Check Point Software Technologies, Ltd.

360 роликов
Нет подписчиков
Компания Check Point Software Technologies Ltd. — мировой поставщик решений в области обеспечения интернет-безопасности, единственный поставщик средств обеспечения полной безопасности Total Security для сетей, данных и конечных узлов, объединенных единой средой управления.
Сортировка

00:00:31
Обнаружено блокирование рекламы на сайте
Для существования нашего сайта необходим показ рекламы. Просим отнестись с пониманием и добавить сайт в список исключений вашей программы для блокировки рекламы (AdBlock и другие).
HD Check Point: Without the Best Security, Bad Things Happen
Two chatty security guards get distracted by a shiny coin, and their VIP client is swept away by criminals in a white van. For more information visit Takes real life security scenario, and demonstrates how the standard, traditional methods just don’t do the job any more. Gen V from , the only solution for 5th generation cyber security.
Check Point: Customer & Partner Insights- California DMV
partners with hundreds of companies across the U.S. and internationally to form long-term business and person relationships. To learn more: speaks with customers and partners at RSA Conference 2014 in San Francisco. Watch as they share w...
Cмотреть видео
Cмотреть видео
Check Point: : Introducing Software-defined Protection | Cyber Security Software
To address today’s EVER-CHANGING threat landscape, has introduced a MODULAR and dynamic security architecture that envisions a THREE-LAYER infrastructure that provides operational RESILIENCE and real-time, PROACTIVE protection.
Cмотреть видео
Cмотреть видео
Check Point: SMB Cyber Security - 600 Appliance Setup
Small businesses need cost-effective security that provides robust protections and ease of use. For more information: brings its long-standing history of security expertise to a range of solutions optimized for the unique demands of smal...
Cмотреть видео
Cмотреть видео
Check Point: Software - 20 Years of Innovation
An overview in pictures of key milestones in 's 20 year history
Cмотреть видео
Cмотреть видео
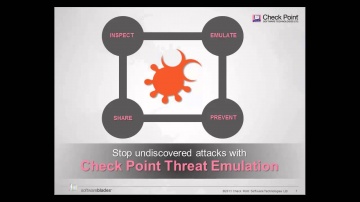
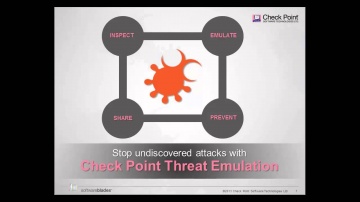
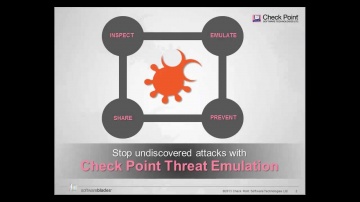
Check Point: Introducing ThreatCloud Emulation Services | Cloud Security
Learn More: Find Zero-Day Threats before they find you with ThreatCloud Emulation Services.
Cмотреть видео
Cмотреть видео
Check Point: Next Generation Firewall, How To Choose The Right One | Network Security
What questions should you ask when choosing the right network security protection in an integrated next generation firewall platform? For more information: provides customers of all sizes with the latest data and network security protect...
Cмотреть видео
Cмотреть видео
Check Point: Customer Success Video: MLB Network Maintains 100 Percent Network Uptime
The MLB Network turns to to help launch the cable network and achieve 100 percent uptime. 's easy, flexible and scalable security solution enables the MLB Network to maintain zero downtime and address the needs of its viewing fans in 70 m...
Cмотреть видео
Cмотреть видео
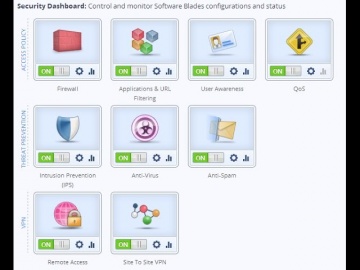
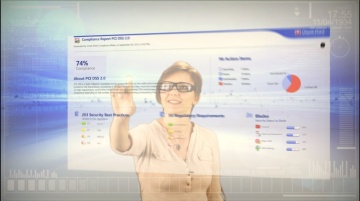
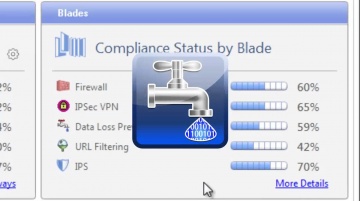
Check Point: Compliance Software Blade - Regulatory Compliance
For more information: This is the third video in the Compliance Software Blade Demonstration Series. See how the Compliance Software Blade can help you easily review your regulatory compliance status, and quickly prepare detailed reports ...
Cмотреть видео
Cмотреть видео
Check Point: Your Second Pair of Eyes - Compliance Software Blade | Network Security
For more information: Keeping a close eye on security and compliance is a challenging task. The Compliance Software Blade can be your second pair of eyes to constantly monitor your security status, save time in preparing audits and compl...
Cмотреть видео
Cмотреть видео
Check Point: - CNN Report a Gil Shwed (sub español)
CNN analiza en este informe la creación de Gil Shwed, , una empresa dedicada a la creación de soluciones en el ámbito de la seguridad informática.
Cмотреть видео
Cмотреть видео
Check Point: Threat Emulation Explained by | Advanced Threat Prevention
's Threat new Threat Emulation Software Blade prevents infections from undiscovered exploits, zero-day and targeted attacks. For more information: 's Threat new Threat Emulation Software Blade prevents infections from undiscovered exploit...
Cмотреть видео
Cмотреть видео
Check Point: Threat Emulation Explained by | Advanced Threat Prevention
's Threat new Threat Emulation Software Blade prevents infections from undiscovered exploits, zero-day and targeted attacks. For more information: 's Threat new Threat Emulation Software Blade prevents infections from undiscovered exploit...
