Поиск по тегу «network» в разделе Видеокаталог
HD 00:02:53
ITGLOBAL: Quality of Service: справляемся с нагрузкой без лишних затрат - видео
Команда TechLab рассказывает о том, как функция QoS системы СКАТ DPI помогает управлять трафиком в режиме повышенной нагрузки на сеть и экономить на полосе пропускания. Сейчас, когда многие перешли на удаленную работу из дома, нагрузка на ...
Cмотреть видео
Cмотреть видео
HD 00:12:23
Транспортные сети в 5G [Лекция по 5G. Часть 18] Антон Степутин - видео
Требования к транспортные сетям мобильной связи, причины перегрузок, гибкие транспортные сети. Об этом в вебинаре Антона Степутина — кандидата технических наук, доцента СПбГУТ, корпоративного технического тренера, председателя Оргкоми...
Cмотреть видео
Cмотреть видео
HD 00:04:40
CNET: 5G explained with billiards and darts | Bridget Breaks It Down
Millimeter wave, latency, speed, density -- 5G cellular technology comes with plenty of jargon. Bridget Carey breaks it down for you in a simple way -- with bar games. Watch Bridget break down synthetic DNA as a way to store your data: L...
Cмотреть видео
Cмотреть видео
HD 00:30:26
Check Point: Who's Responsible for your Cloud Security?
A full breakdown of what is shared responsibility and the layers of security needed to protect you from security breaches in the cloud. For more information:
Cмотреть видео
Cмотреть видео
HD 00:22:22
Check Point: Building a Secure Platform as CIO - CPX 360 Keynote
In his keynote, Sharon Schusheim will discuss what it takes to build and operate a secure platform as a CIO. For more information: CPX 360 promises to be the premier cyber security summit. For the first time, we will bring our customers...
Cмотреть видео
Cмотреть видео
HD 00:06:53
Check Point: Top Cloud Cyber Security Challenges in 2018
Head of Product Marketing, Data Center and Cloud, Don Mayer, discusses some of the top cyber security challenges organizations face with the cloud in 2018. He dives into the amount of cyber attacks or cyber threats targeting the cloud and e...
Cмотреть видео
Cмотреть видео
HD 00:08:37
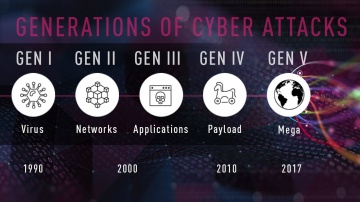
Check Point: 2018 Cyber Security - 5TH GENERATION CYBER ATTACKS
The 5th Generation of Cyber Attacks is here, is your Cyber Security ready in 2018? Darrell Burkey, Director of IPS Products interviews with WADK-AM in Newport/ Providence areas in Rhode Island on Gen V cyber security. Visit - to learn more ...
Cмотреть видео
Cмотреть видео
HD 00:02:44
Check Point: CloudGuard SaaS Demo Series: Protecting Sensitive Data
For more information: Watch this short demonstration video to learn how CloudGuard SaaS, an industry-first software-as-a-service (SaaS) security solution, provides advanced security and sensitive data protection for SaaS applications such ...
Cмотреть видео
Cмотреть видео
HD 00:05:12
Check Point: Deployment Tools; DIY security appliance images using ISOmorphic
Deployment Tools; DIY security appliance images using ISOmorphic. For more information: In our second video on deployment tools we show you how to image Security Appliances and Open Servers. With the ISOmorphic utility you can inst...
Cмотреть видео
Cмотреть видео
HD 00:19:44
Check Point: Cloud Security - VMware & CloudGuard - CPX 360 2018
Businesses that use the public cloud are vulnerable to cyber threats. Learn how to close the security gaps in the cloud. Public and hybrid cloud adoption is exploding among enterprises, but so are cloud hacks and breaches. Cloud asset...
Cмотреть видео
Cмотреть видео
HD 00:50:38
Check Point: Advanced Cyber Security for 2018 | Introducing 3 New products: Step into Gen-V of Cyber
For more information: is happy to welcome the 5th Generation of Cyber Security with 3 exciting new offerings: Infinity Total Protection (ITP), CloudGuard, and Smart-1 Security Management Appliances. • Infinity Total Protection is a gam...
Cмотреть видео
Cмотреть видео
HD 00:02:49
Check Point: Advanced Cyber Security for 2018 | Prevent Gen V Cyber Attacks with Infinity
More information: ... Infinity is the first consolidated security across networks, cloud and mobile, providing the highest level of threat prevention against both known and unknown targeted attacks to keep you protected now and in the fut...
Cмотреть видео
Cмотреть видео
HD 00:01:54
Check Point: Advanced Cyber Security for 2018 | Prevent 5th Generation Cyber Attacks with Infinity
More information: Infinity is the first consolidated security across networks, cloud and mobile, providing the highest level of threat prevention against both known and unknown targeted attacks to keep you protected now and in the future...
