Check Point: SandBlast Agent Forensics → Похожие видео ролики , Страница 9
This video shows SandBlast Agent’s automated forensics analysis in action. For more information: It demonstrates SandBlast Agent’s power to instantly provide security teams with a crystal-clear understanding of cyber attacks, empowering them to focus on effective incident triage and response. Advanced Endpoint | Threat Prevention: Protect endpoints from sophisticated cyber attacks and zero-day threats, enabling a deep understanding of security events for rapid response and quick remediation of attacks. Visit our website for more information about SandBlast Agent’s comprehensive coverage ac...
Подробнее в видео...
Подробнее в видео...
00:06:26
Check Point: Entrevista a Juan Rivera, en el noticiero Buenos Dias Per̼
Juan Rivera, Gerente Regional de Cono Sur
Cмотреть видео
Cмотреть видео
00:05:34
Check Point: Software commente les dernières tendances de la sécurité informatique en 2010
I Télé Les Echos de l'Eco David Darmon, Directeur General France de Software Technologies, lun des leaders mondiaux de la sécurité informatique, explique les tendances de la sécurité informatique en 2010 au vu des récents événements Inter...
Cмотреть видео
Cмотреть видео
HD 00:23:48
Check Point: Ask Me Anything - How to Sell to a CISO
In this fireside chat with Jerry Pitman, CISO, Tenneco , will share what he looks for when meeting with security vendors and also the less effective sales pitches he experienced
Cмотреть видео
Cмотреть видео
HD 00:44:57
Check Point: vSEC for Microsoft Azure Hybrid Cloud : Deployment Scenarios and Demo
Cloud Security Architect provides overview of deployment scenarios, use cases and demos vSEC for Microsoft Azure for Hybrid Cloud.
Cмотреть видео
Cмотреть видео
HD 00:05:29
Check Point: Next Generation Firewall, How To Choose The Right One | Network Security
What questions should you ask when choosing the right network security protection in an integrated next generation firewall platform? For more information: provides customers of all sizes with the latest data and network security protect...
Cмотреть видео
Cмотреть видео
HD 00:05:18
Check Point: Deployment Tools - ISOmorphic & Blink
Deploying Next Generation Firewalls just got easier with the introduction of the Blink utility. For more information: Blink creates a working snapshot of a cleanly installed security gateway with a completed First-Time Configuration Wizard...
Cмотреть видео
Cмотреть видео
HD 00:01:04
Check Point: RSA Conference 2014 - Partner Insights - Avnet
Learn More: Gimv, a leading European private equity and venture capital investment company, leverages ThreatCloud Emulation technology to prevent against zero day attacks. Watch as IT Manager Kristof Poppe discusses his experience wi...
Cмотреть видео
Cмотреть видео
HD 00:02:38
Check Point: Your Second Pair of Eyes - Compliance Software Blade | Network Security
For more information: Keeping a close eye on security and compliance is a challenging task. The Compliance Software Blade can be your second pair of eyes to constantly monitor your security status, save time in preparing audits and compl...
Cмотреть видео
Cмотреть видео
HD 00:02:29
Check Point: Customer Success: Community Newspaper Group (CNG)
For More Information: Community Newspaper Groups seventeen newspapers provide readers with the latest in local news, sports, and entertainment in Perth, Australia. As a publishing outlet, its critical for Community Newspaper Group to kee...
Cмотреть видео
Cмотреть видео
HD 00:03:31
Check Point: Protecting Against Spy Eye Bot | Network Security
For more information: Learn how to protect against Spy Eye bot
Cмотреть видео
Cмотреть видео
HD 00:06:09
Check Point: Introducción a Compliance Blade
Introducción a Compliance Blade a Software
Cмотреть видео
Cмотреть видео
HD 00:00:54
Check Point: 01 Installing the Management Server Hotfix
Install the Hotfix on Gaia R77.30 Security Management Server and R77.20/R77.30 Security Gateways. It is required for both the vSEC Gateway and the vSEC Controller.
Cмотреть видео
Cмотреть видео
HD 00:00:48
Check Point: Customer & Partner Insights- FishNet Security
Learn More: speaks with customers and partners at RSA Conference 2014 in San Francisco. Watch as they share what makes them a fan.
Cмотреть видео
Cмотреть видео
HD 00:03:59
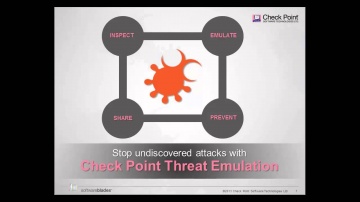
Check Point: Threat Emulation Explained by | Advanced Threat Prevention
's Threat new Threat Emulation Software Blade prevents infections from undiscovered exploits, zero-day and targeted attacks. For more information: 's Threat new Threat Emulation Software Blade prevents infections from undiscovered exploit...
