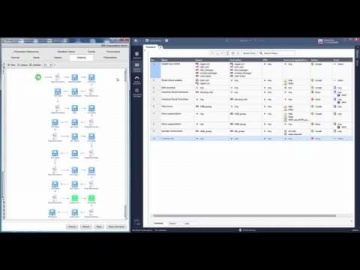
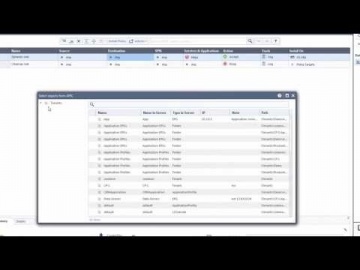
PLM: ЛОЦМАН:PLM Управление архивом - видео → Похожие видео ролики , Страница 60
Вся разработанная на предприятии документация подлежит учету и хранению, которыми занимаются специалисты службы архива или бюро технической документации. На вебинаре демонстрируется как автоматизировать эти процессы в системе ЛОЦМАН:PLM с помощью прикладного модуля. Модуль ЛОЦМАН:PLM Архив позволяет вести электронную картотеку документов и абонентов, обеспечивает быстрый доступ к документам с учетом назначенных прав пользователя, а также предоставляет возможность обмена документацией с другими предприятиями. В программе: 0:00 - Вводная часть 3:40 - Основные возможности и новинк...
Подробнее в видео...
Подробнее в видео...
HD 00:02:07
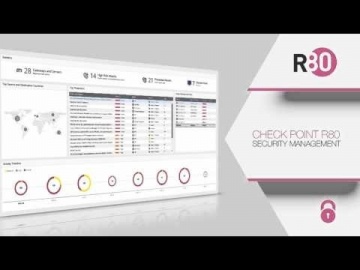
Check Point: R80 Enhances Efficiency at the University of Kansas
The University of Kansas tested R80 security management and liked what they saw. Today they enjoy increased operational efficiency through concurrent administration capabilities, APIs for automation and a single pane of glass.
Cмотреть видео
Cмотреть видео
HD 00:04:02
Check Point: SideStepper: Anatomy of an iOS Vulnerability | Mobile Threat Prevention
For more information, visit: Report: IDC Technology Spotlight: Why Comprehensive Security Requires Mobile Threat Prevention: disclosed details about SideStepper, a vulnerability that can be used to install malicious enterprise apps o...
Cмотреть видео
Cмотреть видео
HD 00:01:48
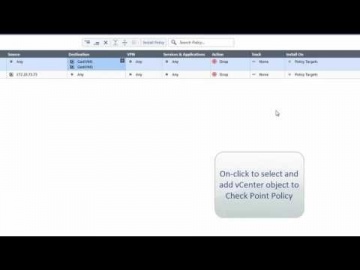
Check Point: vSEC controller Demo with R80 Smart Management | Cloud Security
This video demos the vSEC cloud security integration with VMware vCenter and NSX. It shows you how to integrate a vCenter server in the Smart Console, provision a security rule based on imported vCenter objects like VM name, integrate wit...
Cмотреть видео
Cмотреть видео
HD 00:02:11
Check Point: R80 Streamlines Security Management at Appvion | Data Center Security
Appvion, a manufacturer of specialty papers, tested R80 security management during development and now uses it every day to gain efficiency, high visibility and concurrent management capabilities.
Cмотреть видео
Cмотреть видео
HD 00:20:33
Check Point: We Make Jeans; How Hard Can That Be?
This talk will present some of the business challenges, experiences and road maps from a security perspective to protect the global Levi Brand. Steve Zalewski, Chief Security Architect, Levi Strauss For more information:
Cмотреть видео
Cмотреть видео
HD 00:01:15
Check Point: ââÑââÛâ»Ù¨â_Ä_ÄÝÎ_Ñ£ÐâäâÎÙâä
¾÷¬È_¨âµâ_ÄÄ__ø_»¨¾äÜ£ø_ª_ªá¤_ªÇ»â_Ûâ_Ä_Ä_ÄöÄ¥â©Ä_âãâÀÄÐÄÂÄÄÄöÜâ侩Ùø ¾ÄÉʱâÕã¬ââ¡Á÷ÇÝÑÀà¼Ñ_ªÛââµâ_ÄÄ__ø_»ÛÉøâ»Ä_ÄÂÄ_Ä â£Ä_â¡ÄÈâáâ_Ä ÄÊÛÄÄÄ...
Cмотреть видео
Cмотреть видео
HD 00:18:01
Check Point: How to Hack a Smartphone - Demo with Pablo Perez CPX 360
Ever wanted to know how to hack a smartphone? Join this exciting live demo to see first-hand how easy it is. For more information visit In this session, Michael Shaulov will demonstrate a live hacking of a smartphone. After the demonstrat...
