Поиск по тегу «vsec» в разделе Видеокаталог
HD 00:01:48
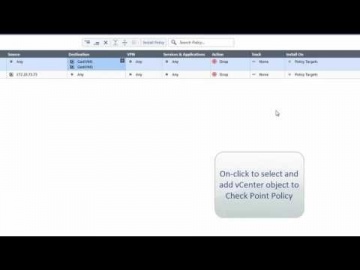
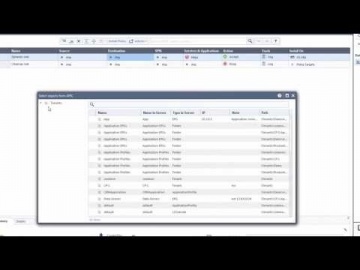
Check Point: vSEC controller Demo with R80 Smart Management | Cloud Security
This video demos the vSEC cloud security integration with VMware vCenter and NSX. It shows you how to integrate a vCenter server in the Smart Console, provision a security rule based on imported vCenter objects like VM name, integrate wit...
Cмотреть видео
Cмотреть видео
HD 00:02:09
Check Point: SmartConsole Integration with Cisco ACI | Private Cloud Networks
vSEC for Cisco ACI securely enables the rapid deployment of applications in private cloud networks. The integration with CiscoÛªs APIC Controller lowers the time it takes to create and update security policies from minutes to seconds, allo...
Cмотреть видео
Cмотреть видео
HD 00:02:24
Check Point: Partner Success Story - RoundTower on vSEC Solution | Cloud Security
For More Information: ... Partner Round Tower shares a vSEC success story highlighting the features and benefits of vSEC for VMware NSX advanced security for the Software-Defined Data Center. vSEC integration with VMware NSX delivers dyn...
Cмотреть видео
Cмотреть видео
HD 00:01:15
Check Point: 11. Troubleshooting
This video demonstrates how to verify that traffic is redirected and inspected by vSEC gateways.
Cмотреть видео
Cмотреть видео
HD 00:02:28
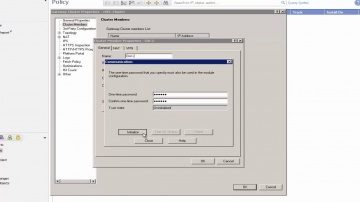
Check Point: 09 Creating vSEC Cluster Objects
Create a cluster object, with vSEC Gateway members. Each gateway will automatically get the license attached to the cluster.
Cмотреть видео
Cмотреть видео
HD 00:44:57
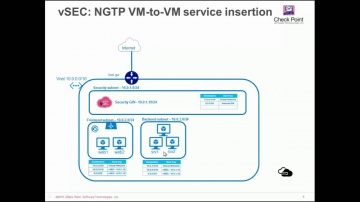
Check Point: vSEC for Microsoft Azure Hybrid Cloud : Deployment Scenarios and Demo
Cloud Security Architect provides overview of deployment scenarios, use cases and demos vSEC for Microsoft Azure for Hybrid Cloud.
Cмотреть видео
Cмотреть видео
HD 00:01:51
Check Point: 08 Creating Security Group and IP Sets
Software Technologies Ltd. — крупнейший в мире поставщик в области безопасности. Компания предлагает покупателям ведущие в индустрии решения и защищает покупателей от кибератак с непревзойденным уровнем успешного обнаружения вре...
Cмотреть видео
Cмотреть видео
HD 00:01:32
Check Point: 07 Deploying the Service
This procedure uses an Agent VM, for an environment with a local Datastore. If you will use an external Datastore, have its details ready before you begin.
Cмотреть видео
Cмотреть видео
HD 00:00:47
Check Point: 06 Creating a vSEC Gateway IP Address Pool
We recommend that you create pool for automatic assignment of management interface IP addresses.
Cмотреть видео
Cмотреть видео
HD 00:02:15
Check Point: 05 Registering a vSEC Gateway Service and Host Preparation
Software Technologies Ltd. — крупнейший в мире поставщик в области безопасности. Компания предлагает покупателям ведущие в индустрии решения и защищает покупателей от кибератак с непревзойденным уровнем успешного обнаружения вре...
Cмотреть видео
Cмотреть видео
HD 00:01:41
Check Point: 04 Installing the OVF Package and Configuring Global Parameters
Software Technologies Ltd. — крупнейший в мире поставщик в области безопасности. Компания предлагает покупателям ведущие в индустрии решения и защищает покупателей от кибератак с непревзойденным уровнем успешного обнаружения вре...
Cмотреть видео
Cмотреть видео
HD 00:00:37
Check Point: 03 Adding the vCenter IP Address to the Runtime Settings
VMware requires you to add the vCenter IP address to the Runtime Settings tab on the vCenter Server Setting page
Cмотреть видео
Cмотреть видео
HD 00:01:00
Check Point: 02 Configuring Agent VM
To use a local Datastore on multiple ESX hosts (recommended) for the vSEC Gateway, or to use a non-distributed vSwitch for vSEC Gateway communication to the Security Management Server, you must configure Agent VM settings
Cмотреть видео
Cмотреть видео
HD 00:00:54
Check Point: 01 Installing the Management Server Hotfix
Install the Hotfix on Gaia R77.30 Security Management Server and R77.20/R77.30 Security Gateways. It is required for both the vSEC Gateway and the vSEC Controller.
Cмотреть видео
Cмотреть видео
HD 00:02:44
Check Point: and VMware Partnership delivers advanced security for the SDDC | Cloud Security
More Information: VMware and Partnership delivers advanced security for the Software-Defined Data Center. vSEC integration with VMware NSX delivers dynamic orchestration of advanced threat prevention for all traffic in the Software-Def...
Cмотреть видео
Cмотреть видео
00:02:08
Check Point: Customer Success Video: Helvetia Insurance, vSEC for VMware NSX | Cloud Security
For over 150 years, Helvetia has grown into a successful international insurance group with a wide range of services. Andreas Hagin, Head of Corporate Network & Unified Communication Engineering at Helvetia, discusses the importance of ...
Cмотреть видео
Cмотреть видео
HD 00:02:29
Check Point: 24/7 Protection with ThreatCloud Managed Security Service | Threat Prevention
For more information visit ThreatCloud Managed Security Service is a cloud-based service providing actionable attack alerts for IPS, Anti-Bot and Antivirus customers. experts remotely monitor, manage and escalate attack incidents. Custo...
Cмотреть видео
Cмотреть видео
HD 00:02:57
Check Point: vSEC Advanced Security for Software-Defined Data Centers | Cloud Security
For more information visit: vSEC integration with VMware NSX delivers dynamic orchestration of advanced threat prevention for all traffic in the Software-Defined Data Center. Learn more
Cмотреть видео
Cмотреть видео
HD 00:01:46
Check Point: Introducing ThreatCloud Emulation Services | Cloud Security
Learn More: Find Zero-Day Threats before they find you with ThreatCloud Emulation Services.
Cмотреть видео
Cмотреть видео
HD 00:04:08
Check Point: ThreatCloud | Complete Cyber Security Intelligence Infrastructure | Network Security
For more information: Introducing ThreatCloud, the first collaborative network to fight cyber-attacks.
Cмотреть видео
Cмотреть видео
HD 00:03:59
Check Point: DDoS Protector - Technical Overview | DDoS Protection
's new Threat Emulation Software Blade prevents infections from undiscovered exploits, zero-day and targeted attacks. For more information: This innovative solution quickly inspects suspicious files, emulates how they run to discover mali...
Cмотреть видео
Cмотреть видео