Поиск по тегу «product solutions» в разделе Видеокаталог
HD 01:01:35
Check Point: EU GDPR Webinar Replay
The European Union’s General Data Protection Regulation (‘GDPR’) poses the biggest change to the regulatory landscape of data privacy. To learn more visit: GDPR places significant policy and technical responsibilities on ANY organization ...
Cмотреть видео
Cмотреть видео
HD 00:05:18
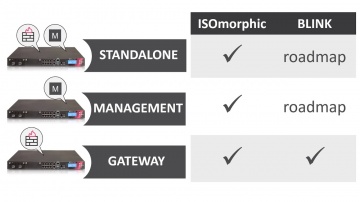
Check Point: Deployment Tools - ISOmorphic & Blink
Deploying Next Generation Firewalls just got easier with the introduction of the Blink utility. For more information: Blink creates a working snapshot of a cleanly installed security gateway with a completed First-Time Configuration Wizard...
Cмотреть видео
Cмотреть видео
HD 00:04:12
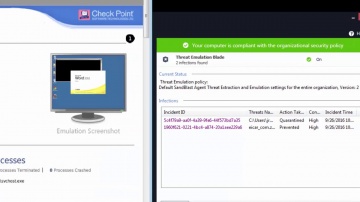
Check Point: SandBlast Agent Protects From Advanced Zero-day Malware
What happens if employees roam outside enterprise network that protect them from advanced zero-day invasions? For more information: SandBlast Agent protects the enterprise end-points from advanced zero-day malware, by using advanced C-P-U...
Cмотреть видео
Cмотреть видео
HD 00:03:15
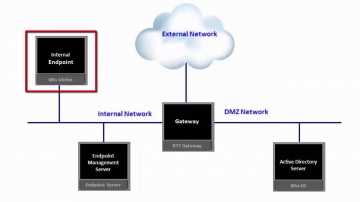
Check Point: Installing SandBlast Agent on the Enterprise Endpoint
This video provides an overview of recommended process for deployment of SandBlast Agent on the Enterprise Endpoints. SandBlast Agent defends endpoints with a complete set of real-time advanced endpoint protection technologies, including T...
Cмотреть видео
Cмотреть видео
HD 00:04:03
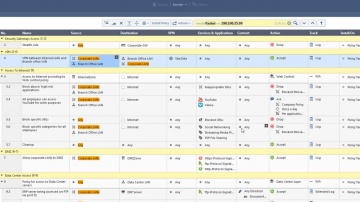
Check Point: Use R80.10 New Packet Mode Feature to Search Through Policy
Packet Mode, a new feature introduced within R80.10, enables you to search the rule base as if it were a packet going through the security policy. For more information visit: R80.10 features the most advanced threat prevention across netw...
Cмотреть видео
Cмотреть видео
HD 00:18:47
Check Point: Gil Shwed & Marius Nacht Interview - Milan 2017
Gil Shwed & Marius Nacht discuss product innovation and the Experience over the years. For more information:
Cмотреть видео
Cмотреть видео
HD 00:17:56
Check Point: Hacking the Smartphone | Mobile Cyber Hack Demonstration
Live demonstration of a smartphone hack, from Experience 2017. For more information visit: Watch Michael Shaulov, Head of Mobility Products at Software hack a smart phone in real time. Today every business is a mobile business, with req...
Cмотреть видео
Cмотреть видео
HD 00:18:41
Check Point: Cloud Security: Safe Journey to the Cloud
The era of cloud is upon us; firms of all sizes and in all walks of life are looking to leverage the agility and elasticity of cloud. For more information visit: But cloud carries a totally new and unique set of security challenges. In th...
Cмотреть видео
Cмотреть видео
00:19:02
Check Point: Evolving Role of the CISO - A Customer Story
In this session, CISO Joey Smith will discuss his understanding of the importance of compliance and security and their differences. For more information: Additionally, he will review what he has personally learned from his experience as...
Cмотреть видео
Cмотреть видео
HD 00:04:32
Check Point: R80.10 Security Management | Tech Bytes: Gateways, Logs, and Manage & Settings
This video is an overview that describes important features and functionality of the R80.10 SmartConsole. More information: To learn more about R80.10 Security Management: Infinity is the only fully consolidated cyber security architec...
Cмотреть видео
Cмотреть видео
HD 00:04:01
Check Point: Tutorial: Configuring Application Control
How to use R80 SmartConsole to get started with the Application Control, URL Filtering Software Blades, and URL Filtering Settings with R80 Security Management. For more information: Infinity, the first consolidated security across net...
Cмотреть видео
Cмотреть видео
HD 00:05:44
Check Point: Security Demo for Industrial Control Systems
This video demonstrates how is deployed to protect and secure your operational network. For more information, please visit: In the centralized management center (called the SmartCenter), rules or security policies are created and pushed ...
Cмотреть видео
Cмотреть видео
HD 00:54:57
Check Point: Understanding SandBlast - Zero-Day Protection
Understanding your exposure to threats—and what you can do about it is not only responsible business management—it’s critical to business survival. More information: Turn Security into an Enabler, Not a Disabler. SandBlast Zero-Day Prote...