Cмотреть видео
Cмотреть видео
00:21:22
Check Point: Vicente Amozurrutia Director MÌ©xico de en TV Azteca Noticias
Software Technologies Ltd. — крупнейший в мире поставщик в области безопасности. Компания предлагает покупателям ведущие в индустрии решения и защищает покупателей от кибератак с непревзойденным уровнем успешного обнаружения вре...
Cмотреть видео
Cмотреть видео
00:13:17
Check Point: Sky News Interview with Kurt Hansen
Software Technologies Ltd. — крупнейший в мире поставщик в области безопасности. Компания предлагает покупателям ведущие в индустрии решения и защищает покупателей от кибератак с непревзойденным уровнем успешного обнаружения вре...
Cмотреть видео
Cмотреть видео
HD 00:02:35
Check Point: SandBlast Agent Backs Up Anti-Virus by Preventing Recently Discovered Malware | Tech By
What happens if your anti-virus signature database is not updated with a very recently discovered malware? SandBlast Agent defends endpoints with a complete set of real-time advanced endpoint protection technologies, by using the up-to-date...
Cмотреть видео
Cмотреть видео
00:02:07
Check Point: 3D Security
TheStreet.com Gil Shwed, CEO of Software, talks with James Rogers of
Cмотреть видео
Cмотреть видео
HD 00:02:50
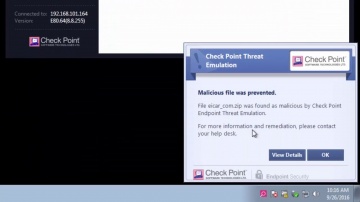
Check Point: Threat Emulation Protects Investment Firm: Gimv
Learn More: Gimv, a leading European private equity and venture capital investment company, leverages ThreatCloud Emulation technology to prevent against zero day attacks. Watch as IT Manager Kristof Poppe discusses his experience wi...
Cмотреть видео
Cмотреть видео
HD 00:00:39
Check Point: Automation with VMware vCenter Orchestrator and R80 Smart Management
Use VMware vCenter Orchestrator to provision security policies in Ûªs R80 Smart Management Console leveraging the open API interface. This video demos automated security policy provisioning. Rules that are provisioned include Stealth rul...
Cмотреть видео
Cмотреть видео
HD 00:01:32
Check Point: SandBlast Mobile Security: Man-in-the-Middle Mobile Attacks
Our mobile devices are more vulnerable then we think. A man-in-the middle attack is a potential threat every time you connect to a Wi-Fi network. For more information: Imagine you are at a coffee shop and you want to connect to Wi-Fi and...
Cмотреть видео
Cмотреть видео
HD 00:02:09
Check Point: SmartConsole Integration with Cisco ACI | Private Cloud Networks
vSEC for Cisco ACI securely enables the rapid deployment of applications in private cloud networks. The integration with CiscoÛªs APIC Controller lowers the time it takes to create and update security policies from minutes to seconds, allo...
Cмотреть видео
Cмотреть видео
HD 00:02:47
Check Point: ã»âÎÙÄ_Ä_â±Ä â£Ä_â¡ÄÈÄÁÄÄâÈÄ_âü¬»à_¤¼ÄÔ_¨¥ã¬ø
2016_«3¾ÏöÛÄÔÄ_â¢ÄÇÄöÄÄÄÄöÄøÄ_âøâ_øCEOÇâöâÜÄÑÄ_Ä¢Ä_âáĤÄ_Ü¥ÓÈâÕÉÂÐÜÑ_ÑÙÛâÒÁâä¨Ü¥ÓȤøÛÄÔÄ_â¢ÄÇÄö__¨üÈ_µÇø_Ñ_ÇЪ_Ûã_ܨÄâ_Ä_ÄöÇ_ã_...
Cмотреть видео
Cмотреть видео
HD 00:18:22
Check Point: Simple Security Is Your Best Bet
Patrick Woods, CISO, Missouri State Highway Patrol This thought-provoking session will challenge current models in cyber security management and architecture that suggest that complex problems demand complex solutions. Instead, it is a sim...
Cмотреть видео
Cмотреть видео
HD 00:02:46
Check Point: Denham Capital Enjoys Agility and Security in the vSEC Protected Microsoft Azure Cloud
More information: A leading private equity firm with great success in the often unpredictable energy industry, Denham Capital needed to move to the cloud for increased agility without compromising security. With Microsoft Azure and vSEC ...
