Поиск по тегу «check point software» в разделе Видеокаталог
HD 01:01:35
Check Point: EU GDPR Webinar Replay
The European Union’s General Data Protection Regulation (‘GDPR’) poses the biggest change to the regulatory landscape of data privacy. To learn more visit: GDPR places significant policy and technical responsibilities on ANY organization ...
Cмотреть видео
Cмотреть видео
HD 00:00:31
Check Point: Without the Best Security, Bad Things Happen
Two chatty security guards get distracted by a shiny coin, and their VIP client is swept away by criminals in a white van. For more information visit Takes real life security scenario, and demonstrates how the standard, traditional methods ...
Cмотреть видео
Cмотреть видео
HD 00:19:45
Check Point: How to Hack a Cell Phone | Demo for Understanding Mobile Security
Want to hack a Smartphone? A hands-on approach to understanding mobile security. Learn more here: Ever wanted to know how to hack a smartphone? Join this exciting live demo to see first-hand how easy it is! Learn more:
Cмотреть видео
Cмотреть видео
HD 00:27:48
Check Point: New Cyber Security Technologies and Cyber Threat Solutions
is your partner against cyber-crime. This is realized on a daily basis by thousands of customers worldwide using the most advanced cyber security technologies. More information: These technologies are part of Infinity’s cyber security a...
Cмотреть видео
Cмотреть видео
HD 00:13:39
Check Point: Hacking the Boardroom - CPX 360 2018
Cybersecurity is a boardroom discussion for enterprise corporations globally. In this fun & entertaining presentation, you will learn how to approach senior executive for an effective discussion on Cybersecurity & how the Internet of Everyt...
Cмотреть видео
Cмотреть видео
HD 00:18:01
Check Point: How to Hack a Smartphone - Demo with Pablo Perez CPX 360
Ever wanted to know how to hack a smartphone? Join this exciting live demo to see first-hand how easy it is. For more information visit In this session, Michael Shaulov will demonstrate a live hacking of a smartphone. After the demonstrat...
Cмотреть видео
Cмотреть видео
HD 00:34:55
Check Point: Gil Shwed Keynote: Stepping Up to Gen V of Cyber Security
Gil Shwed's keynote from CPX 2018 on the future of Cyber Security. Find out what Gen V Cyber Attacks are and how you can prevent the next Cyber Attack. For more information visit -
Cмотреть видео
Cмотреть видео
HD 00:19:44
Check Point: Cloud Security - VMware & CloudGuard - CPX 360 2018
Businesses that use the public cloud are vulnerable to cyber threats. Learn how to close the security gaps in the cloud. Public and hybrid cloud adoption is exploding among enterprises, but so are cloud hacks and breaches. Cloud asset...
Cмотреть видео
Cмотреть видео
HD 00:20:00
Check Point: Cloud Security Challenges by Peter Sandkuijl - CPX 360 2018
Public and hybrid cloud adoption is exploding among enterprises, but so are cloud hacks and breaches. Cloud assets are at risk from the same types of threats targeting physical networks. What's more, cyber criminals are using increasingly...
Cмотреть видео
Cмотреть видео
HD 00:21:37
Check Point: Artificial Intelligence: a Silver Bullet in Cyber Security? CPX 360 Keynote
Artificial Intelligence is the Industrial Revolution of our time. It is already reshaping our world and is likely to transform practically every facet of our human lives. Learn more here: Fighting cybercrime is one of its many application...
Cмотреть видео
Cмотреть видео
HD 00:05:18
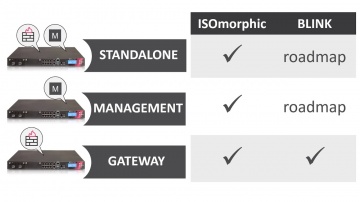
Check Point: Deployment Tools - ISOmorphic & Blink
Deploying Next Generation Firewalls just got easier with the introduction of the Blink utility. For more information: Blink creates a working snapshot of a cleanly installed security gateway with a completed First-Time Configuration Wizard...
Cмотреть видео
Cмотреть видео
HD 00:03:09
Check Point: Happy International Women's Day 2018
The women of share the best advice they ever received in recognition of International Women's Day 2018. Learn more about at
Cмотреть видео
Cмотреть видео
HD 00:02:19
Check Point: The Mississippi Secretary of State & CTO Prevents Ransomware
For more information visit Seeking to modernize its security infrastructure, the Mississippi Secretary of State upgraded to SandBlast and now prevents ransomware attacks and enjoys a peace of mind.
Cмотреть видео
Cмотреть видео
HD 00:03:55
Check Point: Deploy Small Business Appliances with the Zero Touch Cloud Service
Watch our overview of the Zero Touch Cloud Service to see how you can save valuable time in the initial deployment of our small business security appliances. For more information:
Cмотреть видео
Cмотреть видео
HD 00:06:37
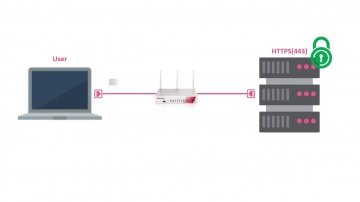
Check Point: HTTPS Inspection on Small Business Appliances
Watch our tutorial on how to enable HTTPS inspection on our 700 Appliance to improve your small business security. More information:
Cмотреть видео
Cмотреть видео
HD 00:06:01
Check Point: Advanced Cyber Security for 2018 - Cyber Security Demo
This video is a technical demonstration of what the cyber security architecture of the future is all about. For more information visit: Infinity is the first consolidated cyber security across networks, cloud and mobile. Unlike other so...