Cмотреть видео
Cмотреть видео
HD 00:02:45
Check Point: SandBlast Zero-Day Protection | Advanced Threat Prevention
Learn how to take the first steps to enable your security gateway to leverage the SandBlast Cloud Service or the SandBlast Appliance. Learn more at: See what end users would experience, and what security administrators can expect to see. ...
Cмотреть видео
Cмотреть видео
01:03:03
Check Point: Stay One Step Ahead with SandBlast Zero-Day Protection
Watch this webcast to learn about SandBlast Zero-Day Protection, an innovative approach to stop unknown malware, zero-day and targeted attacks from infiltrating networks. More information: Zero-day protection offering network security wi...
Cмотреть видео
Cмотреть видео
HD 00:01:45
Check Point: Preventing Tomorrow's Cyber Security Threats
Increasing your enterprise security often means increasing your complexity and management challenges in kind. For more information, visit Growing complexity in security infrastructure puts a huge strain on the efficiency of the security o...
Cмотреть видео
Cмотреть видео
HD 00:01:42
Check Point: Employee Testimonial - Why work at ?
If you are passionate about innovation, dream of working with the brightest, thrive in a fast-paced, changing and challenging environment – see what we have to offer. Career opportunities: Employee, Kellmen Meghu, describes why Software ...
Cмотреть видео
Cмотреть видео
HD 00:03:07
Check Point: Customer Success: AlmavivA Group
Almaviva, Italy's number one Information & Communication Technology provider, describes how Technologies protects the organizations infrastructure.
Cмотреть видео
Cмотреть видео
HD 00:01:44
Check Point: Customer & Partner Insights- California DMV
partners with hundreds of companies across the U.S. and internationally to form long-term business and person relationships. To learn more: speaks with customers and partners at RSA Conference 2014 in San Francisco. Watch as they share w...
Cмотреть видео
Cмотреть видео
HD 00:04:19
Check Point: SMB Cyber Security - 600 Appliance Setup
Small businesses need cost-effective security that provides robust protections and ease of use. For more information: brings its long-standing history of security expertise to a range of solutions optimized for the unique demands of smal...
Cмотреть видео
Cмотреть видео
HD 00:05:30
Check Point: Denial of Service Cyber Attack Protector Overview
DDoS Protector™Appliances block Denial of Service attacks within seconds with multi-layered protection and up to 40 Gbps of performance. For more information: Modern DDoS attacks use new techniques to exploit areas where traditional secu...
Cмотреть видео
Cмотреть видео
HD 00:02:08
Check Point: 2013 Security Report | Cyber Security
Based on research of nearly 900 companies and 120,000 hours of monitored traffic, the 2013 Security Report reveals major security risks organizations are exposed to on a daily basis. For information: Most importantly, the report provides...
Cмотреть видео
Cмотреть видео
00:05:02
Check Point: on National Czech Republic Television
Eurograbber was launched against banking customers, using a sophisticated combination of malware directed at computers and mobile devices. For more information click here: The malware, in conjunction with the attackers' command and contr...
Cмотреть видео
Cмотреть видео
HD 00:04:43
Check Point: Next-Generation Secure Web Gateway | Network Security
Learn More: Are you trying to secure Web 2.0 with 1.0 tools? The Web has evolved, threats have evolved, so should your Web Security! In this video, learn how to best protect against today's web-borne malware and help businesses to get th...
Cмотреть видео
Cмотреть видео
HD 00:14:29
Check Point: Radio Interview Discussing 2013 Cyber Security Threats
Kellman Meghu, Head of Security Engineering at speaks to The Biggs Radio Show about what cyber security threats we should look out for in 2013
Cмотреть видео
Cмотреть видео
HD 00:04:05
Check Point: Denial of Service Attacks & How to Protect Against Them
DDoS Protector™Appliances block Denial of Service attacks within seconds with multi-layered protection and up to 40 Gbps of performance. For more information: Alon Kantor, Corporate Development Architect at talks about the threat of dist...
Cмотреть видео
Cмотреть видео
HD 00:06:47
Check Point: Unveils New Network Security Appliance Models
Gabi Reish, Head of Product Management at Software Technologies, introduces the new 2012 line of Appliances. For more information: provides organizations of all sizes with the latest data and network security protection in an integrated...
Cмотреть видео
Cмотреть видео
HD 00:03:18
Check Point: Advanced Network Security: New Anti-Bot Software Blade
Infinity is the first consolidated security across networks, cloud and mobile, providing the highest level of threat prevention. More information: provides organizations of all sizes with the latest data and network security protection i...
Cмотреть видео
Cмотреть видео
00:01:45
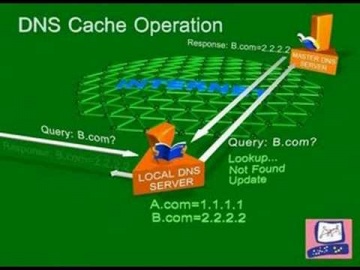
Check Point: DNS Cache Poisoning Attack | Internet Security
Software explains common DNS attacks. Learn More: DNS is the glue that holds the Internet, including web and e-mail together. A successful attack may severely impact the availability of an organization’s public facing web sites and e-mail...
Cмотреть видео
Cмотреть видео