Cмотреть видео
Cмотреть видео
HD 00:03:59
Check Point: Threat Emulation Explained by | Advanced Threat Prevention
's Threat new Threat Emulation Software Blade prevents infections from undiscovered exploits, zero-day and targeted attacks. For more information: 's Threat new Threat Emulation Software Blade prevents infections from undiscovered exploit...
Cмотреть видео
Cмотреть видео
HD 00:05:12
Check Point: Deployment Tools; DIY security appliance images using ISOmorphic
Deployment Tools; DIY security appliance images using ISOmorphic. For more information: In our second video on deployment tools we show you how to image Security Appliances and Open Servers. With the ISOmorphic utility you can inst...
Cмотреть видео
Cмотреть видео
HD 00:22:53
Check Point: Gen V Cyber Security with Moti Sagey - CPX 360
In his keynote, Moti Sagey will discuss in a pragmatic fact based way what it takes to build a Gen V security solution and how the cyber landscape matches the must have for effective security.
Cмотреть видео
Cмотреть видео
HD 00:01:12
Check Point: RSA Conference 2014 - Customer Insights - Securities America, Inc.
Find out more: speaks with customers and partners at RSA Conference 2014 in San Francisco. Watch as Leon Johnson from Securities America, Inc. speaks about the critical need to secure data in the financial industry and how integrates ...
Cмотреть видео
Cмотреть видео
HD 00:15:01
Check Point: Do You Know What's Hiding On Your Network?
This video summarizes the analysis and findings in the 2013 Security Report. For more information: provides organizations of all sizes with the latest data and network security protection in an integrated next generation firewall platfo...
Cмотреть видео
Cмотреть видео
HD 00:15:01
Check Point: Do You Know What's Hiding On Your Network?
This video summarizes the analysis and findings in the 2013 Security Report. For more information: provides organizations of all sizes with the latest data and network security protection in an integrated next generation firewall platfo...
Cмотреть видео
Cмотреть видео
HD 00:02:08
Check Point: Capsule Docs – Keep Your Business Documents Protected | Enterprise | Network Security
Capsule Docs protects your sensitive business documents to ensure they don’t get unintentionally exposed. See how Capsule Docs works to provide document security.
Cмотреть видео
Cмотреть видео
HD 00:01:43
Check Point: Malware Threat Prevention | Zero-Day, Zero-Second.
What can malware do in 60 seconds? One minute can change everything for a business. So what happens when the speed of business is overtaken by the speed of malware? The team devised a test to quantify that exact question. Learn More: As ...
Cмотреть видео
Cмотреть видео
HD 00:01:34
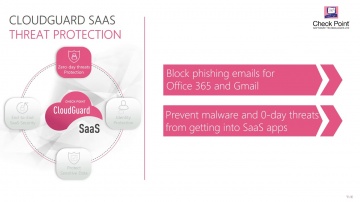
Check Point: Zero-day Threat Protection for SaaS Email | CloudGuard SaaS Demo
Demo showing how CloudGuard Saas provides advanced security and threat prevention for SaaS applications. For more information: Watch this short demonstration video to learn how CloudGuard SaaS, an industry-first software-as-a-service (Saa...
Cмотреть видео
Cмотреть видео
HD 00:03:11
Check Point: Choose the Right Next Generation Firewall - Multi-Layer Security
Why Multi-Layer Security and how 's Software Blade Architecture is the most secure and scalable solution in this market. For more information: provides organizations of all sizes with the latest data and network security protection in a...
Cмотреть видео
Cмотреть видео
HD 00:00:37
Check Point: 03 Adding the vCenter IP Address to the Runtime Settings
VMware requires you to add the vCenter IP address to the Runtime Settings tab on the vCenter Server Setting page
Cмотреть видео
Cмотреть видео
HD 00:01:17
Check Point: RSA Conference 2014 - Customer Insights - Leidos
Find out more: speaks with customers and partners at RSA Conference 2014 in San Francisco. Watch as Joseph Royal of Leidos shares what makes him a fan.
Cмотреть видео
Cмотреть видео
HD 00:02:44
Check Point: Protected 24x7 With | Cyber Security
For more information visit:
Cмотреть видео
Cмотреть видео
HD 00:03:11
Check Point: Choose the Right Next Generation Firewall - Multi-Layer Security
Why Multi-Layer Security and how 's Software Blade Architecture is the most secure and scalable solution in this market. For more information: provides organizations of all sizes with the latest data and network security protection in a...
Cмотреть видео
Cмотреть видео
HD 00:01:24
Check Point: Capsule Docs - Secure Business Documents Everywhere | Network Security
Capsule Docs ensures that only authorized individuals can access your business documents. Confidently share documents with coworkers, business partners, clients, and vendors, because you are in control of their access and sharing rights.
Cмотреть видео
Cмотреть видео