Streamlines Security Management at Appvion | Data Center Security
Appvion, a manufacturer of specialty papers, tested R80 security management during development and now uses it every day to gain efficiency, high visibility and concurrent management capabilities.
Cмотреть видео
Cмотреть видео
HD 00:03:30
Check Point: Tutorial: Configuring IPS Settings with R80 Security Management Server | Advanced Threa
How to use R80 SmartConsole to configure the settings for the IPS Software Blade. For more information visit:
Cмотреть видео
Cмотреть видео
HD 00:01:58
Check Point: Hunze en Aa Water Resource Board enhances Network Security, SCADA Systems with SandBlas
For more information: To help ensure safe operation of its pumping stations and other key systems, the Hunze en Aa Water Resource Board implemented NGTX appliances with SandBlast zero-day protection. Through the solutions centralized mana...
Cмотреть видео
Cмотреть видео
HD 00:00:49
Check Point: RSA 2016: Receives "Recommended" Rating in NSS Next Generation Firewall Test
More Information: NSS Labs, Inc. released their results for the 2016 Generation Firewall Test. In their independent assessment of the security effectiveness and value, NSS once again recognized with the "Recommended" rating. This marks t...
Cмотреть видео
Cмотреть видео
HD 00:05:44
Check Point: Security Demo for Industrial Control Systems
This video demonstrates how is deployed to protect and secure your operational network. For more information, please visit: In the centralized management center (called the SmartCenter), rules or security policies are created and pushed ...
Cмотреть видео
Cмотреть видео
HD 00:01:54
Check Point: 700 Series Appliances for Small Business - Product Video | SMB Cyber Security
As a small business, your focus is on building unique products, driving sales, and providing excellent service to your customers. Security is important but it seems like every week there is some new piece of software or equipment to prote...
Cмотреть видео
Cмотреть видео