Cмотреть видео
Cмотреть видео
HD 00:17:04
Check Point: Advanced Cyber Security for 2018 | Infinity | Technical Deep Dive with Jeff Schwartz
Infinity is the first consolidated security across networks, cloud, and mobile, providing the highest level of threat prevention against both known and unknown targeted attacks to keep you protected now and in the future. Jeff Schwartz, our...
Cмотреть видео
Cмотреть видео
HD 00:06:01
Check Point: Advanced Cyber Security for 2018 - Cyber Security Demo
This video is a technical demonstration of what the cyber security architecture of the future is all about. For more information visit: Infinity is the first consolidated cyber security across networks, cloud and mobile. Unlike other so...
Cмотреть видео
Cмотреть видео
HD 00:01:06
Всё под контролем - PRTG Network Monitor
PRTG Network Monitor отслеживает работу всех систем, устройств, приложений и трафика вашей IT-инфраструктуры Следите за вашей сетью и получайте уведомления в режиме онлайн на любые устройства (планшет, см...
Cмотреть видео
Cмотреть видео
HD 00:01:12
Предупрежден, значит вооружен - PRTG Network Monitor
PRTG Network Monitor. Защитите свою систему от поломок, сбоев и хакерских атак уже сегодня при помощи программы PAESSLER -
Cмотреть видео
Cмотреть видео
HD 00:03:02
Check Point: CloudGuard (formerly vSEC) Gateway Introduction
CloudGuard (formerly vSEC) Intro to the Gateway by Greg Pepper, Data Center Security Architect. For more information: Complete Threat Prevention Security for Enterprise Clouds Cloud adoption continues to skyrocket, yet so are attacks targ...
Cмотреть видео
Cмотреть видео
HD 00:04:45
Check Point: R80.10 Policy Revision
R80.10 Policy revision explained. Learn how to work with policy revision in R80.10. For more information: R80.10 features the most advanced threat prevention across networks and cloud, managed by a single security management console. Secu...
Cмотреть видео
Cмотреть видео
HD 00:00:52
1 июня — Международный день защиты детей | REG.Holidays
Компания REG.RU поздравляет с 1 июня — Международным днём защиты детей. Наша цель — сделать .NETWORK наиболее дружелюбной и безопасной, чтобы каждый .BABY и все .ДЕТИ получали только пользу и удовольствие от работы с Интернетом,...
Cмотреть видео
Cмотреть видео
HD 00:01:55
Check Point: Optimizes Security with Gigamon’s Full Network Visibility
and Gigamon’s joint solution provides comprehensive network visibility, optimal performance and advanced threat prevention capabilities. For more information:
Cмотреть видео
Cмотреть видео
HD 00:04:01
Check Point: Tutorial: Configuring Application Control
How to use R80 SmartConsole to get started with the Application Control, URL Filtering Software Blades, and URL Filtering Settings with R80 Security Management. For more information: Infinity, the first consolidated security across net...
Cмотреть видео
Cмотреть видео
HD 00:01:34
Check Point: DressCode Android Malware Discovered on Google Play | SandBlast Mobile Security | Andro
The mobile threat prevention research team discovered a new Android malware on Google Play, called DressCode, which was embedded into more than 40 apps, and found in more than 400 additional apps on third party app stores. notified Google...
Cмотреть видео
Cмотреть видео
HD 00:02:07
Check Point: Advanced Endpoint Protection & Forensics | Advanced Threat Prevention
Continuously preventing even the most sophisticated cyber attacks and responding quickly to limit damages on endpoint devices is essential to all businesses today. More information: The SandBlast Agent extends Ûªs industry-leading zero-...
Cмотреть видео
Cмотреть видео
HD 00:01:43
Check Point: Malware Threat Prevention | Zero-Day, Zero-Second.
What can malware do in 60 seconds? One minute can change everything for a business. So what happens when the speed of business is overtaken by the speed of malware? The team devised a test to quantify that exact question. Learn More: As ...
Cмотреть видео
Cмотреть видео
HD 00:03:11
Check Point: Choose the Right Next Generation Firewall - Multi-Layer Security
Why Multi-Layer Security and how 's Software Blade Architecture is the most secure and scalable solution in this market. For more information: provides organizations of all sizes with the latest data and network security protection in a...
Cмотреть видео
Cмотреть видео
HD 00:03:11
Check Point: Choose the Right Next Generation Firewall - Multi-Layer Security
Why Multi-Layer Security and how 's Software Blade Architecture is the most secure and scalable solution in this market. For more information: provides organizations of all sizes with the latest data and network security protection in a...
Cмотреть видео
Cмотреть видео
HD 00:04:23
Check Point: SmartEvent | Security Management Walk-Through
Are you tired of managing security by manually searching through millions of logs to find the information you need? There is a better way! Watch this SmartEvent Video to learn how to manage your security more efficiently. For more informa...
Cмотреть видео
Cмотреть видео

![Транспортные сети в 5G [Лекция по 5G. Часть 18] Антон Степутин - видео](https://12n.ru/upload/video/images/small/84/c2/84c2adf6ca720e17d4d763fa4c3a640f.jpg)