Cмотреть видео
Cмотреть видео
HD 00:22:56
Check Point: Internet of Things: The Dangers of IoT - CPX 360 2018
The concept of Internet of Things (IoT) truly represents a radical shift in how companies will operate, governments will govern and individuals will live their lives. Micro compute technologies and autonomous systems will permeate our day-t...
Cмотреть видео
Cмотреть видео
HD 00:04:19
Check Point: SMB Cyber Security - 600 Appliance Setup
Small businesses need cost-effective security that provides robust protections and ease of use. For more information: brings its long-standing history of security expertise to a range of solutions optimized for the unique demands of smal...
Cмотреть видео
Cмотреть видео
00:02:36
Check Point: Global TV Interviews Kellman Meghu
Software Technologies Ltd. — крупнейший в мире поставщик в области безопасности. Компания предлагает покупателям ведущие в индустрии решения и защищает покупателей от кибератак с непревзойденным уровнем успешного обнаружения вре...
Cмотреть видео
Cмотреть видео
00:46:00
Check Point: Tackling a Complex Threat Landscape with Software-defined Protection
Description: In this 30-minute webinar we'll examine software-defined protection (SDP). This new architecture addresses today's security challenges by providing operational resilience and real-time, proactive protection. You'll learn: • ...
Cмотреть видео
Cмотреть видео
00:08:04
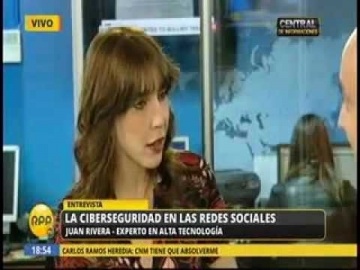
Check Point: Juan Rivera, habla sobre seguridad en redes sociales
Juan Rivera, Gerente Regional de Cono Sur
Cмотреть видео
Cмотреть видео
00:03:02
Check Point: Cyber Security Plays Offense | Cyber Security
For more information: Gil Shwed, CEO of talks to James Rogers of TheStreet.com
Cмотреть видео
Cмотреть видео
HD 00:03:59
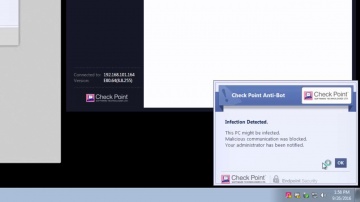
Check Point: SandBlast Agent Anti-Bot Protects the Endpoint from Bot Invasions | Tech Bytes
What happens if employees roam outside enterprise network that protect them from Bot invasions? SandBlast Agent protects the enterprise endpoints from Bot threats, by detecting the communication with command-and-control server. Its Anti-Bot...
Cмотреть видео
Cмотреть видео
HD 00:01:25
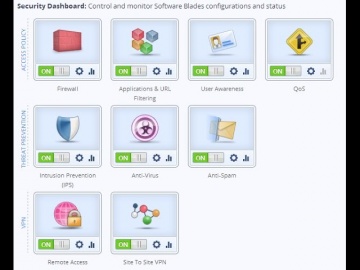
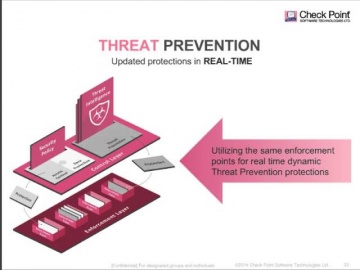
Check Point: R80 Security Management | Advanced Threat Prevention
's R80 Security Management helps you consolidate security functions so you can be more efficient and effective at deploying the strongest protections across your organization. More Information:
Cмотреть видео
Cмотреть видео
HD 00:02:24
Check Point: Partner Success Story - RoundTower on vSEC Solution | Cloud Security
For More Information: ... Partner Round Tower shares a vSEC success story highlighting the features and benefits of vSEC for VMware NSX advanced security for the Software-Defined Data Center. vSEC integration with VMware NSX delivers dyn...
Cмотреть видео
Cмотреть видео
HD 00:01:54
Check Point: 600 Security Appliance: One Box, Complete Protection | SMB Cyber Security
Learn more about the 600 appliance: The 600 provides a complete security package with firewall, VPN, antivirus, intrusion prevention and more, at a price your small business can afford.
Cмотреть видео
Cмотреть видео
HD 00:02:17
Check Point: Big Bad Mobile Threats of 2015 - Mobile Threat Prevention
The mobile threat landscape changed dramatically in 2015. Simple hacks and rudimentary malware was quickly replaced by sophisticated cyber thieves who know exactly what sensitive data they can take from you and how. Along with the growing s...
Cмотреть видео
Cмотреть видео