itbion.ru / Видео / По комментариям
Как использовать онлайн-кассу интернет-магазину: популярные вопросы о ФЗ-54
Подробнее о 54-ФЗ: Директор по развитию бизнеса фискальных решений компании АТОЛ Юлия Русинова отвечает на популярные вопросы о ФЗ-54 эксклюзивно для Эвотор.Для интернет магазинов есть определенная специфика, как они применяют контрольно-ка...
Cмотреть видео
Cмотреть видео
Как люди привыкают к технологиям: «Коля, я не с женой пришел. Можешь камеры в ресторане отключить?
Руководитель Gadget Studio Николай Турубар о том, как люди привыкают к технологиям
Cмотреть видео
Cмотреть видео
"1С:Предприятие 8 через интернет" c 1С:Модем
Решение для быстрого доступа к программам 1С через Интернет.
Cмотреть видео
Cмотреть видео
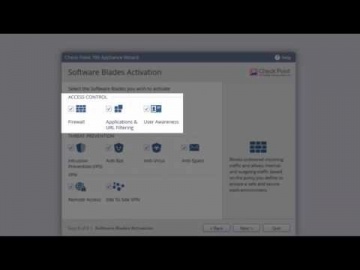
Check Point: 700 Appliance Setup | SMB Cyber Security
For more information: Watch our tutorial on how to setup our 700 Appliance, 's latest addition to the product family to protect small businesses against the latest cyber threats.
Cмотреть видео
Cмотреть видео
Check Point: Advanced Cyber Security for 2018 - Cyber Security Demo
This video is a technical demonstration of what the cyber security architecture of the future is all about. For more information visit: Infinity is the first consolidated cyber security across networks, cloud and mobile. Unlike other so...
Cмотреть видео
Cмотреть видео
Check Point: Advanced Cyber Security for 2018 | Infinity
Learn more at Introducing Infinity, the world’s most advanced cyber security and management architecture. Infinity consolidates security across network, cloud and mobile, keeping you secured from known and unknown threats, today and in ...
Cмотреть видео
Cмотреть видео
Check Point: CheckMates First Birthday Award Winners
CheckMates, the user community for customers and partners, is celebrating it's first birthday by recognizing excellent contributors and content!
Cмотреть видео
Cмотреть видео
Check Point: Optimizes Security with Gigamon’s Full Network Visibility
and Gigamon’s joint solution provides comprehensive network visibility, optimal performance and advanced threat prevention capabilities. For more information:
Cмотреть видео
Cмотреть видео
Check Point: Advanced Cyber Security for 2018 | Infinity | Technical Deep Dive with Jeff Schwartz
Infinity is the first consolidated security across networks, cloud, and mobile, providing the highest level of threat prevention against both known and unknown targeted attacks to keep you protected now and in the future. Jeff Schwartz, our...
Cмотреть видео
Cмотреть видео
Check Point: Lightboard Series: Dynamic Revisions
This video elaborates on the logic behind the R80.10 Security Management architecture focusing on the dynamic revisions feature. This feature automatically stores the full history of database changes, with very little footprint, consuming ...
Cмотреть видео
Cмотреть видео
Check Point: Infinity | The Cyber Security Architecture of the Future
Gabi Reish - VP, Product Management and Product Marketing, Software For more information on the Cyber Security Architecture of the Future, please go to:
Cмотреть видео
Cмотреть видео
Check Point: Compliance Software Blade - Regulatory Compliance
For more information: This is the third video in the Compliance Software Blade Demonstration Series. See how the Compliance Software Blade can help you easily review your regulatory compliance status, and quickly prepare detailed reports ...
Cмотреть видео
Cмотреть видео
Check Point: Cloud Security: Safe Journey to the Cloud
The era of cloud is upon us; firms of all sizes and in all walks of life are looking to leverage the agility and elasticity of cloud. For more information visit: But cloud carries a totally new and unique set of security challenges. In th...
Cмотреть видео
Cмотреть видео
Check Point: and Tufin: Security Management for the Future | Enterprise Network Security
and Tufin provide complete, simplified and automated security management for the enterprise network of the future. For more information: Together, the Tufin Orchestration Suite with Firewalls and Security Management products provide ad...
Cмотреть видео
Cмотреть видео
Check Point: Gil Shwed Awarded 2018 Israel Prize For Technology & Innovation
Credit to Israeli Broadcasting Service, Kann News 2018 Gil Shwed CEO of software was recently awarded the Israel Prize for Technology & Innovation. The video shows Gil Shwed accepting the award and also details Gil Shwed's journey as an e...
Cмотреть видео
Cмотреть видео
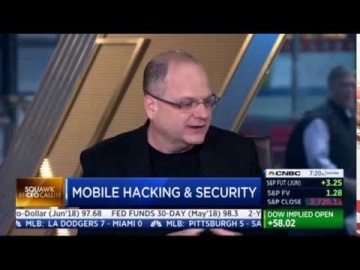
Check Point: Founder & CEO Gil Shwed on CNBC Squawk Box
CNBC Squawk Box featured Check Point CEO & Founder Gil Shwed. Gil Shwed discusses 5th generation cyber attacks. For more https://www.checkpoint.com/gen-v-cybe...Talking about level three attacks, level four attacks; what are fifth and s...
