Check Point: SandBlast Mobile Security: Man-in-the-Middle Mobile Attacks, Check Point: Mobile Security HD

00:01:32
Check Point Software Technologies, Ltd. 360 роликов
8085 просмотров на сайте 12n.ru
SandBlast Mobile Security: Man-in-the-Middle Mobile Attacks.
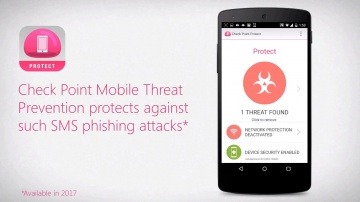
Our mobile devices are more vulnerable then we think. A man-in-the middle attack is a potential threat every time you connect to a Wi-Fi network. For more information: Imagine you are at a coffee shop and you want to connect to Wi-Fi and check your email. Once connected, you may be asked to download a configuration profile to get internet access. At this moment the man-in-the middle attacker gets to work. Without your knowledge, you are now connected to the internet via the attackers access point. He now has complete visibility and access to everything you are doing on your mobile device. For example, the attacker can capture credentials to highly sensitive business applications or access and download confidential documents stored in file sharing applications Mobile Threat Prevention can protect against these types of attacks, before they even start. When trying to connect to a compromised network, Mobile Threat Prevention alerts you of the malicious activity. Once you disconnect from the compromised Wi-Fi network, the device is no longer at risk and safe for use. Administrators have complete visibility into all incidents throughout their organization using the Mobile Threat Prevention management console. Stay one step ahead with.
развернуть свернуть