Cмотреть видео
Cмотреть видео
HD 00:26:45
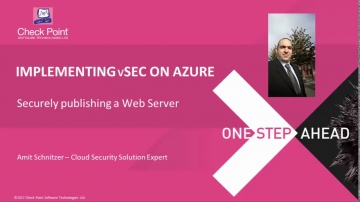
Check Point: Step-By-Step Guide for Securing a Web Server on Azure using CloudGuard IaaS (prev. vSE
Learn to create and deploy a web server on top of Azure public cloud and to securely publish it through a vSEC standalone server. More information:
Cмотреть видео
Cмотреть видео
HD 00:09:10
Check Point: Software’s vSEC Cloud Security featured in Globb TV Interview at VMWorld 2017
More information: Itai Greenberg, Head of Cloud Security at Software Technologies, describes how ’s vSEC Cloud Security protects workloads in public clouds like AWS, private clouds like VMware SDDC ( using NSX ) and hybrid clouds built u...
Cмотреть видео
Cмотреть видео
HD 00:01:56
Check Point: Defeats Mobile Cyberattacks
Advanced cybercrimes aren’t science fiction; they’re real – and have real consequences. is at the forefront of mobile security, ensuring that devices and data everywhere remain safe. We don’t just build cutting edge technology: we stand be...
Cмотреть видео
Cмотреть видео
HD 00:02:24
Check Point: SandBlast Mobile: How It Works
Accurate threat detection is a critical component of preventing advanced attacks on smartphones and tablets. Traditional mobile anti-virus, signature-based solutions identify known threats, but they can't detect zero-day malware or apps tha...
Cмотреть видео
Cмотреть видео
HD 00:02:10
Check Point: SandBlast Mobile: Protecting Against Malicious Apps
Our mobile devices are used for both personal and business purposes. Installing new apps may compromise both your private and corporate data. Every year, malicious apps downloaded from official app stores infect millions of mobile devices....
Cмотреть видео
Cмотреть видео
HD 00:02:05
Check Point: Secure your Mobile Phone Now | Introducing SandBlast Mobile
Protecting your enterprise from mobile threats and cyber attacks. More information: Worried about your Mobile Privacy? Secure your mobile phone now against mobile threats. Keeping your business safe from cyberattacks is no easy task, and...
Cмотреть видео
Cмотреть видео
HD 00:01:15
Check Point: Advanced Cyber Attack Business Protection
SandBlast mobile offers the best advanced cyber attack protection for your business. More information: Cybercriminals are better than ever at stealing sensitive information from your smartphone or tablet. Whether it's personal information...
Cмотреть видео
Cмотреть видео
HD 00:08:41
Check Point: 's Avi Rembaum: Shedding Light on the Dark Web
Leveraging intelligence culled from the Dark Web will help boost information security for enterprises, says Avi Rembaum of Software Technologies. "What's really becoming far more important is leveraging the intelligence coming from that r...
Cмотреть видео
Cмотреть видео
HD 00:14:26
Check Point: Protect Your Mobile Workforce with SandBlast Mobile & Microsoft Intune
Videos in this Series: Part 1 - Preparing Microsoft Intune for Integration with SandBlast Mobile Part 2 - Configuring Integration between SandBlast Mobile and Microsoft Intune Part 3 - Testing Integration Part 4 - Solution Overview and Star...
Cмотреть видео
Cмотреть видео
HD 00:10:15
Check Point: Protecting Your Mobile Workforce with SandBlast Mobile & Microsoft Intune Pt.1
Videos in this Series: Part 1 - Preparing Microsoft Intune for Integration with SandBlast Mobile Part 2 - Configuring Integration between SandBlast Mobile and Microsoft Intune Part 3 - Testing Integration Part 4 - Solution Overview and Star...
Cмотреть видео
Cмотреть видео
HD 00:02:22
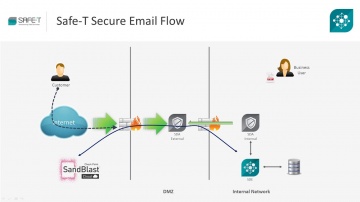
Check Point: Securing Data Exchange with SandBlast and Safe-T HDS
Organizations today face host of challenges in securing high risk data. SandBlast is most advanced protection against zero-day malware threats, while Safe-T HDS secures all data exchange scenarios including human data exchange such as secu...
Cмотреть видео
Cмотреть видео
HD 00:08:53
Check Point: CyberTalk: Conversations on the Cloud with ESG's Jon Oltsik | Cloud Security | CyberTal
To learn more about cybersecurity trends and challenges, check out An informal conversation between ESG principal analyst Jon Oltsik and 's Don Meyer, focused on cloud security: what to watch out for, how to secure against data breaches, ...
Cмотреть видео
Cмотреть видео
HD 00:03:33
Check Point: Continuing Policy Work-in-Progress with R80.10 Session Take Over | Tech Bytes
R80.10 enables security administrators to work on the same policy at the same time. But what happens if a project needs to be finished and the security administrator is not available to do so? R80.10 Session Take Over feature allows for oth...
Cмотреть видео
Cмотреть видео
HD 00:03:13
Check Point: Managing Security Policy Changes with R80.10 | Tech Bytes
When new services are introduced and your security policy needs to be adjusted accordingly, what tools will you be using? R80.10 makes it easier to implement changes. The “Where Used” and “Replace” tools will help security administrators ma...
Cмотреть видео
Cмотреть видео