Cмотреть видео
Cмотреть видео
Check Point: Choosing the right endpoint security solution
For more information: Fred Borjesson regional endpoint sales manager at Software Technologies discusses the best ways for enterprises to manage their endpoint security and explains the benefit of using one unique single endpoint security...
Cмотреть видео
Cмотреть видео
Check Point: Advanced Endpoint Protection & Forensics | Advanced Threat Prevention
Continuously preventing even the most sophisticated cyber attacks and responding quickly to limit damages on endpoint devices is essential to all businesses today. More information: The SandBlast Agent extends Ûªs industry-leading zero-...
Cмотреть видео
Cмотреть видео
Check Point: IPS Software Blade
SSL Certificates attacks can compromise even the most secure sites. Learn how s IPS solutions protect against this specific kind of threats.
Cмотреть видео
Cмотреть видео
Check Point: vSEC, The Future of Cloud Security
In this video, you’ll hear from Donald Meyer, Head of Marketing, Data Center and Cloud, where he discusses issues surrounding Cloud security and how organizations can better protect themselves from vulnerabilities in the Cloud. For more in...
Cмотреть видео
Cмотреть видео
Check Point: Hamas’ Cyber Tactics Exposed - Attacking IDF Soldier’s Mobile Phones
The Israeli Defense Forde uncovered a Hamas network that reached out to IDF soldiers online, sometimes in romantic ways, and ask them to download applications that would infect them with Trojan horse viruses. The applications used by Hamas ...
Cмотреть видео
Cмотреть видео
Check Point: Makes DLP Work | Data Loss Prevention
's new DLP Software Blade combines innovative technology with a unique approach that blocks intentional and unintentional data breaches and educates employees in the process to help prevent future incidents. Watch this video to see how...
Cмотреть видео
Cмотреть видео
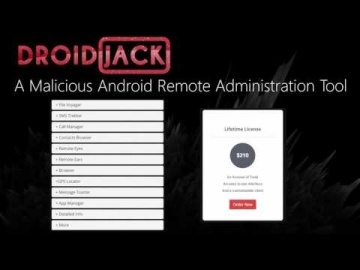
Check Point: Viking Horde: A New Type of Android Malware on Google Play | Mobile Security
Blog: More information: The research team uncovered a new Android malware campaign on Google Play it calls Viking Horde. Viking Horde conducts ad fraud, but can also be used for other attack purposes such as DDoS attacks, spam messages...
Cмотреть видео
Cмотреть видео
Check Point: Anti-Ransomware: Tecnología y Demostración
Anti-Ransomware protege contra el ransomware de día cero. Está incluido en el paquete de SandBlast Agent. Este video presenta la descripción de la solución seguido por una demonstración. Anti-Ransomware usa las habilidades del análisis for...
Cмотреть видео
Cмотреть видео
Check Point: Pokemon GO Repackaged Malware Demonstration | SandBlast Mobile Security Demo
The excitement over the new game Pokemon GO has taken the world by storm. Because it's available only in limited countries right now, some people may be tempted to download the app from sources other than Google Play or the Apple App Store....
Cмотреть видео
Cмотреть видео
Check Point: Threat Emulation Protects Investment Firm: Gimv
Learn More: Gimv, a leading European private equity and venture capital investment company, leverages ThreatCloud Emulation technology to prevent against zero day attacks. Watch as IT Manager Kristof Poppe discusses his experience wi...
Cмотреть видео
Cмотреть видео
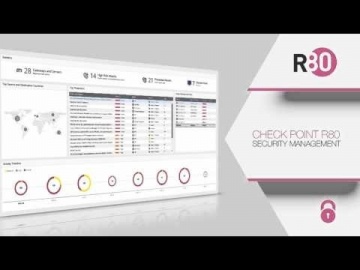
Check Point: R80 Security Management | Advanced Threat Prevention
's R80 Security Management helps you consolidate security functions so you can be more efficient and effective at deploying the strongest protections across your organization. More Information:
Cмотреть видео
Cмотреть видео
Check Point: 600 Security Appliance: One Box, Complete Protection | SMB Cyber Security
Learn more about the 600 appliance: The 600 provides a complete security package with firewall, VPN, antivirus, intrusion prevention and more, at a price your small business can afford.
Cмотреть видео
Cмотреть видео
Check Point: Use R80.10 New Packet Mode Feature to Search Through Policy
Packet Mode, a new feature introduced within R80.10, enables you to search the rule base as if it were a packet going through the security policy. For more information visit: R80.10 features the most advanced threat prevention across netw...
Cмотреть видео
Cмотреть видео
Check Point: DressCode Android Malware Discovered on Google Play | SandBlast Mobile Security | Andro
The mobile threat prevention research team discovered a new Android malware on Google Play, called DressCode, which was embedded into more than 40 apps, and found in more than 400 additional apps on third party app stores. notified Google...
Cмотреть видео
Cмотреть видео