Cмотреть видео
Cмотреть видео
Check Point: Do You Know What's Hiding On Your Network?
This video summarizes the analysis and findings in the 2013 Security Report. For more information: provides organizations of all sizes with the latest data and network security protection in an integrated next generation firewall platfo...
Cмотреть видео
Cмотреть видео
Check Point: Do You Know What's Hiding On Your Network?
This video summarizes the analysis and findings in the 2013 Security Report. For more information: provides organizations of all sizes with the latest data and network security protection in an integrated next generation firewall platfo...
Cмотреть видео
Cмотреть видео
Check Point: Choose the Right Next Generation Firewall - Multi-Layer Security
Why Multi-Layer Security and how 's Software Blade Architecture is the most secure and scalable solution in this market. For more information: provides organizations of all sizes with the latest data and network security protection in a...
Cмотреть видео
Cмотреть видео
Check Point: Choose the Right Next Generation Firewall - Multi-Layer Security
Why Multi-Layer Security and how 's Software Blade Architecture is the most secure and scalable solution in this market. For more information: provides organizations of all sizes with the latest data and network security protection in a...
Cмотреть видео
Cмотреть видео
Check Point: ThreatCloud | Complete Cyber Security Intelligence Infrastructure | Network Security
For more information: Introducing ThreatCloud, the first collaborative network to fight cyber-attacks.
Cмотреть видео
Cмотреть видео
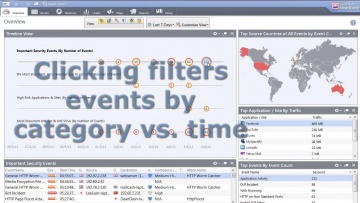
Check Point: SmartEvent | Security Management Walk-Through
Are you tired of managing security by manually searching through millions of logs to find the information you need? There is a better way! Watch this SmartEvent Video to learn how to manage your security more efficiently. For more informa...
Cмотреть видео
Cмотреть видео
Check Point: Q&A: Compliance and Regulations with Jeremy Kaye | Network Security Risk and Compliance
For more information: On June 18, 2013, 's in house #regulations and #compliance expert Jeremy Kaye spoke with Dameon Welch-Abernathy live in our first Google+ Hangouts on Air. This was an opportunity to hear some of the challenges your p...
Cмотреть видео
Cмотреть видео
Check Point: Choosing the Right Next Generation Firewall | NGFW Explained
For more information: What is a Next Generation Firewall, where did the term come from and why is leading this market.
Cмотреть видео
Cмотреть видео
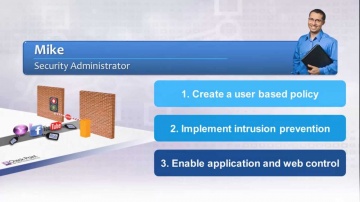
Check Point: A Day in the Life of Mike, a Next Generation Firewall Administrator
For more information: See how security admins can easily create granular policies—based on users or groups—to identify, block or limit usage of over Web 2.0 applications and educate users on safe Internet use with our Next Generation Fire...
Cмотреть видео
Cмотреть видео
Check Point: Compliance Software Blade | Network Security Best Practices
For more information: This is the second video in the Compliance Software Blade Demonstration Series. This video provides insight into aligning both security and compliance to security best practices.
Cмотреть видео
Cмотреть видео
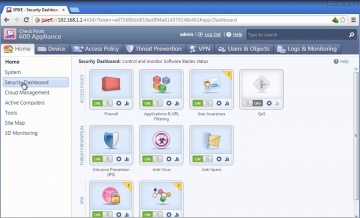
Check Point: 600 Appliance Setup
Watch our tutorial on how to setup our 600 Appliance, 's latest edition to the product family to protect small businesses against the latest cyber threats.
Cмотреть видео
Cмотреть видео
Check Point: CRN Interviews Amnon Bar-Lev | Network Security
Amnon Bar-Lev talks to CRN about how to better target products for sales and that there should be a focus on evaluating existing network security architecture and protecting organizations.
Cмотреть видео
Cмотреть видео
Check Point: Denial of Service Cyber Attack Protector Overview
DDoS Protector™Appliances block Denial of Service attacks within seconds with multi-layered protection and up to 40 Gbps of performance. For more information: Modern DDoS attacks use new techniques to exploit areas where traditional secu...
Cмотреть видео
Cмотреть видео
Check Point: Third Party Security Validation | Threat Prevention
For more information: is excited to have received top awards from respected industry sources and certification bodies for its Next Generation Firewall, IPS and Threat Prevention Appliance products.
Cмотреть видео
Cмотреть видео
Check Point: Compliance Software Blade Demonstration
Introduction and overview to the Compliance Software Blade and its features and functions.For more information: The Compliance Software Blade monitors your management, Software Blades and security gateways to constantly validate that you...
Cмотреть видео
Cмотреть видео
Check Point: 2013 Security Report | Cyber Security
Based on research of nearly 900 companies and 120,000 hours of monitored traffic, the 2013 Security Report reveals major security risks organizations are exposed to on a daily basis. For information: Most importantly, the report provides...
Cмотреть видео
Cмотреть видео
Check Point: DDoS Protector - Technical Overview | DDoS Protection
's new Threat Emulation Software Blade prevents infections from undiscovered exploits, zero-day and targeted attacks. For more information: This innovative solution quickly inspects suspicious files, emulates how they run to discover mali...
Cмотреть видео
Cмотреть видео
Check Point: on National Czech Republic Television
Eurograbber was launched against banking customers, using a sophisticated combination of malware directed at computers and mobile devices. For more information click here: The malware, in conjunction with the attackers' command and contr...
Cмотреть видео
Cмотреть видео